Your Architecture and design considerations for secure software images are ready in this website. Architecture and design considerations for secure software are a topic that is being searched for and liked by netizens today. You can Get the Architecture and design considerations for secure software files here. Download all royalty-free vectors.
If you’re looking for architecture and design considerations for secure software pictures information related to the architecture and design considerations for secure software keyword, you have come to the ideal blog. Our site frequently gives you hints for seeing the highest quality video and picture content, please kindly search and locate more informative video articles and images that fit your interests.
Architecture And Design Considerations For Secure Software. Software design normally includes descriptions of the architecture components interfaces and other characteristics of a system or component. Standards and Architecture Considerations for Secure Hardware Design and Verification Abstract. Software architecture and practical considerations Cite as. At the beginning of any secure network design project many best practices apply more or less uniformly to all areas of the design.
 Secure Sdlc Is A Structural Concept To Integrate Security At Every Phase Of Software Development Lifecy Software Development Security Training Website Security From pinterest.com
Secure Sdlc Is A Structural Concept To Integrate Security At Every Phase Of Software Development Lifecy Software Development Security Training Website Security From pinterest.com
At the beginning of any secure network design project many best practices apply more or less uniformly to all areas of the design. Initially software architecture design considerations were taken into account during the initial phase of development as changing the software is tougher in the later stages. Youll understand how to identify and implement secure design when considering databases UML unit testing. This article by Sean Convery presents these practices in. Often COTS software with the potential for secure operation is. All rights Recipients of.
All rights Recipients of.
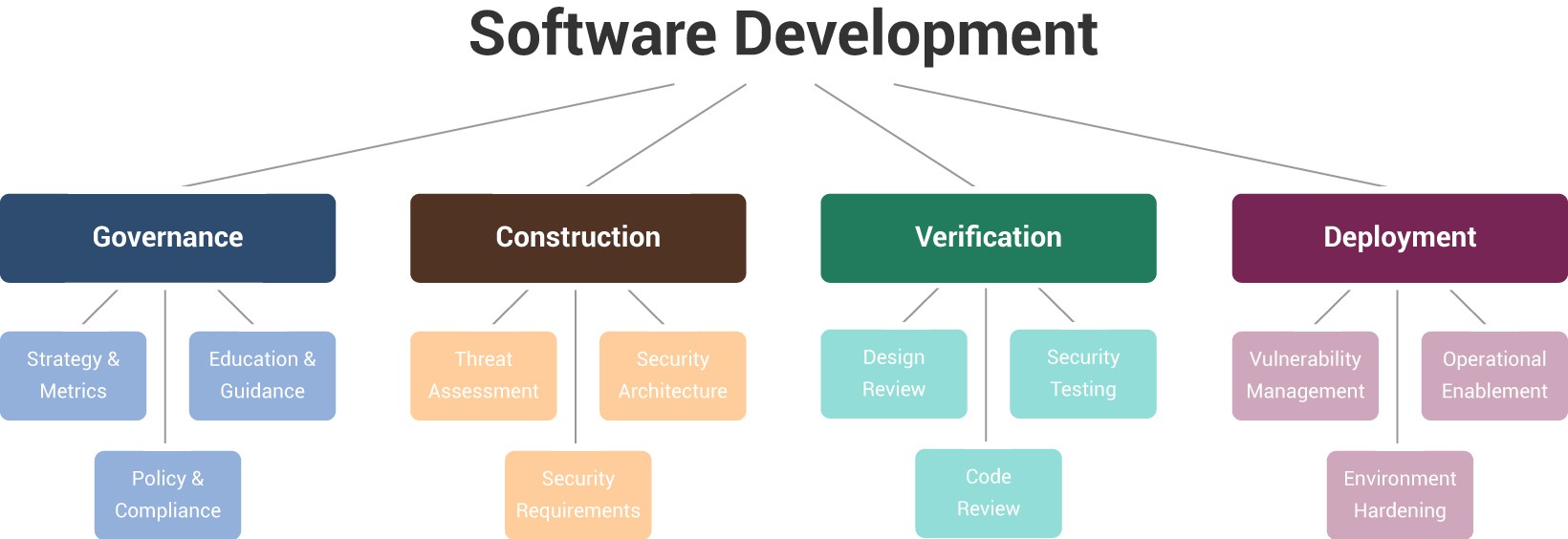
Security Design Considerations in Web Services Standards provide important authentication and message-level security services for web services but they are not a complete security solution. This article by Sean Convery presents these practices in. Security is a built-in quality attribute affecting the whole software life cycle. In fact almost 80 of organizations are9. Architecture and Design Considerations for Secure. PACS Architecture and Design Considerations Version 1806 June 2018 ONVIF 2 PACS Architecture and Design Considerations v1806 2008-2018 by ONVIF.
 Source: ptsecurity.com
Source: ptsecurity.com
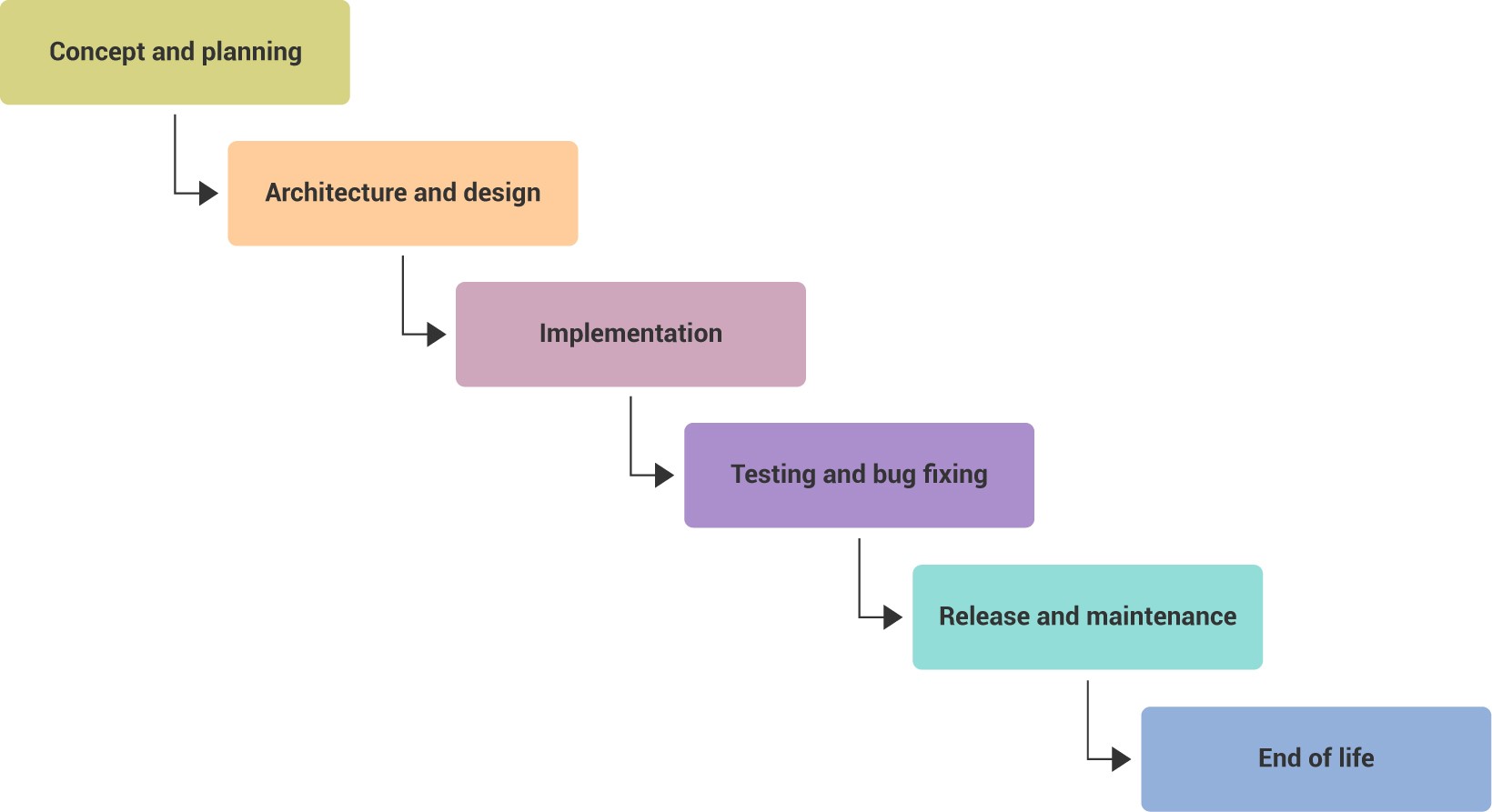
A big part of secure software architecture and design. Architecture considerations to implement secure software updates over the air By Bjoern Steurich August 03 2017 With increasing recognition that our cars are evolving into rolling data centers manufacturers. But this definition falls flat in the agile development journey where working in increments and iterations is the core criteria. Sayer and Robert Seacord and D. Architecture and Design Considerations for Secure.
 Source: docs.vmware.com
Source: docs.vmware.com
Sayer and Robert Seacord and D. The mathematical and architectural details to achieve these goals are presented and practical considerations and heuristics for using inverse design are. Standards and Architecture Considerations for Secure Hardware Design and Verification Abstract. Is understanding who might target your app. This presentation considers the foundations of secure products in particular the need for true random number sources for nonce and key generation and product compliance with standards such as FIPS 140-2 and 186-4.
 Source: docs.wso2.com
Source: docs.wso2.com
Architecture considerations to implement secure software updates over the air By Bjoern Steurich August 03 2017 With increasing recognition that our cars are evolving into rolling data centers manufacturers. Borrowing the concept of computational graphs SPINS is a design framework that emphasizes flexibility and reproducible results. Architecture and Design Considerations for Secure. But this definition falls flat in the agile development journey where working in increments and iterations is the core criteria. Svoboda and Kazuya Togashi year2011.
 Source: pinterest.com
Source: pinterest.com
The mathematical and architectural details to achieve these goals are presented and practical considerations and heuristics for using inverse design are. Security Design Considerations in Web Services Standards provide important authentication and message-level security services for web services but they are not a complete security solution. Software systems are constructed in a way that potential harm caused by attackers is minimized eg software is deployed with least necessary privilege. Often COTS software with the potential for secure operation is. Nanophotonic inverse design with SPINS.
 Source: pinterest.com
Source: pinterest.com
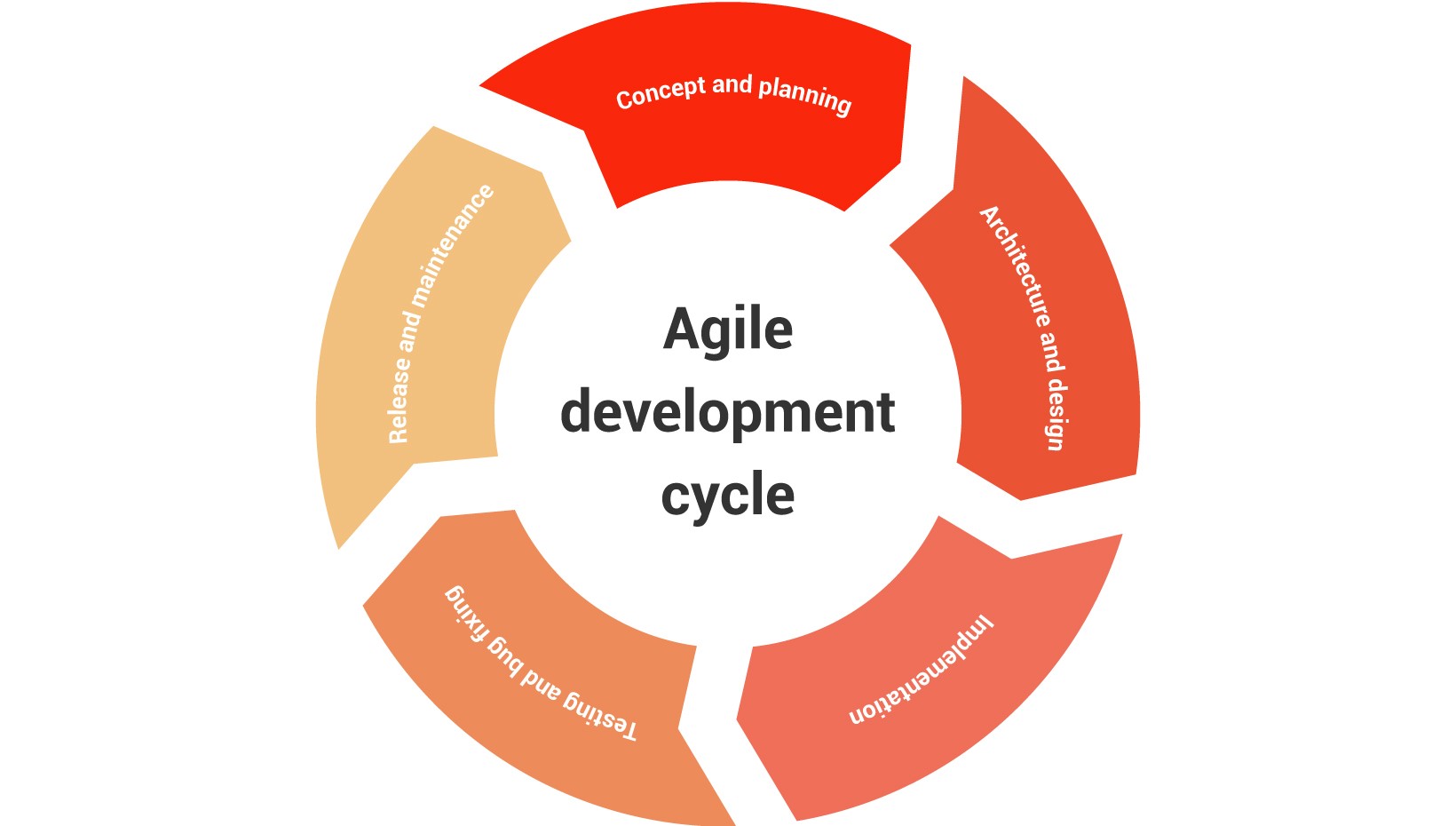
A computational nanophotonic design library for gradient-based optimization called SPINS is presented. Software architecture and practical considerations Cite as. Standards and Architecture Considerations for Secure Hardware Design and Verification Abstract. Nanophotonic inverse design with SPINS. Architecture considerations to implement secure software updates over the air By Bjoern Steurich August 03 2017 With increasing recognition that our cars are evolving into rolling data centers manufacturers.
 Source: pinterest.com
Source: pinterest.com
A big part of secure software architecture and design. Standards and Architecture Considerations for Secure Hardware Design and Verification Abstract. In this section we also examine some additional areas for the software security architect to focus on in web services from a defense-in-depth standpoint. This presentation considers the foundations of secure products in particular the need for true random number sources for nonce and key generation and product compliance with standards such as FIPS 140-2 and 186-4. But this definition falls flat in the agile development journey where working in increments and iterations is the core criteria.
 Source: pinterest.com
Source: pinterest.com
This presentation considers the foundations of secure products in particular the need for true random number sources for nonce and key generation and product compliance with standards such as FIPS 140-2 and 186-4. Sayer and Robert Seacord and D. Architecture and Design Considerations for Secure. The design of secure software. At the beginning of any secure network design project many best practices apply more or less uniformly to all areas of the design.
 Source: in.pinterest.com
Source: in.pinterest.com
Four Considerations for Security Architecture Design As organizations proceed enthusiastically with DI initiatives the implications for network security are often overlooked or minimized. The design of secure software. A computational nanophotonic design library for gradient-based optimization called SPINS is presented. Architecture and Design Considerations for Secure Software inproceedingsDougherty2011ArchitectureAD titleArchitecture and Design Considerations for Secure Software authorC. In this section we also examine some additional areas for the software security architect to focus on in web services from a defense-in-depth standpoint.
 Source: ptsecurity.com
Source: ptsecurity.com
Borrowing the concept of computational graphs SPINS is a design framework that emphasizes flexibility and reproducible results. In this section we also examine some additional areas for the software security architect to focus on in web services from a defense-in-depth standpoint. Security Design Considerations in Web Services Standards provide important authentication and message-level security services for web services but they are not a complete security solution. Youll understand how to identify and implement secure design when considering databases UML unit testing. Accounts for 14 of the CSSOP exam.
 Source: ptsecurity.com
Source: ptsecurity.com
Youll understand how to identify and implement secure design when considering databases UML unit testing. This article by Sean Convery presents these practices in. Initially software architecture design considerations were taken into account during the initial phase of development as changing the software is tougher in the later stages. Open Network Video Interface Forum Inc. At the beginning of any secure network design project many best practices apply more or less uniformly to all areas of the design.
 Source: pinterest.com
Source: pinterest.com
Vendors ship the packages with setup scripts that allow the user to set up the software for these very different purposes with very different security considerations. This presentation considers the foundations of secure products in particular the need for true random number sources for nonce and key generation and product compliance with standards such as FIPS 140-2 and 186-4. Architecture considerations to implement secure software updates over the air By Bjoern Steurich August 03 2017 With increasing recognition that our cars are evolving into rolling data centers manufacturers. This article by Sean Convery presents these practices in. Software design normally includes descriptions of the architecture components interfaces and other characteristics of a system or component.
 Source: pinterest.com
Source: pinterest.com
Sayer and Robert Seacord and D. Aside from the many considerations of actually using these algorithms in a secure manner - in itself no small task - there are the human factors to consider. Vendors ship the packages with setup scripts that allow the user to set up the software for these very different purposes with very different security considerations. PACS Architecture and Design Considerations Version 1806 June 2018 ONVIF 2 PACS Architecture and Design Considerations v1806 2008-2018 by ONVIF. Nanophotonic inverse design with SPINS.
 Source: pinterest.com
Source: pinterest.com
Aside from the many considerations of actually using these algorithms in a secure manner - in itself no small task - there are the human factors to consider. In this section we also examine some additional areas for the software security architect to focus on in web services from a defense-in-depth standpoint. At the beginning of any secure network design project many best practices apply more or less uniformly to all areas of the design. Software systems are constructed in a way that potential harm caused by attackers is minimized eg software is deployed with least necessary privilege. In fact almost 80 of organizations are9.
 Source: pinterest.com
Source: pinterest.com
So you can proactively incorporate. The mathematical and architectural details to achieve these goals are presented and practical considerations and heuristics for using inverse design are. This presentation considers the foundations of secure products in particular the need for true random number sources for nonce and key generation and product compliance with standards such as FIPS 140-2 and 186-4. Aside from the many considerations of actually using these algorithms in a secure manner - in itself no small task - there are the human factors to consider. The design of secure software.
 Source: pinterest.com
Source: pinterest.com
Sayer and Robert Seacord and D. Often COTS software with the potential for secure operation is. All rights Recipients of. Open Network Video Interface Forum Inc. A big part of secure software architecture and design.
 Source: pinterest.com
Source: pinterest.com
Architecture and Design Considerations for Secure Software inproceedingsDougherty2011ArchitectureAD titleArchitecture and Design Considerations for Secure Software authorC. Aside from the many considerations of actually using these algorithms in a secure manner - in itself no small task - there are the human factors to consider. Security Design Considerations in Web Services Standards provide important authentication and message-level security services for web services but they are not a complete security solution. But this definition falls flat in the agile development journey where working in increments and iterations is the core criteria. Svoboda and Kazuya Togashi year2011.
 Source: pinterest.com
Source: pinterest.com
Security Design Considerations in Web Services Standards provide important authentication and message-level security services for web services but they are not a complete security solution. PACS Architecture and Design Considerations Version 1806 June 2018 ONVIF 2 PACS Architecture and Design Considerations v1806 2008-2018 by ONVIF. Aside from the many considerations of actually using these algorithms in a secure manner - in itself no small task - there are the human factors to consider. So you can proactively incorporate. Borrowing the concept of computational graphs SPINS is a design framework that emphasizes flexibility and reproducible results.
 Source: pl.pinterest.com
Source: pl.pinterest.com
Software architecture and practical considerations Cite as. This presentation considers the foundations of secure products in particular the need for true random number sources for nonce and key generation and product compliance with standards such as FIPS 140-2 and 186-4. Often COTS software with the potential for secure operation is. Architecture and Design Considerations for Secure. So you can proactively incorporate.
This site is an open community for users to do submittion their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site helpful, please support us by sharing this posts to your favorite social media accounts like Facebook, Instagram and so on or you can also bookmark this blog page with the title architecture and design considerations for secure software by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.