Your Explain security architecture design in cloud computing images are ready. Explain security architecture design in cloud computing are a topic that is being searched for and liked by netizens now. You can Download the Explain security architecture design in cloud computing files here. Get all free vectors.
If you’re looking for explain security architecture design in cloud computing pictures information connected with to the explain security architecture design in cloud computing topic, you have visit the right site. Our website always gives you hints for viewing the maximum quality video and image content, please kindly surf and find more informative video content and graphics that fit your interests.
Explain Security Architecture Design In Cloud Computing. We can broadly divide the cloud architecture into two parts. The Cloud Computing is a model for enabling ubiquitous convenient on-demand network access to a shared pool of configurable computing resources eg networks servers storage applications and services that can be rapidly provisioned. This layer comprises of physical servers network and other aspects that can be physically managed and controlled. Businesses used cloud infrastructures to work with these applications.
 Security Architecture Applications Ibm Cloud Architecture Center From ibm.com
Security Architecture Applications Ibm Cloud Architecture Center From ibm.com
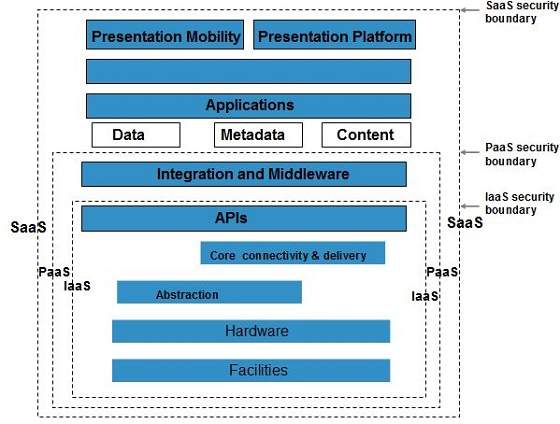
Cloud Computing Architecture As we know cloud computing technology is used by both small and large organizations to store the information in cloud and access it from anywhere at anytime using the internet connection. 3 Design The security architecture design in cloud computing may change just from the company to the company based on their requirement. SaaS Cloud Computing Security Architecture SaaS services provide access to software applications and data through a browser. List the different cloud architecture design principles tutorial brief notes dumps summary and pdf. We can broadly divide the cloud architecture into two parts. Cloud computing architecture is made of several layers for better operational efficiency.
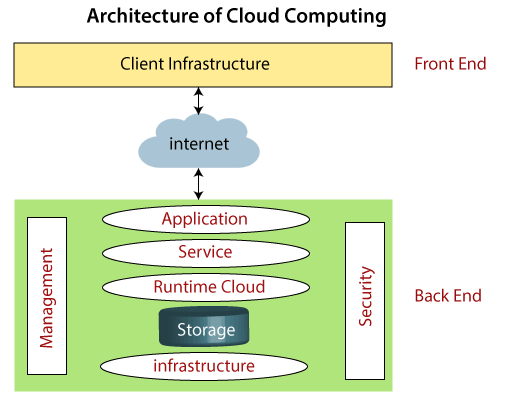
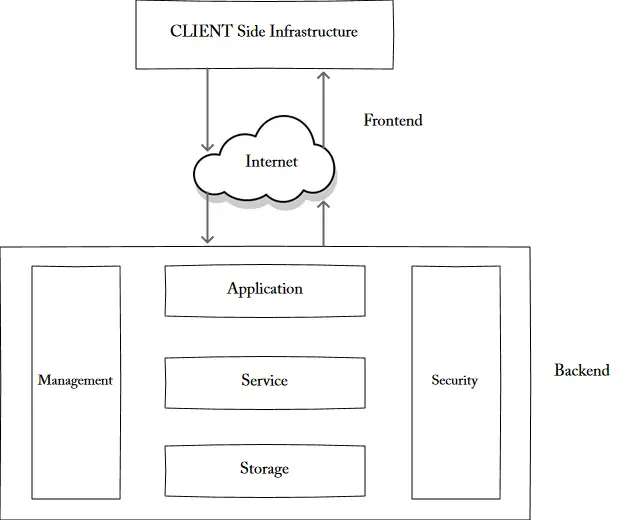
Front End Back End Each of the ends is connected through a network.
Its well known that most of the. Cloud Computing Architecture Diagrams Cloud Computing According to the definition of the National Institute of Standards and Technology NIST. Cloud controller or CLC is at the top and is used to manage virtualized resources like servers network and storage. Cloud Computing architecture comprises of many cloud components which are loosely coupled. This paper focuses on. It reviews and monitors online computing resources for achieving an optimal workflow.
 Source: pinterest.com
Source: pinterest.com
Front End Back End Each of the ends is connected through a network. Nowadays several enterprises are willing to adapt hybrid cloud security architecture. The Cloud Computing is a model for enabling ubiquitous convenient on-demand network access to a shared pool of configurable computing resources eg networks servers storage applications and services that can be rapidly provisioned. It is required to pass the aws cloud practitioner exam The Well-Architected Framework by Amazon helps users to build. Cloud controller or CLC is at the top and is used to manage virtualized resources like servers network and storage.
 Source: tutorialspoint.com
Source: tutorialspoint.com
SaaS Cloud Computing Security Architecture SaaS services provide access to software applications and data through a browser. It reviews and monitors online computing resources for achieving an optimal workflow. Cloud computings multitenancy and virtualization features pose unique security and access control challenges. Cloud Computing Architecture As we know cloud computing technology is used by both small and large organizations to store the information in cloud and access it from anywhere at anytime using the internet connection. Walrus is the next layer and.
 Source: pinterest.com
Source: pinterest.com
Walrus is the next layer and. Design Challengesin Architecture and Security 27 In the internet people like to use email for communication because of its convenience ef-ficiency and reliability. The specific terms of security responsibility may vary between services and are sometimes up for negotiation with the service provider. It reviews and monitors online computing resources for achieving an optimal workflow. 247 service availability and overall performance of the servers websites applications etc is ensured by manualautomated monitoring management.
 Source: javatpoint.com
Source: javatpoint.com
Cloud computing security architecture relies on having visibility throughout the cloud network with performance management capabilities. This paper focuses on. Cloud computing security addresses every physical and logical security issues across all the assorted service models of code platform and infrastructure. 3 Design The security architecture design in cloud computing may change just from the company to the company based on their requirement. The specific terms of security responsibility may vary between services and are sometimes up for negotiation with the service provider.
 Source: pinterest.com
Source: pinterest.com
Cloud computing security addresses every physical and logical security issues across all the assorted service models of code platform and infrastructure. Cloud computing security architecture relies on having visibility throughout the cloud network with performance management capabilities. This paper focuses on. 3 Design The security architecture design in cloud computing may change just from the company to the company based on their requirement. 247 service availability and overall performance of the servers websites applications etc is ensured by manualautomated monitoring management.
 Source: ibm.com
Source: ibm.com
Cloud Computing Architecture Diagrams Cloud Computing According to the definition of the National Institute of Standards and Technology NIST. A Review on Cloud Computing. Frontend is a userclient-facing architecture. Cloud computings multitenancy and virtualization features pose unique security and access control challenges. Design Challenges in Architecture and Security 35 earthquakes hurricanes etc.
 Source: pinterest.com
Source: pinterest.com
This layer comprises of physical servers network and other aspects that can be physically managed and controlled. The security issues at various levels of cloud computing environment is identified in this paper and categorized based on cloud computing architecture. Frontend is a userclient-facing architecture. Cloud Computing Architecture As we know cloud computing technology is used by both small and large organizations to store the information in cloud and access it from anywhere at anytime using the internet connection. Businesses used cloud infrastructures to work with these applications.
 Source: ro.pinterest.com
Source: ro.pinterest.com
Its well known that most of the. Figure - Cloud Computing Architecture. Walrus is the next layer and. Nowadays several enterprises are willing to adapt hybrid cloud security architecture. Cloud computings multitenancy and virtualization features pose unique security and access control challenges.
 Source: ibm.com
Source: ibm.com
SaaS Cloud Computing Security Architecture SaaS services provide access to software applications and data through a browser. Nowadays several enterprises are willing to adapt hybrid cloud security architecture. 247 service availability and overall performance of the servers websites applications etc is ensured by manualautomated monitoring management. Figure - Cloud Computing Architecture. This layer comprises of physical servers network and other aspects that can be physically managed and controlled.
 Source: w3schools.in
Source: w3schools.in
SaaS Cloud Computing Security Architecture SaaS services provide access to software applications and data through a browser. Businesses used cloud infrastructures to work with these applications. However these services area unit delivered. Cloud Computing Architecture As we know cloud computing technology is used by both small and large organizations to store the information in cloud and access it from anywhere at anytime using the internet connection. Cloud Computing Architecture Diagrams Cloud Computing According to the definition of the National Institute of Standards and Technology NIST.
 Source: pinterest.com
Source: pinterest.com
Design Challengesin Architecture and Security 27 In the internet people like to use email for communication because of its convenience ef-ficiency and reliability. Cloud controller or CLC is at the top and is used to manage virtualized resources like servers network and storage. Cloud computing security addresses every physical and logical security issues across all the assorted service models of code platform and infrastructure. The Cloud Computing is a model for enabling ubiquitous convenient on-demand network access to a shared pool of configurable computing resources eg networks servers storage applications and services that can be rapidly provisioned. SaaS Cloud Computing Security Architecture SaaS services provide access to software applications and data through a browser.
 Source: pinterest.com
Source: pinterest.com
Cloud Computing architecture comprises of many cloud components which are loosely coupled. It reviews and monitors online computing resources for achieving an optimal workflow. Walrus is the next layer and. Businesses used cloud infrastructures to work with these applications. Cloud Computing architecture comprises of many cloud components which are loosely coupled.
 Source: pinterest.com
Source: pinterest.com
Front End Back End Each of the ends is connected through a network. The specific terms of security responsibility may vary between services and are sometimes up for negotiation with the service provider. 247 service availability and overall performance of the servers websites applications etc is ensured by manualautomated monitoring management. A Review on Cloud Computing. Figure - Cloud Computing Architecture.
 Source: pinterest.com
Source: pinterest.com
We can broadly divide the cloud architecture into two parts. The specific terms of security responsibility may vary between services and are sometimes up for negotiation with the service provider. SaaS Cloud Computing Security Architecture SaaS services provide access to software applications and data through a browser. It is required to pass the aws cloud practitioner exam The Well-Architected Framework by Amazon helps users to build. At last BPO is one of the most unique out of all the layers of cloud computing architecture as unlike other layers it is concerned with outsourcing the services.
 Source: pinterest.com
Source: pinterest.com
The security issues at various levels of cloud computing environment is identified in this paper and categorized based on cloud computing architecture. In this article authors discuss a distributed architecture. SaaS Cloud Computing Security Architecture SaaS services provide access to software applications and data through a browser. It reviews and monitors online computing resources for achieving an optimal workflow. We can broadly divide the cloud architecture into two parts.
 Source: pinterest.com
Source: pinterest.com
A Review on Cloud Computing. Explain Security Monitoring in Cloud Computing Security monitoring in cloud computing or cloud monitoring is a software and process package. Could be analyzed by scientists to help predict further disasters. Cloud Computing architecture comprises of many cloud components which are loosely coupled. 3 Design The security architecture design in cloud computing may change just from the company to the company based on their requirement.
 Source: pinterest.com
Source: pinterest.com
Cloud Computing architecture comprises of many cloud components which are loosely coupled. The specific terms of security responsibility may vary between services and are sometimes up for negotiation with the service provider. Cloud Computing architecture comprises of many cloud components which are loosely coupled. Design Challengesin Architecture and Security 27 In the internet people like to use email for communication because of its convenience ef-ficiency and reliability. Unlike subscription-based pricing models the clouds payment structure enables the user to subscribe to vendor services and cloud infrastructures are paid on a pay-per-use basis.
 Source: pinterest.com
Source: pinterest.com
In this article authors discuss a distributed architecture. SaaS Cloud Computing Security Architecture SaaS services provide access to software applications and data through a browser. We can broadly divide the cloud architecture into two parts. Frontend is a userclient-facing architecture. Cloud computing security architecture relies on having visibility throughout the cloud network with performance management capabilities.
This site is an open community for users to submit their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site value, please support us by sharing this posts to your favorite social media accounts like Facebook, Instagram and so on or you can also bookmark this blog page with the title explain security architecture design in cloud computing by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.






