Your Layers in security architecture design in cloud computing images are available. Layers in security architecture design in cloud computing are a topic that is being searched for and liked by netizens now. You can Get the Layers in security architecture design in cloud computing files here. Find and Download all royalty-free vectors.
If you’re looking for layers in security architecture design in cloud computing images information linked to the layers in security architecture design in cloud computing topic, you have pay a visit to the right site. Our site always provides you with hints for seeking the highest quality video and picture content, please kindly surf and locate more enlightening video articles and graphics that match your interests.
Layers In Security Architecture Design In Cloud Computing. Cloud computing has three different service layers that are offered as services. SaaS Cloud Computing Security Architecture SaaS services provide access to software applications and data through a browser. Layers of security architecture do not have standard names that are universal across all architectures. A generic list of security architecture layers is as follows.
 From pinterest.com
From pinterest.com
3-1 Chapter 3 Cloud Computing Security Essentials and Architecture 31 The 3F Inflection Point in the History of the Internet and Information Systems The evolution of the nternet can be divided into three generations. Sections 3 and 4 explain high-level security objectives and principles policies and technologies relevant for the various policy abstraction levels and architecture layers in. Design Challenges in Architecture and Security 35 earthquakes hurricanes etc. In the 70sI the. Cloud computing has three different service layers that are offered as services. SaaS Cloud Computing Security Architecture SaaS services provide access to software applications and data through a browser.
PPT Cloud Computing Architecture IT Security PowerPoint presentation free to view - id.
Kernel and device drivers 3. Operating System In our. The exact definition of fog computing however is still being molded. A generic list of security architecture layers is as follows. These layers allow users to use cloud computing services optimally and achieve the kind of results they are looking for from the system. Cloud computing has three different service layers that are offered as services.
 Source: researchgate.net
Source: researchgate.net
Walrus is the next layer and. Design reviews of new changes can be better assessed against this architecture to assure that they conform to the principles described in the architecture allowing for more consistent and effective design. Cloud controller or CLC is at the top and is used to manage virtualized resources like servers network and storage. These layers allow users to use cloud computing services optimally and achieve the kind of results they are looking for from the system. Kernel and device drivers 3.
 Source: pinterest.com
Source: pinterest.com
Cloud computing has three different service layers that are offered as services. Cloud computing architecture is made of several layers for better operational efficiency. And its likely at least two teams one supporting but independent from cloud deployment projects that should be driving design and. Cloud controller or CLC is at the top and is used to manage virtualized resources like servers network and storage. Cloud computing security architecture relies on having visibility throughout the cloud network with performance management capabilities.
 Source: pinterest.com
Source: pinterest.com
NIST Cloud Computing Reference Architecture Recommendations of the National Institute of Standards and Technology Fang Liu Jin Tong Jian Mao Robert Bohn John Messina Lee Badger and Dawn Leaf Special. 3-1 Chapter 3 Cloud Computing Security Essentials and Architecture 31 The 3F Inflection Point in the History of the Internet and Information Systems The evolution of the nternet can be divided into three generations. Architecture Layers Harvard Universitys vision for enterprise architecture is to articulate and drive to common solutions standards and opportunities for alignment in order to reduce IT complexity and cost across the Security. In the 70sI the. - Infrastructure as a Service IaaS.
 Source: pinterest.com
Source: pinterest.com
Its well known that most of the. The exact definition of fog computing however is still being molded. Design Challenges in Architecture and Security 35 earthquakes hurricanes etc. The first is the infrastructure layer that is developed on the virtualization technology where the service providers offer virtual machines as a service to the end-users. Kernel and device drivers 3.
 Source: pinterest.com
Source: pinterest.com
SaaS Cloud Computing Security Architecture SaaS services provide access to software applications and data through a browser. Understanding the cloud system is equally important The cloud architecture is composed of several components that combine together to form different layers of cloud architecture. 4fa10c-N2Y5O The Adobe Flash plugin is needed to view this content. The exact definition of fog computing however is still being molded. Design Challenges in Architecture and Security 35 earthquakes hurricanes etc.
 Source: researchgate.net
Source: researchgate.net
These layers allow users to use cloud computing services optimally and achieve the kind of results they are looking for from the system. Operating System In our. PPT Cloud Computing Architecture IT Security PowerPoint presentation free to view - id. - Infrastructure as a Service IaaS. The first is the infrastructure layer that is developed on the virtualization technology where the service providers offer virtual machines as a service to the end-users.
 Source: pinterest.com
Source: pinterest.com
High-level layers of enterprise cloud security architecture should include the following. 3-1 Chapter 3 Cloud Computing Security Essentials and Architecture 31 The 3F Inflection Point in the History of the Internet and Information Systems The evolution of the nternet can be divided into three generations. Architecture Layers Harvard Universitys vision for enterprise architecture is to articulate and drive to common solutions standards and opportunities for alignment in order to reduce IT complexity and cost across the Security. Layers of security architecture do not have standard names that are universal across all architectures. Could be analyzed by scientists to help predict further disasters.
 Source: pinterest.com
Source: pinterest.com
Cloud computing has three different service layers that are offered as services. Cloud controller or CLC is at the top and is used to manage virtualized resources like servers network and storage. The first is the infrastructure layer that is developed on the virtualization technology where the service providers offer virtual machines as a service to the end-users. The exact definition of fog computing however is still being molded. 3-1 Chapter 3 Cloud Computing Security Essentials and Architecture 31 The 3F Inflection Point in the History of the Internet and Information Systems The evolution of the nternet can be divided into three generations.
 Source: pinterest.com
Source: pinterest.com
The exact definition of fog computing however is still being molded. In the 70sI the. And its likely at least two teams one supporting but independent from cloud deployment projects that should be driving design and. A generic list of security architecture layers is as follows. Design Challengesin Architecture and Security 27 In the internet people like to use email for communication because of its convenience ef-ficiency and reliability.
 Source: pinterest.com
Source: pinterest.com
Operating System In our. A generic list of security architecture layers is as follows. Design reviews of new changes can be better assessed against this architecture to assure that they conform to the principles described in the architecture allowing for more consistent and effective design. Security architecture and design looks at how information security controls and safeguards are implemented in IT systems in order to protect the confidentiality integrity and availability of the data that are used processed and stored. Kernel and device drivers 3.
 Source: pinterest.com
Source: pinterest.com
Its well known that most of the. Kernel and device drivers 3. A Review on Cloud Computing. Cloud computing has three different service layers that are offered as services. A generic list of security architecture layers is as follows.
 Source: researchgate.net
Source: researchgate.net
- Infrastructure as a Service IaaS. Cloud controller or CLC is at the top and is used to manage virtualized resources like servers network and storage. Could be analyzed by scientists to help predict further disasters. In the 70sI the. Architecture Layers Harvard Universitys vision for enterprise architecture is to articulate and drive to common solutions standards and opportunities for alignment in order to reduce IT complexity and cost across the Security.
 Source: pinterest.com
Source: pinterest.com
4fa10c-N2Y5O The Adobe Flash plugin is needed to view this content. Architecture Layers Harvard Universitys vision for enterprise architecture is to articulate and drive to common solutions standards and opportunities for alignment in order to reduce IT complexity and cost across the Security. The exact definition of fog computing however is still being molded. Walrus is the next layer and. Design Challenges in Architecture and Security 35 earthquakes hurricanes etc.
 Source: pinterest.com
Source: pinterest.com
Its well known that most of the. Operating System In our. The first is the infrastructure layer that is developed on the virtualization technology where the service providers offer virtual machines as a service to the end-users. These layers allow users to use cloud computing services optimally and achieve the kind of results they are looking for from the system. Security architecture and design looks at how information security controls and safeguards are implemented in IT systems in order to protect the confidentiality integrity and availability of the data that are used processed and stored.
 Source: pinterest.com
Source: pinterest.com
A generic list of security architecture layers is as follows. The specific terms of security responsibility may vary between services and are sometimes up for negotiation with the service provider. In the 70sI the. Sections 3 and 4 explain high-level security objectives and principles policies and technologies relevant for the various policy abstraction levels and architecture layers in. Kernel and device drivers 3.
 Source: pinterest.com
Source: pinterest.com
Security architecture and design looks at how information security controls and safeguards are implemented in IT systems in order to protect the confidentiality integrity and availability of the data that are used processed and stored. Cloud computing has three different service layers that are offered as services. Layers of security architecture do not have standard names that are universal across all architectures. The exact definition of fog computing however is still being molded. Design reviews of new changes can be better assessed against this architecture to assure that they conform to the principles described in the architecture allowing for more consistent and effective design.
 Source: pinterest.com
Source: pinterest.com
A Review on Cloud Computing. High-level layers of enterprise cloud security architecture should include the following. Layers of security architecture do not have standard names that are universal across all architectures. Sections 3 and 4 explain high-level security objectives and principles policies and technologies relevant for the various policy abstraction levels and architecture layers in. Understanding the cloud system is equally important The cloud architecture is composed of several components that combine together to form different layers of cloud architecture.
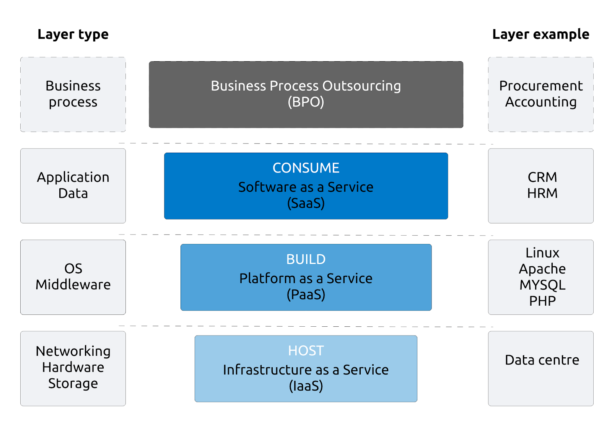 Source: visma.com
Source: visma.com
A generic list of security architecture layers is as follows. The first is the infrastructure layer that is developed on the virtualization technology where the service providers offer virtual machines as a service to the end-users. These layers allow users to use cloud computing services optimally and achieve the kind of results they are looking for from the system. Cloud computing has three different service layers that are offered as services. Operating System In our.
This site is an open community for users to submit their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site convienient, please support us by sharing this posts to your own social media accounts like Facebook, Instagram and so on or you can also save this blog page with the title layers in security architecture design in cloud computing by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.






