Your Nist security architecture design images are available in this site. Nist security architecture design are a topic that is being searched for and liked by netizens now. You can Download the Nist security architecture design files here. Find and Download all free images.
If you’re searching for nist security architecture design images information related to the nist security architecture design keyword, you have pay a visit to the right site. Our site frequently gives you suggestions for seeking the maximum quality video and picture content, please kindly hunt and locate more informative video articles and images that match your interests.
Nist Security Architecture Design. NISTとは 米国国立標準技術研究所の略称であり米国の技術や産業工業などに関する規格標準化を行っている政府機関です暗号技術の研究でも有名です サイバーセキュリティフレーム. The purpose of this publication is to provide a systematic approach to designing a technical security architecture for the exchange of health information that l Security Architecture Design Process for Health Information Exchanges HIEs NIST. Security architecture design process provides a scalable standardized and repeatable methodology to guide HIE system development in the integration of data protection mechanisms across each layer and results in a technology selection and design that satisfies high-level. Security Architecture Design Process for Health Information Exchanges NISTIR 7497 Draft.
 A Quick Nist Cybersecurity Framework Summary Cipher Cybersecurity Framework Cyber Security Framework From pinterest.com
A Quick Nist Cybersecurity Framework Summary Cipher Cybersecurity Framework Cyber Security Framework From pinterest.com
This architecture includes the typical technology silos found in a utility such as OT IT and physical access control systems PACS. Security architecture design process provides a scalable standardized and repeatable methodology to guide HIE system development in the integration of data protection mechanisms across each layer and results in a technology selection and design that satisfies high-level. The architecture must meet the baseline security requirements as codified in NIST Special Publication 800-53 or similar. Step 2 is creating the governance and compliance evidence codified in the form of policies procedures and security control implementations. Matthew Scholl NIST Kevin Stine NIST Kenneth Lin BAH Daniel Steinberg BAH Abstract The purpose of this publication is to provide a systematic approach to designing a technical security architecture for the exchange of health information that leverages common government and commercial practices and that demonstrates how these practices can be applied to the development. In our lab at the NCCoE which is part of NIST we built an environment that simulates an electric utilitys architecture.
A set of physical and logical security-relevant representations ie views of system architecture that conveys information about how the system is partitioned into security domains and makes use of security-relevant elements to enforce security policies within and between security domains based on how data.
Economy and public welfare by providing technical leadership for the nations measurement and standards infrastructure. The architecture must meet the baseline security requirements as codified in NIST Special Publication 800-53 or similar. In our lab at the NCCoE which is part of NIST we built an environment that simulates an electric utilitys architecture. Economy and public welfare by providing technical leadership for the nations measurement and standards infrastructure. Step 3 is the on-going monitoring operations and security management of the system. ITL develops tests test methods reference data proof of concept implementations and technical analysis.
 Source: pinterest.com
Source: pinterest.com
This architecture includes the typical technology silos found in a utility such as OT IT and physical access control systems PACS. 2 NIST SP 800-39. Matthew Scholl NIST Kevin Stine NIST Kenneth Lin BAH Daniel Steinberg BAH Abstract The purpose of this publication is to provide a systematic approach to designing a technical security architecture for the exchange of health information that leverages common government and commercial practices and that demonstrates how these practices can be applied to the development. NIST published Security Architecture Design Process for Health Information Exchanges HIEs NISTIR 7497 in September 2010 to provide a systematic approach to designing a technical security architecture for the exchange of health information that leverages common government and commercial practices and that demonstrates how these practices can be applied to the development. NIST SP 800-37 Rev.
 Source: pinterest.com
Source: pinterest.com
213 Guidance on Security for the Architecture Domains. A set of physical and logical security-relevant representations ie views of system architecture that conveys information about how the system is partitioned into security domains and makes use of security-relevant elements to enforce security policies within and between security domains based on how data. The Information Technology Laboratory ITL at the National Institute of Standards and Technology NIST promotes the US. Developer security and privacy architecture and design are directed at external developers although they could also be applied to internal in-house development. NISTとは 米国国立標準技術研究所の略称であり米国の技術や産業工業などに関する規格標準化を行っている政府機関です暗号技術の研究でも有名です サイバーセキュリティフレーム.
 Source: pinterest.com
Source: pinterest.com
The purpose of this publication is to provide a systematic approach to designing a technical security architecture for the exchange of health information that l Security Architecture Design Process for Health Information Exchanges HIEs NIST. A set of physical and logical security-relevant representations ie views of system architecture that conveys information about how the system is partitioned into security domains and makes use of security-relevant elements to enforce security policies within and between security domains based on how data. NIST published Security Architecture Design Process for Health Information Exchanges HIEs NISTIR 7497 in September 2010 to provide a systematic approach to designing a technical security architecture for the exchange of health information that leverages common government and commercial practices and that demonstrates how these practices can be applied to the development. Security architecture design process provides a scalable standardized and repeatable methodology to guide HIE system development in the integration of data protection mechanisms across each layer and results in a technology selection and design that satisfies high-level. Security architecture introduces unique single-purpose components in the design.
 Source: pinterest.com
Source: pinterest.com
A set of physical and logical security-relevant representations ie views of system architecture that conveys information about how the system is partitioned into security domains and makes use of security-relevant elements to enforce security policies within and between security domains based on how data. ITL develops tests test methods reference data proof of concept implementations and technical analysis. Developer security and privacy architecture and design are directed at external developers although they could also be applied to internal in-house development. The purpose of this publication is to provide a systematic approach to designing a technical security architecture for the exchange of health information that l Security Architecture Design Process for Health Information Exchanges HIEs NIST. The Information Technology Laboratory ITL at the National Institute of Standards and Technology NIST promotes the US.
 Source: pinterest.com
Source: pinterest.com
In contrast PL-8 is directed at internal developers to ensure that organizations develop a security and privacy architecture that is integrated with the enterprise architecture. A set of physical and logical security-relevant representations ie views of system architecture that conveys information about how the system is partitioned into security domains and makes use of security-relevant elements to enforce security policies within and between security domains based on how data. Security architecture introduces unique single-purpose components in the design. In our lab at the NCCoE which is part of NIST we built an environment that simulates an electric utilitys architecture. NIST is responsible for developing information security standards and guidelines including minimum requirements for federal information systems but such standards and guidelines shall not apply to national security systems without the express approval.
 Source: pinterest.com
Source: pinterest.com
Developer security and privacy architecture and design are directed at external developers although they could also be applied to internal in-house development. Economy and public welfare by providing technical leadership for the nations measurement and standards infrastructure. Security architecture calls for its own unique set of skills and competencies of the enterprise and IT architects. Security architecture design process provides a scalable standardized and repeatable methodology to guide HIE system development in the integration of data protection mechanisms across each layer and results in a technology selection and design that satisfies high-level. A set of physical and logical security-relevant representations ie views of system architecture that conveys information about how the system is partitioned into security domains and makes use of security-relevant elements to enforce security policies within and between security domains based on how data.
 Source: pinterest.com
Source: pinterest.com
Security architecture introduces unique single-purpose components in the design. Step 2 is creating the governance and compliance evidence codified in the form of policies procedures and security control implementations. A set of physical and logical security-relevant representations ie views of system architecture that conveys information about how the system is partitioned into security domains and makes use of security-relevant elements to enforce security policies within and between security domains based on how data. The architecture must meet the baseline security requirements as codified in NIST Special Publication 800-53 or similar. Matthew Scholl NIST Kevin Stine NIST Kenneth Lin BAH Daniel Steinberg BAH Abstract The purpose of this publication is to provide a systematic approach to designing a technical security architecture for the exchange of health information that leverages common government and commercial practices and that demonstrates how these practices can be applied to the development.
 Source: pinterest.com
Source: pinterest.com
2 NIST SP 800-39. The architecture must meet the baseline security requirements as codified in NIST Special Publication 800-53 or similar. NIST is responsible for developing information security standards and guidelines including minimum requirements for federal information systems but such standards and guidelines shall not apply to national security systems without the express approval. Security architecture introduces unique single-purpose components in the design. 213 Guidance on Security for the Architecture Domains.
 Source: pinterest.com
Source: pinterest.com
Matthew Scholl NIST Kevin Stine NIST Kenneth Lin BAH Daniel Steinberg BAH Abstract The purpose of this publication is to provide a systematic approach to designing a technical security architecture for the exchange of health information that leverages common government and commercial practices and that demonstrates how these practices can be applied to the development. This architecture includes the typical technology silos found in a utility such as OT IT and physical access control systems PACS. In our lab at the NCCoE which is part of NIST we built an environment that simulates an electric utilitys architecture. 213 Guidance on Security for the Architecture Domains. ITL develops tests test methods reference data proof of concept implementations and technical analysis.
 Source: pinterest.com
Source: pinterest.com
ITL develops tests test methods reference data proof of concept implementations and technical analysis. 213 Guidance on Security for the Architecture Domains. Step 2 is creating the governance and compliance evidence codified in the form of policies procedures and security control implementations. ITL develops tests test methods reference data proof of concept implementations and technical analysis. The architecture must meet the baseline security requirements as codified in NIST Special Publication 800-53 or similar.
 Source: pinterest.com
Source: pinterest.com
NISTとは 米国国立標準技術研究所の略称であり米国の技術や産業工業などに関する規格標準化を行っている政府機関です暗号技術の研究でも有名です サイバーセキュリティフレーム. Economy and public welfare by providing technical leadership for the nations measurement and standards infrastructure. Step 3 is the on-going monitoring operations and security management of the system. Security Architecture Design Process for Health Information Exchanges NISTIR 7497 Draft. This architecture includes the typical technology silos found in a utility such as OT IT and physical access control systems PACS.
 Source: pinterest.com
Source: pinterest.com
The purpose of this publication is to provide a systematic approach to designing a technical security architecture for the exchange of health information that l Security Architecture Design Process for Health Information Exchanges HIEs NIST. 213 Guidance on Security for the Architecture Domains. Economy and public welfare by providing technical leadership for the nations measurement and standards infrastructure. A set of physical and logical security-relevant representations ie views of system architecture that conveys information about how the system is partitioned into security domains and makes use of security-relevant elements to enforce security policies within and between security domains based on how data. Security architecture introduces unique single-purpose components in the design.
 Source: nl.pinterest.com
Source: nl.pinterest.com
Matthew Scholl NIST Kevin Stine NIST Kenneth Lin BAH Daniel Steinberg BAH Abstract The purpose of this publication is to provide a systematic approach to designing a technical security architecture for the exchange of health information that leverages common government and commercial practices and that demonstrates how these practices can be applied to the development. Security architecture design process provides a scalable standardized and repeatable methodology to guide HIE system development in the integration of data protection mechanisms across each layer and results in a technology selection and design that satisfies high-level. NIST is responsible for developing information security standards and guidelines including minimum requirements for federal information systems but such standards and guidelines shall not apply to national security systems without the express approval. NISTとは 米国国立標準技術研究所の略称であり米国の技術や産業工業などに関する規格標準化を行っている政府機関です暗号技術の研究でも有名です サイバーセキュリティフレーム. NIST published Security Architecture Design Process for Health Information Exchanges HIEs NISTIR 7497 in September 2010 to provide a systematic approach to designing a technical security architecture for the exchange of health information that leverages common government and commercial practices and that demonstrates how these practices can be applied to the development.
 Source: pinterest.com
Source: pinterest.com
Security architecture design process provides a scalable standardized and repeatable methodology to guide HIE system development in the integration of data protection mechanisms across each layer and results in a technology selection and design that satisfies high-level. A set of physical and logical security-relevant representations ie views of system architecture that conveys information about how the system is partitioned into security domains and makes use of security-relevant elements to enforce security policies within and between security domains based on how data. Economy and public welfare by providing technical leadership for the nations measurement and standards infrastructure. Security architecture design process provides a scalable standardized and repeatable methodology to guide HIE system development in the integration of data protection mechanisms across each layer and results in a technology selection and design that satisfies high-level. Security architecture introduces unique single-purpose components in the design.
 Source: pinterest.com
Source: pinterest.com
In contrast PL-8 is directed at internal developers to ensure that organizations develop a security and privacy architecture that is integrated with the enterprise architecture. ITL develops tests test methods reference data proof of concept implementations and technical analysis. 213 Guidance on Security for the Architecture Domains. Security architecture design process provides a scalable standardized and repeatable methodology to guide HIE system development in the integration of data protection mechanisms across each layer and results in a technology selection and design that satisfies high-level. Developer security and privacy architecture and design are directed at external developers although they could also be applied to internal in-house development.
 Source: pinterest.com
Source: pinterest.com
Security architecture design process provides a scalable standardized and repeatable methodology to guide HIE system development in the integration of data protection mechanisms across each layer and results in a technology selection and design that satisfies high-level. The Information Technology Laboratory ITL at the National Institute of Standards and Technology NIST promotes the US. In contrast PL-8 is directed at internal developers to ensure that organizations develop a security and privacy architecture that is integrated with the enterprise architecture. Security architecture design process provides a scalable standardized and repeatable methodology to guide HIE system development in the integration of data protection mechanisms across each layer and results in a technology selection and design that satisfies high-level. A set of physical and logical security-relevant representations ie views of system architecture that conveys information about how the system is partitioned into security domains and makes use of security-relevant elements to enforce security policies within and between security domains based on how data.
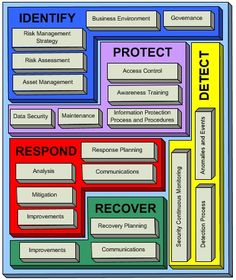 Source: pinterest.com
Source: pinterest.com
A set of physical and logical security-relevant representations ie views of system architecture that conveys information about how the system is partitioned into security domains and makes use of security-relevant elements to enforce security policies within and between security domains based on how data. In our lab at the NCCoE which is part of NIST we built an environment that simulates an electric utilitys architecture. The purpose of this publication is to provide a systematic approach to designing a technical security architecture for the exchange of health information that l Security Architecture Design Process for Health Information Exchanges HIEs NIST. The architecture must meet the baseline security requirements as codified in NIST Special Publication 800-53 or similar. Security Architecture Design Process for Health Information Exchanges NISTIR 7497 Draft.
 Source: pinterest.com
Source: pinterest.com
Step 3 is the on-going monitoring operations and security management of the system. Security architecture design process provides a scalable standardized and repeatable methodology to guide HIE system development in the integration of data protection mechanisms across each layer and results in a technology selection and design that satisfies high-level. NISTとは 米国国立標準技術研究所の略称であり米国の技術や産業工業などに関する規格標準化を行っている政府機関です暗号技術の研究でも有名です サイバーセキュリティフレーム. NIST SP 800-37 Rev. NIST published Security Architecture Design Process for Health Information Exchanges HIEs NISTIR 7497 in September 2010 to provide a systematic approach to designing a technical security architecture for the exchange of health information that leverages common government and commercial practices and that demonstrates how these practices can be applied to the development.
This site is an open community for users to share their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site value, please support us by sharing this posts to your favorite social media accounts like Facebook, Instagram and so on or you can also save this blog page with the title nist security architecture design by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.






