Your Owasp architecture design and threat modelling images are ready. Owasp architecture design and threat modelling are a topic that is being searched for and liked by netizens now. You can Find and Download the Owasp architecture design and threat modelling files here. Get all free photos and vectors.
If you’re looking for owasp architecture design and threat modelling images information related to the owasp architecture design and threat modelling keyword, you have visit the ideal site. Our site frequently provides you with suggestions for downloading the highest quality video and image content, please kindly surf and locate more enlightening video content and images that fit your interests.
Owasp Architecture Design And Threat Modelling. Cryptography at rest V8. The purpose of threat modelling is to provide defenders with a. However mobile application security managers and practitioners can find app-specific threat modeling guidance from the Open Web Application Security Project better known as OWASP a vendor-neutral community for advancing appsec. V1 Architecture design and threat modelling.
 Pasta Threat Modeling For Cybersecurity Owasp All Chapters 2020 Presentation Youtube From youtube.com
Pasta Threat Modeling For Cybersecurity Owasp All Chapters 2020 Presentation Youtube From youtube.com
V6 Output encoding escaping. OWASP Threat Dragon is an open-source threat modeling tool both web application and desktop that is used to create threat model diagrams record the most likely threats and decide the action to mitigate said threats. Architecture design and threat modelling V2. To cover topics such as threat modelling secure SDLC or key management users of the MASVS should consult the respective OWASP projects andor other standards such as the ones linked below. V2 Authentication verification requirements. OWASP Introduction to Threat Modeling Threat Modeling.
V5 Malicious input handling verification requirements.
V4 Access control verification requirements. OWASP MASVS 10は2018年1月にリリースされました要件の一覧は以下の通りです 各要件の詳細は公開したMASVSの日本語訳をご覧ください V1 Architecture Design and Threat Modeling Requirements. OWASP Threat Dragon This is a free open-source threat modeling web-based application that includes a rule engine and system diagramming to auto-generate threats and mitigations. The objective of this index is to help an OWASP Application Security Verification Standard ASVS user clearly identify which cheat sheets are useful for each section during his or her usage of the ASVS. As such this is the only category that does not map to technical test cases in the OWASP Mobile Testing Guide. However mobile application security managers and practitioners can find app-specific threat modeling guidance from the Open Web Application Security Project better known as OWASP a vendor-neutral community for advancing appsec.
 Source: in.pinterest.com
Source: in.pinterest.com
As such this is the only category that does not map to technical test cases in the OWASP Mobile Testing Guide. Threat Modeling SMEs or Security Assessors who are responsible for analyzing the security of the entire applciations components. As such this is the only category that does not map to technical test cases in the OWASP Mobile Testing Guide. About EC-Councils Certified Threat Intelligence Analyst CTIA Program. In 2011 OWASP launched the Mobile Top 10 list to identify the biggest security issues to focus on.
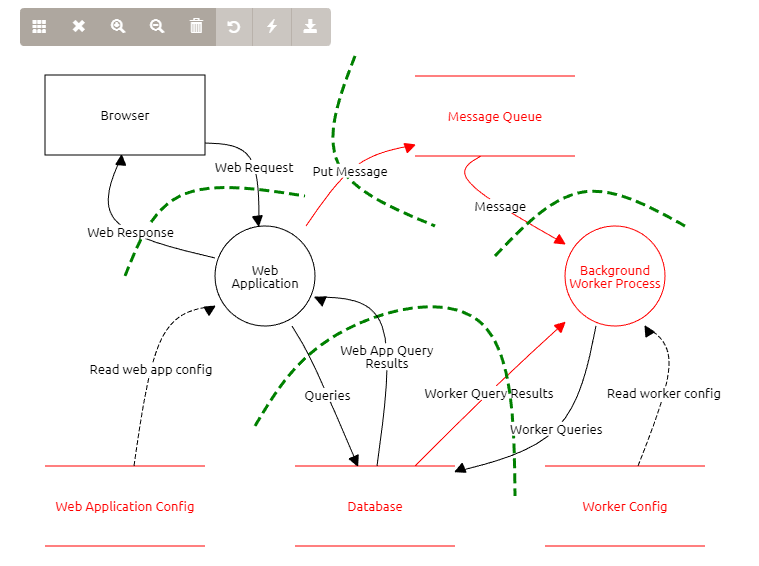
OWASP Introduction to Threat Modeling Threat Modeling. Threat modelling is a process by which potential threats can be identified enumerated and prioritised all from a hypothetical attackers point of view. V7 Cryptography at rest verification requirements. Threat Modeling SMEs or Security Assessors who are responsible for analyzing the security of the entire applciations components. 13 行 As such this is the only category that does not map to technical test cases in the OWASP.

Architecture Design and Threat Modeling Requirements. The days of the enterprise architect have passed in the age of DevSecOps. OWASPOpen Web Application Security Project読み方オワスプとはソフトウェアやWebアプリケーションのセキュリティ分野の研究やガイドラインの作成脆弱性診断ツールの開発イベント開催など多岐にわたる活動をしているオープンソースソフトウェアコミュニティです. V1 Architecture Design and Threat Modeling Control Objective Security architecture has almost become a lost art in many organizations. This index is based on the version 4x of the ASVS.
 Source: slideshare.net
Source: slideshare.net
This index is based on the version 4x of the ASVS. V1 Architecture design and threat modelling. V1 Architecture Design and Threat Modeling Control Objective Security architecture has almost become a lost art in many organizations. The objective of this index is to help an OWASP Application Security Verification Standard ASVS user clearly identify which cheat sheets are useful for each section during his or her usage of the ASVS. This index is based on the version 4x of the ASVS.
 Source: pinterest.com
Source: pinterest.com
OWASPOpen Web Application Security Project読み方オワスプとはソフトウェアやWebアプリケーションのセキュリティ分野の研究やガイドラインの作成脆弱性診断ツールの開発イベント開催など多岐にわたる活動をしているオープンソースソフトウェアコミュニティです. V5 Malicious input handling verification requirements. About EC-Councils Certified Threat Intelligence Analyst CTIA Program. Model Design Threat Assessment. Malicious input handling V7.
 Source: pinterest.com
Source: pinterest.com
Architecture design and threat modelling V2. Architecture design and threat modelling V2. V3 Session management verification requirements. About EC-Councils Certified Threat Intelligence Analyst CTIA Program. V1 Architecture design and threat modelling.
 Source: in.pinterest.com
Source: in.pinterest.com
Threat Dragon is both an online threat modeling web application and a. Model Design Threat Assessment. This cheat sheet provides guidance to assess existing apps as well as new apps. V7 Cryptography at rest verification requirements. A systematic structured security technique used to identify the security objectives threats vulnerabilities of an application to help make design and engineering.
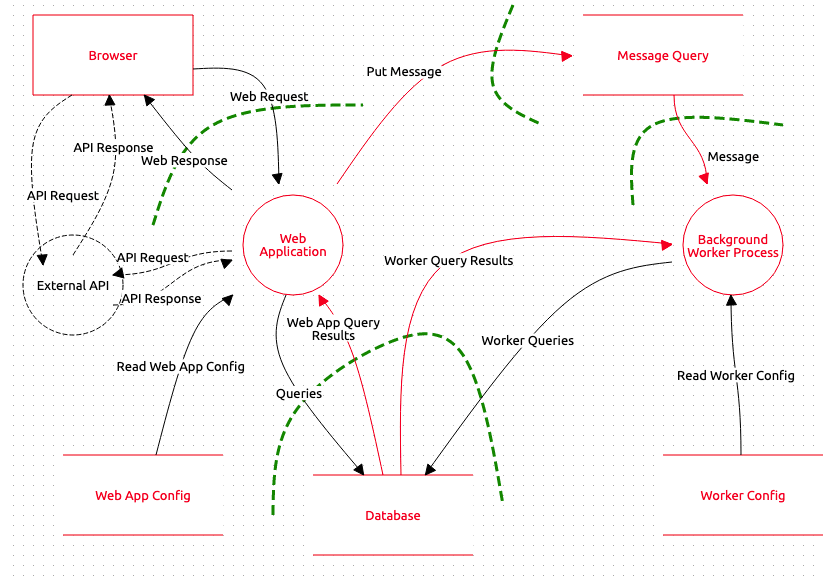 Source: dev.to
Source: dev.to
Threat modelling is a process by which potential threats can be identified enumerated and prioritised all from a hypothetical attackers point of view. The days of the enterprise architect have passed in the age of DevSecOps. OWASP MASVS 10は2018年1月にリリースされました要件の一覧は以下の通りです 各要件の詳細は公開したMASVSの日本語訳をご覧ください V1 Architecture Design and Threat Modeling Requirements. OWASP Introduction to Threat Modeling Threat Modeling. OWASP Threat Dragon This is a free open-source threat modeling web-based application that includes a rule engine and system diagramming to auto-generate threats and mitigations.
 Source: speakerdeck.com
Source: speakerdeck.com
In 2011 OWASP launched the Mobile Top 10 list to identify the biggest security issues to focus on. Architecture design and threat modelling V2. A systematic structured security technique used to identify the security objectives threats vulnerabilities of an application to help make design and engineering. OWASP MASVS 10は2018年1月にリリースされました要件の一覧は以下の通りです 各要件の詳細は公開したMASVSの日本語訳をご覧ください V1 Architecture Design and Threat Modeling Requirements.

V6 Output encoding escaping. What is Threat Modelling. Threat Modeling SMEs or Security Assessors who are responsible for analyzing the security of the entire applciations components. The days of the enterprise architect have passed in the age of DevSecOps. V4 Access control verification requirements.
 Source: pinterest.com
Source: pinterest.com
V4 Access control verification requirements. The purpose of threat modelling is to provide defenders with a. V7 Cryptography at rest verification requirements. Threat Modeling SMEs or Security Assessors who are responsible for analyzing the security of the entire applciations components. Cryptography at rest V8.

To cover topics such as threat modelling secure SDLC or key management users of the MASVS should consult the respective OWASP projects andor other standards such as the ones linked below. Architecture Design and Threat Modeling Requirements. From details about threats and likely attacks against each project the organization as a whole operates. However mobile application security managers and practitioners can find app-specific threat modeling guidance from the Open Web Application Security Project better known as OWASP a vendor-neutral community for advancing appsec. To cover topics such as threat modelling secure SDLC or key management users of the MASVS should consult the respective OWASP projects andor other standards such as the ones linked below.

As such this is the only category that does not map to technical test cases in the OWASP Mobile Testing Guide. V7 Cryptography at rest verification requirements. To cover topics such as threat modelling secure SDLC or key management users of the MASVS should consult the respective OWASP projects andor other standards such as the ones linked below. OWASP Threat Dragon is an open-source threat modeling tool both web application and desktop that is used to create threat model diagrams record the most likely threats and decide the action to mitigate said threats. V5 Malicious input handling verification requirements.
 Source: securecav.com
Source: securecav.com
OWASP Threat Dragon This is a free open-source threat modeling web-based application that includes a rule engine and system diagramming to auto-generate threats and mitigations.
 Source: synopsys.com
Source: synopsys.com
OWASPOpen Web Application Security Project読み方オワスプとはソフトウェアやWebアプリケーションのセキュリティ分野の研究やガイドラインの作成脆弱性診断ツールの開発イベント開催など多岐にわたる活動をしているオープンソースソフトウェアコミュニティです. The objective of this index is to help an OWASP Application Security Verification Standard ASVS user clearly identify which cheat sheets are useful for each section during his or her usage of the ASVS. From details about threats and likely attacks against each project the organization as a whole operates. Threat modelling is a process by which potential threats can be identified enumerated and prioritised all from a hypothetical attackers point of view. V1 Architecture Design and Threat Modeling Control Objective Security architecture has almost become a lost art in many organizations.
 Source: youtube.com
Source: youtube.com
Architecture design and threat modelling V2. Cryptography at rest V8. 13 行 As such this is the only category that does not map to technical test cases in the OWASP. In 2011 OWASP launched the Mobile Top 10 list to identify the biggest security issues to focus on. OWASPOpen Web Application Security Project読み方オワスプとはソフトウェアやWebアプリケーションのセキュリティ分野の研究やガイドラインの作成脆弱性診断ツールの開発イベント開催など多岐にわたる活動をしているオープンソースソフトウェアコミュニティです.
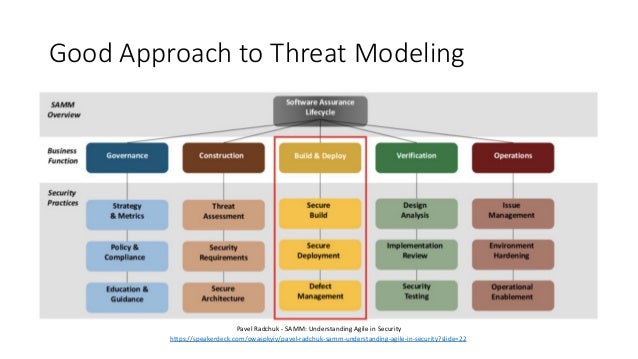 Source: slideshare.net
Source: slideshare.net
V6 Output encoding escaping. As such this is the only category that does not map to technical test cases in the OWASP Mobile Testing Guide. This index is based on the version 4x of the ASVS. The objective of this index is to help an OWASP Application Security Verification Standard ASVS user clearly identify which cheat sheets are useful for each section during his or her usage of the ASVS. Threat Dragon is both an online threat modeling web application and a.
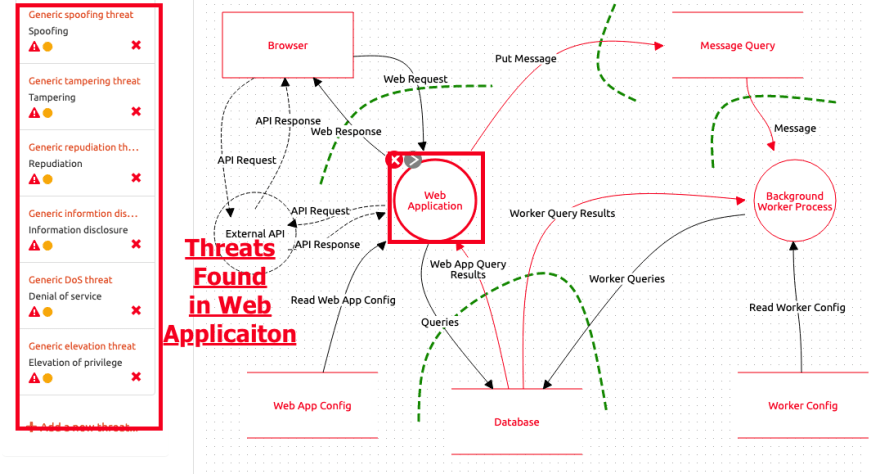 Source: dev.to
Source: dev.to
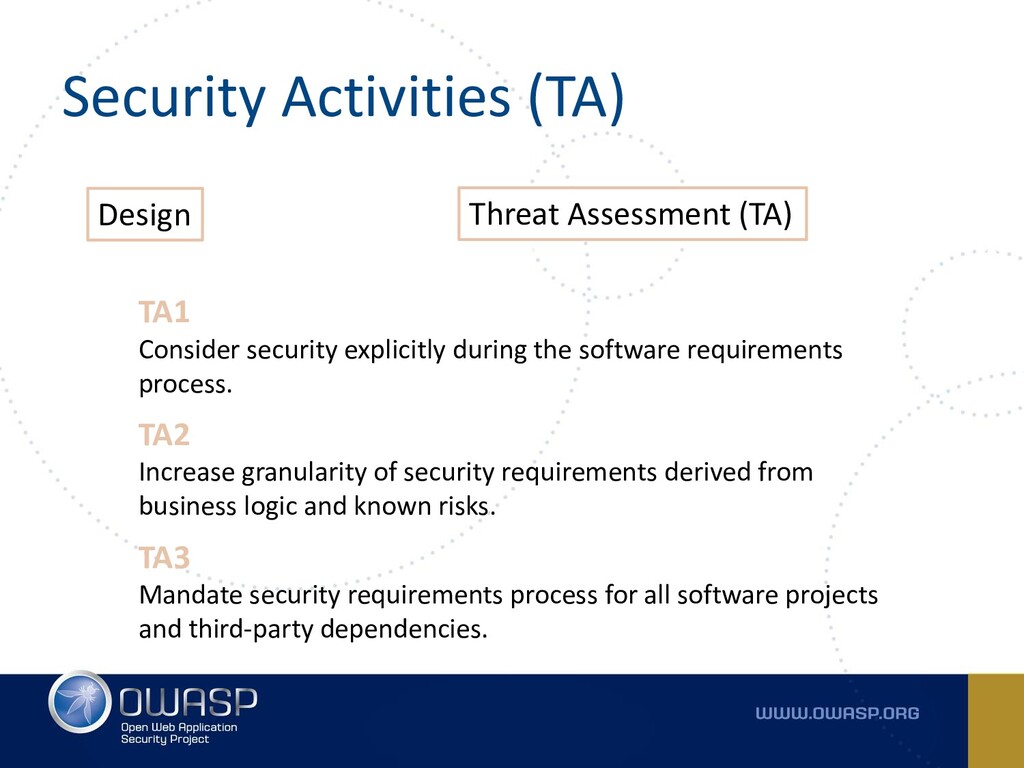
The Threat Assessment TA practice focuses on identifying and understanding of project-level risks based on the functionality of the software being developed and characteristics of the runtime environment. Malicious input handling V7. V3 Session management verification requirements. The Threat Assessment TA practice focuses on identifying and understanding of project-level risks based on the functionality of the software being developed and characteristics of the runtime environment. Error handling and logging V9.
This site is an open community for users to submit their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site helpful, please support us by sharing this posts to your preference social media accounts like Facebook, Instagram and so on or you can also bookmark this blog page with the title owasp architecture design and threat modelling by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.






