Your Principles of secure processor architecture design pdf images are ready. Principles of secure processor architecture design pdf are a topic that is being searched for and liked by netizens today. You can Find and Download the Principles of secure processor architecture design pdf files here. Find and Download all royalty-free images.
If you’re looking for principles of secure processor architecture design pdf images information connected with to the principles of secure processor architecture design pdf interest, you have pay a visit to the ideal blog. Our site frequently gives you hints for downloading the highest quality video and picture content, please kindly hunt and find more enlightening video articles and images that fit your interests.
Principles Of Secure Processor Architecture Design Pdf. Secure the weakest link 2. I am pleased to announce the latest title in Morgan Claypools series on Computer Architecture. It details the five basic principles needed for secure processor architecture design. Jakub Szefer ISBN-10 书号.
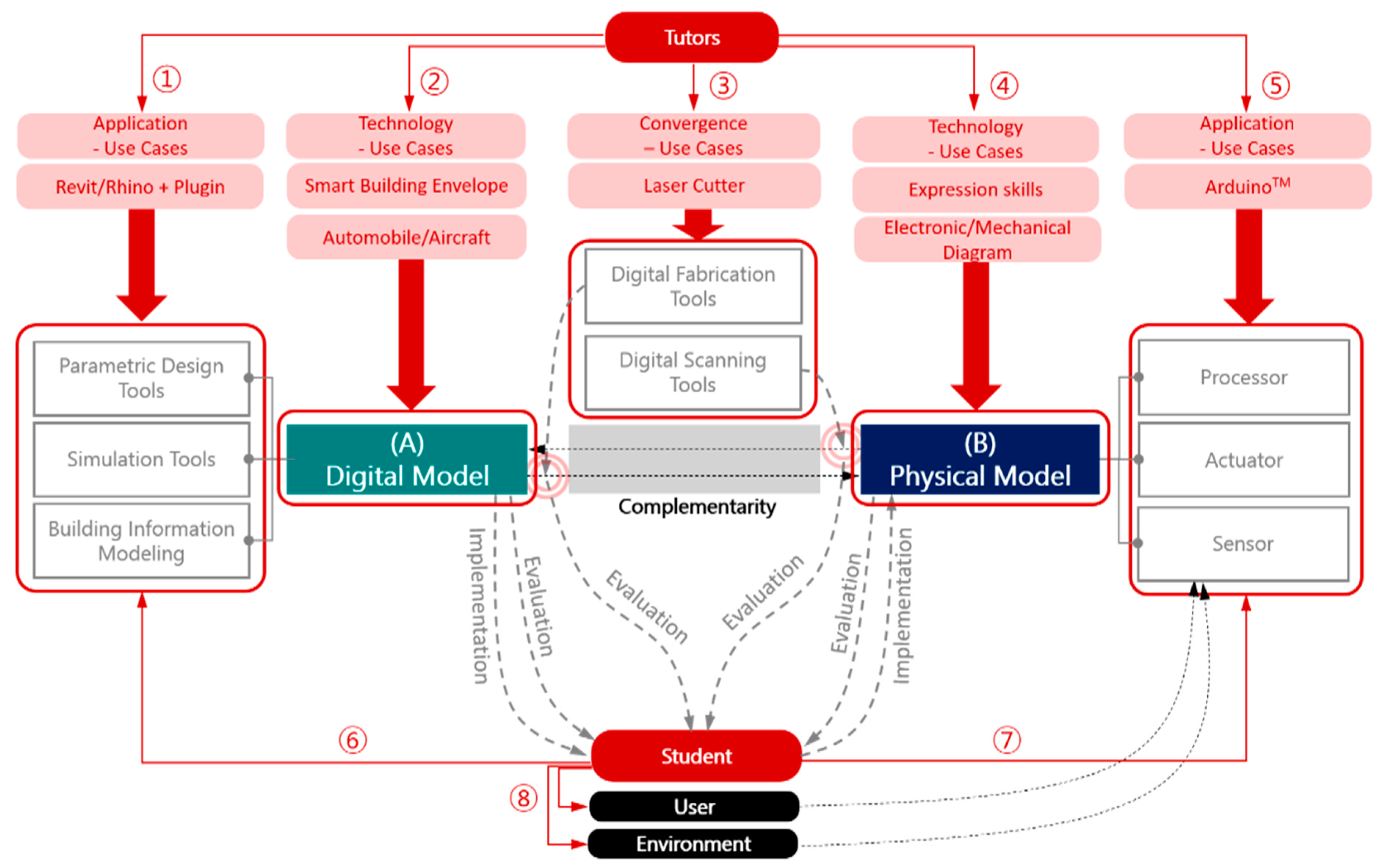 Sustainability Free Full Text A Design Methodology Using Prototyping Based On The Digital Physical Models In The Architectural Design Process Html From mdpi.com
Sustainability Free Full Text A Design Methodology Using Prototyping Based On The Digital Physical Models In The Architectural Design Process Html From mdpi.com
This book aims to give readers insights into the principles behind the design of academic and commercial secure processor architectures.
By design principles when creating new solutions.
 Source: amazon.com
Source: amazon.com
Principles of Secure Processor Architecture Design Jakub Szefer Yale University.
 Source: amazon.com
Source: amazon.com
Secure processor architecture research is concerned with exploring and design. The tutorial will be given on. Jakub Szefer Assistant Professor Dept. Jakub Szefer Assistant Professor Dept. Secure the weakest link 2.
 Source: caslab.csl.yale.edu
Source: caslab.csl.yale.edu
With growing interest in computer security and the protection of the code and data which execute on commodity computers.
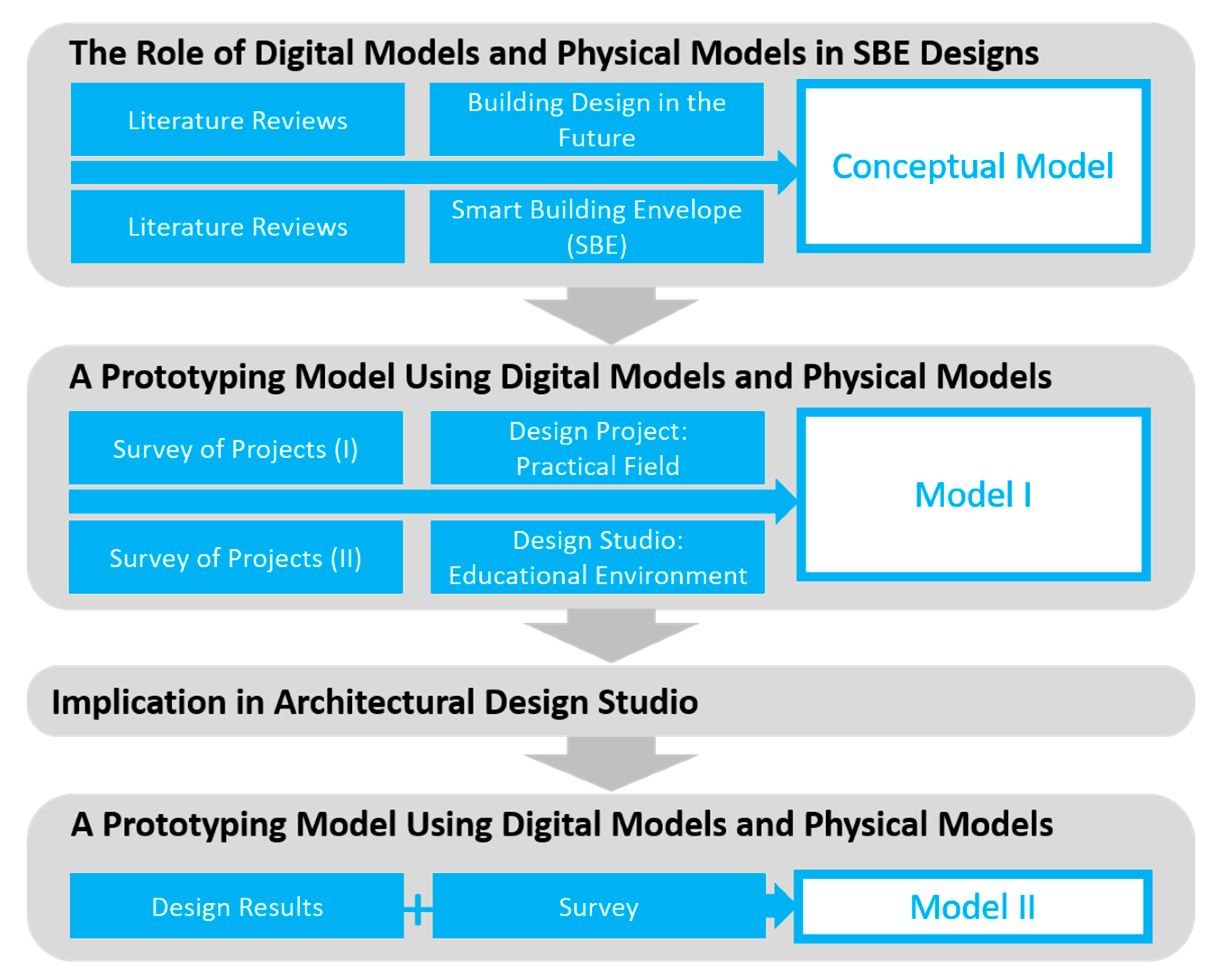 Source: mdpi.com
Source: mdpi.com
Grant least privilege 5. The book also presents existing research challenges and potential new research directions. With growing interest in computer security and the protection of the code and data which execute on commodity computers. Request PDF Principles of Secure Processor Architecture Design With growing interest in computer security and the protection of the code and data which execute on commodity computers. Web page for the tutorial on Principles of Secure Processor Architecture Design which will be presented at ASPLOS 2019 in Providence RI on April 14th 2019.
 Source: pinterest.com
Source: pinterest.com
Defend in depth 3. JohnMitchell SecureArchitecture Principles CS155 Spring2015 IsolaonandLeastPrivilege AccessControlConcepts OperangSystems JohnMitchell. Margaret Martonosi Princeton UniversityPrinciples of Secure Processor Architecture Design Jakub Szefer Yale. Jakub Szefer Principles of Secure Processor Architecture Design Morgan Claypool Publishers October 2018. By design principles when creating new solutions.
 Source: pinterest.com
Source: pinterest.com
The book also presents existing research challenges and potential new research directions. It details the five basic principles needed for secure processor architecture design. Secure the weakest link 2. MIPS RISC Design Principles Simplicity favors regularity fixed size instructions small number of instruction formats opcode always the first 6 bits Smaller is faster limited instruction set limited number. Jakub Szefer Principles of Secure Processor Architecture Design Morgan Claypool Publishers October 2018.
 Source: sciencedirect.com
Source: sciencedirect.com
Program 930 1000 Secure Processor Architectures 30 min 1010. Margaret Martonosi Princeton UniversityPrinciples of Secure Processor Architecture Design Jakub Szefer Yale. The tutorial will be given on. Principles of Secure Processor Architecture Design Jakub Szefer Yale University With growing interest in computer security and the protection of the code and data which execute on commodity computers the amount of hardware security features in todays processor. Web page for the tutorial on Principles of Secure Processor Architecture Design which will be presented at ASPLOS 2019 in Providence RI on April 14th 2019.
 Source: za.pinterest.com
Source: za.pinterest.com
Secure processor architecture research is concerned with exploring and design. The tutorial will be given on. With growing interest in computer security and the protection of the code and data which execute on commodity computers. Secure the weakest link 2. Grant least privilege 5.
 Source: pinterest.com
Source: pinterest.com
Grant least privilege 5.
 Source: pinterest.com
Source: pinterest.com
Program 930 1000 Secure Processor Architectures 30 min 1010.
 Source: pinterest.com
Source: pinterest.com
Principles of Secure Processor Architecture Design Jakub Szefer Yale University With growing interest in computer security and the protection of the code and data which execute on commodity computers the amount of hardware security features in todays processor. Secure processor architecture research is concerned with exploring and design. Secure processor architecture research is concerned with exploring and design. Principles of Secure Processor Architecture Design Jakub Szefer Series Editor. Defend in depth 3.
 Source: amazon.com
Source: amazon.com
Secure processor architecture research is concerned with exploring and design.
 Source: in.pinterest.com
Source: in.pinterest.com
I am pleased to announce the latest title in Morgan Claypools series on Computer Architecture.
 Source: pinterest.com
Source: pinterest.com
Program 930 1000 Secure Processor Architectures 30 min 1010. Margaret Martonosi Princeton UniversityPrinciples of Secure Processor Architecture Design Jakub Szefer Yale. Principles of Secure Processor Architecture Design Synthesis Lectures on Computer Architecture By 作者. Grant least privilege 5. This book aims to give readers insights into the principles behind the design of academic and commercial secure processor architectures.
 Source: mdpi.com
Source: mdpi.com
This book gives readers insights into the principles behind the design of academic and commercial secure processor architectures. The book also presents existing research challenges and potential new research directions. Request PDF Principles of Secure Processor Architecture Design With growing interest in computer security and the protection of the code and data which execute on commodity computers. Control access 8Assume secrets not safe 9. Principles of Secure Processor Architecture Design Jakub Szefer Yale University With growing interest in computer security and the protection of the code and data which execute on commodity computers the amount of hardware security features in todays processor.
 Source: pinterest.com
Source: pinterest.com
This book aims to give readers insights into the principles behind the design of academic and commercial secure processor architectures. Principles of Secure Processor Architecture Design Jakub Szefer Yale University. Secure processor architecture research is concerned with exploring and design. Jakub Szefer Principles of Secure Processor Architecture Design Morgan Claypool Publishers October 2018. The book also presents existing research challenges and potential new research directions.
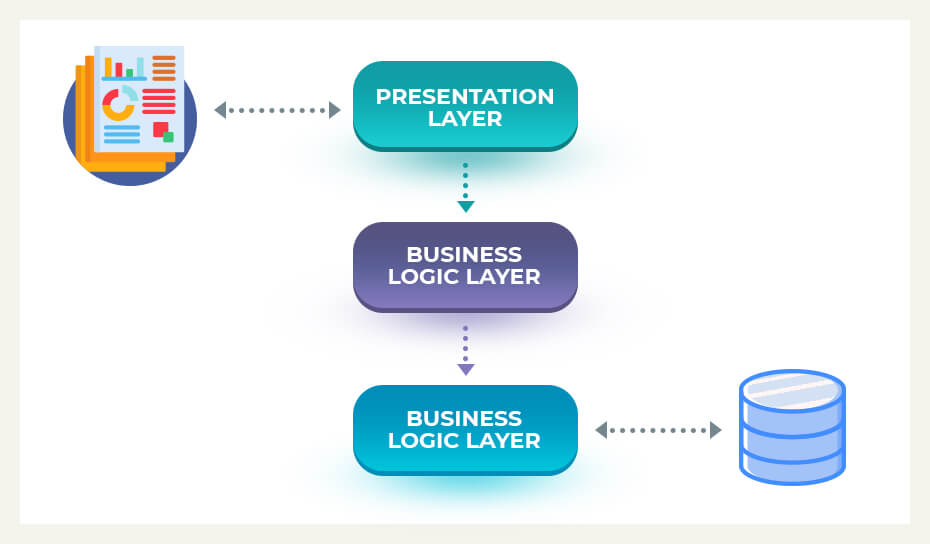 Source: heliossolutions.co
Source: heliossolutions.co
Good security and privacy do not have to be endlessly expensive. The book also presents existing research challenges and potential new research directions. Secure the weakest link 2. Principles of Secure Processor Architecture Design Jakub Szefer Yale University With growing interest in computer security and the protection of the code and data which execute on commodity computers the amount of hardware security features in todays processor. Control access 8Assume secrets not safe 9.
 Source: pinterest.com
Source: pinterest.com
Secure the weakest link 2. Jakub Szefer ISBN-10 书号. Of Electrical Engineering Yale University ASPLOS 2019 April 14th 2019 Tutorial on Principles of Secure Processor Architecture DesignTutorial Outline 830 900 Secure. It details the five basic principles needed for secure processor architecture design. This book aims to give readers insights into the principles behind the design of academic and commercial secure processor architectures.
This site is an open community for users to submit their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site helpful, please support us by sharing this posts to your preference social media accounts like Facebook, Instagram and so on or you can also save this blog page with the title principles of secure processor architecture design pdf by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.






