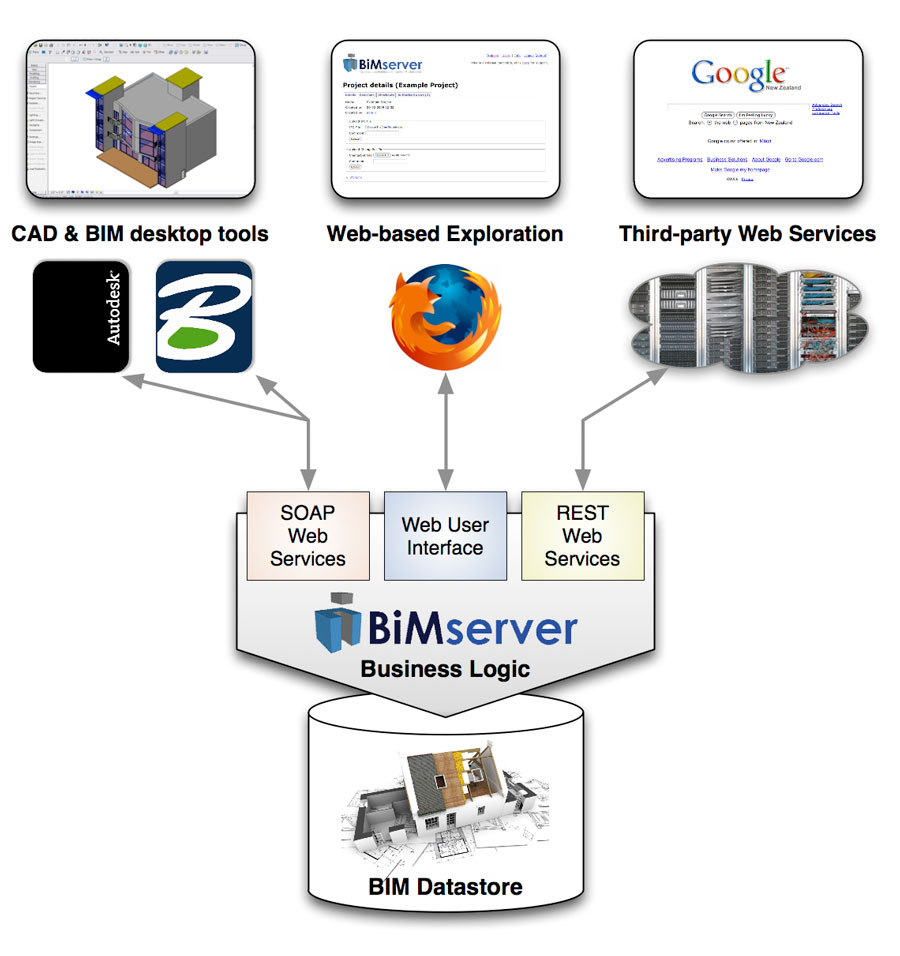
Your Secure architecture design principles images are available in this site. Secure architecture design principles are a topic that is being searched for and liked by netizens now. You can Get the Secure architecture design principles files here. Find and Download all free photos and vectors.
If you’re searching for secure architecture design principles images information linked to the secure architecture design principles interest, you have pay a visit to the ideal blog. Our site always provides you with hints for refferencing the maximum quality video and image content, please kindly hunt and find more enlightening video content and images that match your interests.
Secure Architecture Design Principles. Principles define effective practices that are applicable primarily to architecture-level software decisions and are recommended regardless of the platform or language of the software. Secure by design SBD in software engineering means that software products have been designed from the foundation to be secure. If you look at the Secure Design Principles of the UK National Cyber Security Centre something I strongly recommend reading you will see this mentioned in their first principle Establish the context before designing a system. Implement the principle of least privilege and enforce separation of duties with appropriate authorization for each interaction with your AWS resources.
 Pliances Rather Than Deployed To Every Microservice Software Architecture Design Proxy Server Gateway From pinterest.com
Pliances Rather Than Deployed To Every Microservice Software Architecture Design Proxy Server Gateway From pinterest.com
Hash treealso called MerkleTree is a logical three structure typically a binary tree where two child nodes are hashed together to create parent node. Principles of Secure Design Compartmentalization Isolation Principle of least privilege Defense in depth Use more than one security mechanism Secure the weakest link Fail securely. Principles define effective practices that are applicable primarily to architecture-level software decisions and are recommended regardless of the platform or language of the software. Hover over the various areas of the graphic and click inside the Box for additional information. Asset clarification Before developing any security strategies it is essential to identify. Establish the context before designing a system Before you can create a secure system design you need to have a good understanding of the.
Alternate security tactics and patterns are considered at the beginning of a software design and the best are selected and enforced by the architecture and they are used as guiding principles for developers.
Principles define effective practices that are applicable primarily to architecture-level software decisions and are recommended regardless of the platform or language of the software. The root node is a hash that depends on value of all the leaf nodes. Principles define effective practices that are applicable primarily to architecture-level software decisions and are recommended regardless of the platform or language of the software. Unlike traditional processor architecture research that focuses on performance efficiency and energy as the first-order design objectives secure processor architecture design has security as the first-order design objective while still keeping the others as important design aspects that need to be considered. Recent attacks such a Specter and Meltdown have revealed fundamental vulnerabilities in. Building a Secure Architecture A Deep-Dive into Security Design PrinciplesA resilient architecture acts as a strong foundation for secure applications.
 Source: br.pinterest.com
Source: br.pinterest.com
Principles of Secure Design Compartmentalization Isolation Principle of least privilege Defense in depth Use more than one security mechanism Secure the weakest link Fail securely. Principles of Secure Design Compartmentalization Isolation Principle of least privilege Defense in depth Use more than one security mechanism Secure the weakest link Fail securely. Hash treealso called MerkleTree is a logical three structure typically a binary tree where two child nodes are hashed together to create parent node. PrinciplesofSecureDesign Compartmentalizaon Isolaon Principleofleastprivilege Defenseindepth Usemorethanonesecuritymechanism Securetheweakestlink Failsecurely. Five principles for the design of cyber secure systems 1.
 Source: pinterest.com
Source: pinterest.com
Implement a strong identity foundation. Hash treealso called MerkleTree is a logical three structure typically a binary tree where two child nodes are hashed together to create parent node. Establish the context before designing a system Before you can create a secure system design you need to have a good understanding of the. Implement the principle of least privilege and enforce separation of duties with appropriate authorization for each interaction with your AWS resources. Hover over the various areas of the graphic and click inside the Box for additional information.
 Source: pinterest.com
Source: pinterest.com
Recent attacks such a Specter and Meltdown have revealed fundamental vulnerabilities in. Implement a strong identity foundation. The OWASP security design principles are as follows. Their work provides the foundation needed for designing and implementing secure software systems. Principles of Secure Design Compartmentalization Isolation Principle of least privilege Defense in depth Use more than one security mechanism Secure the weakest link Fail securely.
 Source: co.pinterest.com
Source: co.pinterest.com
Five principles for the design of cyber secure systems 1. In the cloud there are a number of principles that can help you strengthen your workload security. Implement the principle of least privilege and enforce separation of duties with appropriate authorization for each interaction with your AWS resources. Their work provides the foundation needed for designing and implementing secure software systems. Hash treealso called MerkleTree is a logical three structure typically a binary tree where two child nodes are hashed together to create parent node.
 Source: pinterest.com
Source: pinterest.com
Principles of Secure Processor Architecture Design. Principles define effective practices that are applicable primarily to architecture-level software decisions and are recommended regardless of the platform or language of the software. These principles are intended to help ensure that the networks and technologies which underpin modern life are designed and built securely. This course focuses on architecture-level vulnerabilities secure architecture design principles and applications to modern microprocessors. Establish the context before designing a system Before you can create a secure system design you need to have a good understanding of the.
 Source: pinterest.com
Source: pinterest.com
Implement a strong identity foundation. Building a Secure Architecture A Deep-Dive into Security Design PrinciplesA resilient architecture acts as a strong foundation for secure applications. This secure architecture design is the result of an evolutionary process of technology advancement and increasing cyber vulnerability presented in the Recommended Practice document Control Systems Defense in Depth Strategies. Implement the principle of least privilege and enforce separation of duties with appropriate authorization for each interaction with your AWS resources. Hover over the various areas of the graphic and click inside the Box for additional information.
 Source: pinterest.com
Source: pinterest.com
Building a Secure Architecture A Deep-Dive into Security Design PrinciplesA resilient architecture acts as a strong foundation for secure applications. Principles of Secure Design Compartmentalization Isolation Principle of least privilege Defense in depth Use more than one security mechanism Secure the weakest link Fail securely. Principles define effective practices that are applicable primarily to architecture-level software decisions and are recommended regardless of the platform or language of the software. Camouflaging can be added to almost any design as it is at the level of logic gates. If you look at the Secure Design Principles of the UK National Cyber Security Centre something I strongly recommend reading you will see this mentioned in their first principle Establish the context before designing a system.
 Source: pinterest.com
Source: pinterest.com
Implement a strong identity foundation. This course focuses on architecture-level vulnerabilities secure architecture design principles and applications to modern microprocessors. Implement the principle of least privilege and enforce separation of duties with appropriate authorization for each interaction with your AWS resources. Principles of Secure Design Compartmentalization Isolation Principle of least privilege Defense in depth Use more than one security mechanism Secure the weakest link Fail securely Keep it simple. This secure architecture design is the result of an evolutionary process of technology advancement and increasing cyber vulnerability presented in the Recommended Practice document Control Systems Defense in Depth Strategies.
 Source: pinterest.com
Source: pinterest.com
Their work provides the foundation needed for designing and implementing secure software systems. If you look at the Secure Design Principles of the UK National Cyber Security Centre something I strongly recommend reading you will see this mentioned in their first principle Establish the context before designing a system. Hover over the various areas of the graphic and click inside the Box for additional information. Hash treealso called MerkleTree is a logical three structure typically a binary tree where two child nodes are hashed together to create parent node. Building a Secure Architecture A Deep-Dive into Security Design PrinciplesA resilient architecture acts as a strong foundation for secure applications.
 Source: in.pinterest.com
Source: in.pinterest.com
Principles of Secure Design Compartmentalization Isolation Principle of least privilege Defense in depth Use more than one security mechanism Secure the weakest link Fail securely. Recent attacks such a Specter and Meltdown have revealed fundamental vulnerabilities in. Implement the principle of least privilege and enforce separation of duties with appropriate authorization for each interaction with your AWS resources. In the cloud there are a number of principles that can help you strengthen your workload security. Hash treealso called MerkleTree is a logical three structure typically a binary tree where two child nodes are hashed together to create parent node.
 Source: pinterest.com
Source: pinterest.com
In the cloud there are a number of principles that can help you strengthen your workload security. Principles of Secure Design Compartmentalization Isolation Principle of least privilege Defense in depth Use more than one security mechanism Secure the weakest link Fail securely. If you look at the Secure Design Principles of the UK National Cyber Security Centre something I strongly recommend reading you will see this mentioned in their first principle Establish the context before designing a system. In the cloud there are a number of principles that can help you strengthen your workload security. Tutorial on Principles of Secure Processor Architecture Design Jakub Szeferver.
 Source: pinterest.com
Source: pinterest.com
This secure architecture design is the result of an evolutionary process of technology advancement and increasing cyber vulnerability presented in the Recommended Practice document Control Systems Defense in Depth Strategies. The OWASP security design principles are as follows. Alternate security tactics and patterns are considered at the beginning of a software design and the best are selected and enforced by the architecture and they are used as guiding principles for developers. Asset clarification Before developing any security strategies it is essential to identify. Secure by design SBD in software engineering means that software products have been designed from the foundation to be secure.
 Source: pinterest.com
Source: pinterest.com
The root node is a hash that depends on value of all the leaf nodes. Implement the principle of least privilege and enforce separation of duties with appropriate authorization for each interaction with your AWS resources. Alternate security tactics and patterns are considered at the beginning of a software design and the best are selected and enforced by the architecture and they are used as guiding principles for developers. Principles of Secure Processor Architecture Design. Camouflaging can be added to almost any design as it is at the level of logic gates.
 Source: pinterest.com
Source: pinterest.com
Implement the principle of least privilege and enforce separation of duties with appropriate authorization for each interaction with your AWS resources. The OWASP security design principles are as follows. If you look at the Secure Design Principles of the UK National Cyber Security Centre something I strongly recommend reading you will see this mentioned in their first principle Establish the context before designing a system. Establish the context before designing a system Before you can create a secure system design you need to have a good understanding of the. Secure by design SBD in software engineering means that software products have been designed from the foundation to be secure.
 Source: pinterest.com
Source: pinterest.com
Hover over the various areas of the graphic and click inside the Box for additional information. Asset clarification Before developing any security strategies it is essential to identify. This secure architecture design is the result of an evolutionary process of technology advancement and increasing cyber vulnerability presented in the Recommended Practice document Control Systems Defense in Depth Strategies. Five principles for the design of cyber secure systems 1. These principles are intended to help ensure that the networks and technologies which underpin modern life are designed and built securely.
 Source: pinterest.com
Source: pinterest.com
In the cloud there are a number of principles that can help you strengthen your workload security. Implement the principle of least privilege and enforce separation of duties with appropriate authorization for each interaction with your AWS resources. With growing interest in computer security and the protection of the code and data which execute on commodity computers the amount of hardware security features in todays processors has increased significantly over the recent years. This course focuses on architecture-level vulnerabilities secure architecture design principles and applications to modern microprocessors. Building a Secure Architecture A Deep-Dive into Security Design PrinciplesA resilient architecture acts as a strong foundation for secure applications.
 Source: pinterest.com
Source: pinterest.com
This secure architecture design is the result of an evolutionary process of technology advancement and increasing cyber vulnerability presented in the Recommended Practice document Control Systems Defense in Depth Strategies. Principles of Secure Processor Architecture Design. Alternate security tactics and patterns are considered at the beginning of a software design and the best are selected and enforced by the architecture and they are used as guiding principles for developers. The root node is a hash that depends on value of all the leaf nodes. Implement the principle of least privilege and enforce separation of duties with appropriate authorization for each interaction with your AWS resources.
 Source: pinterest.com
Source: pinterest.com
Tutorial on Principles of Secure Processor Architecture Design Jakub Szeferver. In the cloud there are a number of principles that can help you strengthen your workload security. The OWASP security design principles are as follows. Principles of Secure Design Compartmentalization Isolation Principle of least privilege Defense in depth Use more than one security mechanism Secure the weakest link Fail securely. Principles define effective practices that are applicable primarily to architecture-level software decisions and are recommended regardless of the platform or language of the software.
This site is an open community for users to share their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site serviceableness, please support us by sharing this posts to your own social media accounts like Facebook, Instagram and so on or you can also save this blog page with the title secure architecture design principles by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.