Your Secure software architecture design implementation and assurance images are available in this site. Secure software architecture design implementation and assurance are a topic that is being searched for and liked by netizens now. You can Get the Secure software architecture design implementation and assurance files here. Find and Download all free images.
If you’re looking for secure software architecture design implementation and assurance images information connected with to the secure software architecture design implementation and assurance interest, you have visit the right site. Our site always gives you suggestions for seeing the highest quality video and image content, please kindly surf and locate more informative video articles and graphics that match your interests.
Secure Software Architecture Design Implementation And Assurance. Design Review Implementation Review Policy Compliance Security Testing Governance Construction Operations Software Development The Software Assurance Maturity Model SAMM is an open framework to help for software. Secure software architecture and design. Automate the deployment process over all stages and. While many of the attacks on the Internet today are merely a nuisance there is.
 Automated Software Development Tools For Improving Iot Device Security Software Development Iot Automation From pinterest.com
Automated Software Development Tools For Improving Iot Device Security Software Development Iot Automation From pinterest.com
Six new secure design patterns were added to the report in an October 2009 update. VP of Security Architecture WhiteHat Security 16 years of web-based database-driven software development and analysis experience Secure coding educatorauthor Kamaaina. Secure Software Architecture Design Implementation and Assurance Autorzy Seacord Dietrich Plakosh Treść Zawartość Warianty tytułu Języki publikacji Abstrakty Society s increased dependency on networked software. Software assurance Software assurance is especially impor-tant for organizations critical to public safety and economic and national security. Deployment processes are fully documented. Learn vocabulary terms and more with flashcards games and other study tools.
For maximum benefit these practices should be integrated into all stages of software development and maintenance.
Formalize the deployment process and secure the used tooling and processes. Deployment processes include security verification milestones. 2 SECURE SOFTWARE DEVELOPMENT LIFE CYCLE PROCES SES. Accounts for 14 of the CSSOP exam. Conceptual Design and Implementation of a Secure Bootchain based on the High Assurance Boot HABv4 Architecture of the NXP platform June 2019 DOI. It is a set of development practices for strengthening security and compliance.
 Source: pinterest.com
Source: pinterest.com
Software assurance SwA is defined as the level of confidence that software is free from vulnerabilities either intentionally designed into the software or accidentally inserted at anytime during its life cycle and that the software. Software assurance encompasses the development and implementation of methods and processes for ensuring that software functions as intended and is free of design defects and implementation flaws. SSADIA stands for Secure Software Architecture Design Implementation and. SSADIA is defined as Secure Software Architecture Design Implementation and Assurance rarely. The BSA Framework for Secure Software is intended to establish an approach to software security that is flexible adaptable outcome-focused risk-based cost-effective and repeatable.
 Source: pinterest.com
Source: pinterest.com
The BSA Framework for Secure Software is intended to establish an approach to software security that is flexible adaptable outcome-focused risk-based cost-effective and repeatable. These users require a high level of confidence that commercial software is as secure. In 2008 the Software. OWASP SAMM supports the complete software lifecycle including development and acquisition. Security assurance usually also includes activities for the requirements design implementation testing release and maintenance phases of an SDLC.
 Source: pinterest.com
Source: pinterest.com
These users require a high level of confidence that commercial software is as secure. SSADIA is defined as Secure Software Architecture Design Implementation and Assurance rarely. Software assurance encompasses the development and implementation of methods and processes for ensuring that software functions as intended and is free of design defects and implementation flaws. Learn vocabulary terms and more with flashcards games and other study tools. For maximum benefit these practices should be integrated into all stages of software development and maintenance.
 Source: dataversity.net
Source: dataversity.net
OWASP SAMM supports the complete software lifecycle including development and acquisition. Design Review Implementation Review Policy Compliance Security Testing Governance Construction Operations Software Development The Software Assurance Maturity Model SAMM is an open framework to help for software. In 2008 the Software. VP of Security Architecture WhiteHat Security 16 years of web-based database-driven software development and analysis experience Secure coding educatorauthor Kamaaina. 2 SECURE SOFTWARE DEVELOPMENT LIFE CYCLE PROCES SES.
 Source: in.pinterest.com
Source: in.pinterest.com
Secure Software Architecture Design Implementation and Assurance Autorzy Seacord Dietrich Plakosh Treść Zawartość Warianty tytułu Języki publikacji Abstrakty Society s increased dependency on networked software. User request mods managers do costbenefit analysis devs prioritize tasks 2. A big part of secure software architecture and design. While many of the attacks on the Internet today are merely a nuisance there is. Security assurance usually also includes activities for the requirements design implementation testing release and maintenance phases of an SDLC.
 Source: ptsecurity.com
Source: ptsecurity.com
Accounts for 14 of the CSSOP exam. Software assurance SwA is defined as the level of confidence that software is free from vulnerabilities either intentionally designed into the software or accidentally inserted at anytime during its life cycle and that the software. A big part of secure software architecture and design. Software assurance encompasses the development and implementation of methods and processes for ensuring that software functions as intended and is free of design defects and implementation flaws. Deployment processes include security verification milestones.
 Source: pinterest.com
Source: pinterest.com
Secure Software Architecture Design Implementation and Assurance Autorzy Seacord Dietrich Plakosh Treść Zawartość Warianty tytułu Języki publikacji Abstrakty Society s increased dependency on networked software. There is a ready-made solution that provides a structured approach to application securitythe secure development lifecycle SDL. Introduce basic protection measures to limit access to your production secrets. The patterns were derived by generalizing existing best security design practices and by extending existing design patterns with security-specific functionality. Deployment processes are fully documented.
 Source: synopsys.com
Source: synopsys.com
A big part of secure software architecture and design. Design Review Implementation Review Policy Compliance Security Testing Governance Construction Operations Software Development The Software Assurance Maturity Model SAMM is an open framework to help for software. Deployment processes include security verification milestones. OWASP SAMM supports the complete software lifecycle including development and acquisition. Formalize the deployment process and secure the used tooling and processes.
 Source: pinterest.com
Source: pinterest.com
The BSA Framework for Secure Software is intended to establish an approach to software security that is flexible adaptable outcome-focused risk-based cost-effective and repeatable. The BSA Framework for Secure Software is intended to establish an approach to software security that is flexible adaptable outcome-focused risk-based cost-effective and repeatable. The secure software architecture design implementation and assurance minitrack focuses on the research and automation required to develop secure software systems that do not compromise other. Introduce basic protection measures to limit access to your production secrets. Is understanding who might target your app.
 Source: pinterest.com
Source: pinterest.com
VP of Security Architecture WhiteHat Security 16 years of web-based database-driven software development and analysis experience Secure coding educatorauthor Kamaaina. Deployment processes are fully documented. The patterns were derived by generalizing existing best security design practices and by extending existing design patterns with security-specific functionality. While many of the attacks on the Internet today are merely a nuisance there is. Architecture design or implementation.
 Source: pinterest.com
Source: pinterest.com
VP of Security Architecture WhiteHat Security 16 years of web-based database-driven software development and analysis experience Secure coding educatorauthor Kamaaina. It is a set of development practices for strengthening security and compliance. A big part of secure software architecture and design. Learn vocabulary terms and more with flashcards games and other study tools. Introduce basic protection measures to limit access to your production secrets.
 Source: pinterest.com
Source: pinterest.com
SSADIA is defined as Secure Software Architecture Design Implementation and Assurance rarely. Software assurance SwA is defined as the level of confidence that software is free from vulnerabilities either intentionally designed into the software or accidentally inserted at anytime during its life cycle and that the software. The mission of OWASP Software Assurance Maturity Model SAMM is to be the prime maturity model for software assurance that provides an effective and measurable way for all types of organizations to analyze and improve their software security posture. OWASP SAMM supports the complete software lifecycle including development and acquisition. Deployment processes include security verification milestones.
 Source: pinterest.com
Source: pinterest.com
SSADIA is defined as Secure Software Architecture Design Implementation and Assurance rarely. Architecture design or implementation. Deployment processes include security verification milestones. Societys increased dependency on networked software systems has been matched by an increase in the number of attacks aimed at these systems. VP of Security Architecture WhiteHat Security 16 years of web-based database-driven software development and analysis experience Secure coding educatorauthor Kamaaina.
 Source: pinterest.com
Source: pinterest.com
Learn vocabulary terms and more with flashcards games and other study tools. Automate the deployment process over all stages and. Formalize the deployment process and secure the used tooling and processes. Six new secure design patterns were added to the report in an October 2009 update. Conceptual Design and Implementation of a Secure Bootchain based on the High Assurance Boot HABv4 Architecture of the NXP platform June 2019 DOI.
 Source: ptsecurity.com
Source: ptsecurity.com
Secure software architecture and design. The secure software architecture design implementation and assurance minitrack focuses on the research and automation required to develop secure software systems that do not compromise other. Accounts for 14 of the CSSOP exam. Architecture design or implementation. Software assurance encompasses the development and implementation of methods and processes for ensuring that software functions as intended and is free of design defects and implementation flaws.
 Source: pinterest.com
Source: pinterest.com
The BSA Framework for Secure Software is intended to establish an approach to software security that is flexible adaptable outcome-focused risk-based cost-effective and repeatable. The secure software architecture design implementation and assurance minitrack focuses on the research and automation required to develop secure software systems that do not compromise other. Is understanding who might target your app. Learn vocabulary terms and more with flashcards games and other study tools. While many of the attacks on the Internet today are merely a nuisance there is.
 Source: onlinelibrary.wiley.com
Source: onlinelibrary.wiley.com
Accounts for 14 of the CSSOP exam. Architecture design or implementation. In 2008 the Software. Software assurance SwA is defined as the level of confidence that software is free from vulnerabilities either intentionally designed into the software or accidentally inserted at anytime during its life cycle and that the software. It is a set of development practices for strengthening security and compliance.
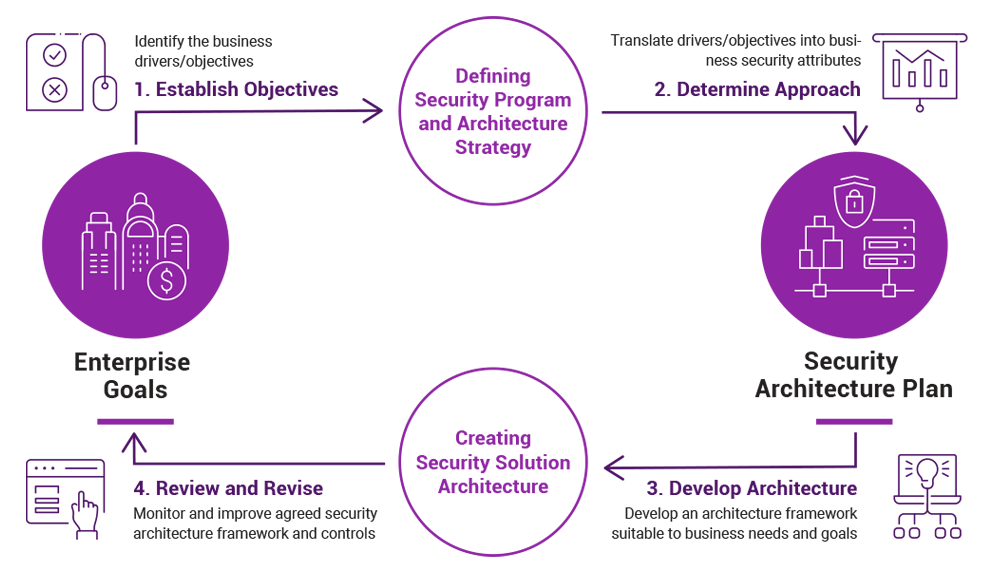
For maximum benefit these practices should be integrated into all stages of software development and maintenance. Automate the deployment process over all stages and. Software assurance Software assurance is especially impor-tant for organizations critical to public safety and economic and national security. For maximum benefit these practices should be integrated into all stages of software development and maintenance. Six new secure design patterns were added to the report in an October 2009 update.
This site is an open community for users to submit their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site value, please support us by sharing this posts to your own social media accounts like Facebook, Instagram and so on or you can also save this blog page with the title secure software architecture design implementation and assurance by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.






