Your Security architecture design in cloud computing slideshare images are available in this site. Security architecture design in cloud computing slideshare are a topic that is being searched for and liked by netizens today. You can Download the Security architecture design in cloud computing slideshare files here. Find and Download all royalty-free vectors.
If you’re searching for security architecture design in cloud computing slideshare images information connected with to the security architecture design in cloud computing slideshare topic, you have come to the right blog. Our site frequently gives you hints for seeing the maximum quality video and image content, please kindly surf and find more informative video content and graphics that match your interests.
Security Architecture Design In Cloud Computing Slideshare. Security architecture and design looks at how information security controls and safeguards are implemented in IT systems in order to protect the confidentiality integrity and availability of the data that are used processed and stored. While there are variations of cloud architecture based on what youre trying to do most clouds require hardware middleware management and automation software. Businesses used cloud infrastructures to work with these applications. A structured support practice aimed at detemining security requirements with all stakeholders and designing solutions to meet those requirements.
 I Pinimg Com Originals 70 D7 B0 70d7b0f808a8644 From in.pinterest.com
I Pinimg Com Originals 70 D7 B0 70d7b0f808a8644 From in.pinterest.com
Adopting new technology can be a challenge but you can save time and rapidly move to the cloud using reference architectures that are based on our expert teams interaction with. Confidentiality integrity and availability. Explain Security Monitoring in Cloud Computing Security monitoring in cloud computing or cloud monitoring is a software and process package. SAFE Architecture Guide 9 Places in the Network. 247 service availability and overall performance of the servers websites applications etc is ensured by manualautomated monitoring management solutions. Cloud Computing leverages many technologies SOA virtualization Web 20.
Not only cloud services are disrupted by virus attacks even miss-configuration issues as well as improper user policy settings can lead to errors.
Security Architecture of Cloud Computing J. Cloud computing security architecture relies on having visibility throughout the cloud network with performance management capabilities. Enterprise Security Architecture. User experience design UX is also important in order to create a navigable online experience. Britto Ramesh Kumar2 1Head Dept. Moreover the cloud security architecture should be aligned with the technology architecture as well as the organizational principles.
 Source: in.pinterest.com
Source: in.pinterest.com
Cloud Computing security architecture is categorized into frontend and backend along with an amalgamation of the event-driven architecture and the service-oriented architecture in Cloud Computing. The specific terms of security responsibility may vary between services and are sometimes up for negotiation with the service provider. Secure Cloud Business Flows June 2019 Functional Controls Functional Controls are common security considerations that are derived from the technical aspects of theflows. Cloud Computing security architecture is categorized into frontend and backend along with an amalgamation of the event-driven architecture and the service-oriented architecture in Cloud Computing. Confidentiality integrity and availability.
 Source: co.pinterest.com
Source: co.pinterest.com
It also inherits their security issues which we discuss here identifying the main vulnerabilities in this kind of. Understanding each capability will help guide your efforts in planning a. SOA Grid and Clou SOA Grid and Clou Slideshare uses cookies to improve functionality and performance and to provide you with relevant advertising. Businesses used cloud infrastructures to work with these applications. Moreover the cloud security architecture should be aligned with the technology architecture as well as the organizational principles.
 Source: pinterest.com
Source: pinterest.com
Of Computer Science Soka Ikeda College of Arts and Science for Women Chennai 2Assistant Professor Dept. This paper focuses on. Figure - Cloud Computing Architecture. Secure cloud computing architecture encompasses three core capabilities. Understanding each capability will help guide your efforts in planning a.
 Source: pinterest.com
Source: pinterest.com
Frontend is a userclient-facing architecture. While there are variations of cloud architecture based on what youre trying to do most clouds require hardware middleware management and automation software. Frameworks and Design Authority. Understanding each capability will help guide your efforts in planning a. 753 Cloud Architecture Design Challenges 76 Cloud Security and Trust Management 42 761 Cloud Security Defense Strategies 762 Distributed IntrusionAnomaly Detection 763 Reputation-Guided 77 References and.
 Source: slideshare.net
Source: slideshare.net
Secure cloud computing architecture encompasses three core capabilities. Cloud computing security architecture relies on having visibility throughout the cloud network with performance management capabilities. SaaS Cloud Computing Security Architecture SaaS services provide access to software applications and data through a browser. 753 Cloud Architecture Design Challenges 76 Cloud Security and Trust Management 42 761 Cloud Security Defense Strategies 762 Distributed IntrusionAnomaly Detection 763 Reputation-Guided 77 References and. Security Architecture of Cloud Computing J.
 Source: slideshare.net
Source: slideshare.net
The security issues at various levels of cloud computing environment is identified in this paper and categorized based on cloud computing architecture. Understanding each capability will help guide your efforts in planning a. Secure cloud computing architecture encompasses three core capabilities. The security issues at various levels of cloud computing environment is identified in this paper and categorized based on cloud computing architecture. Not only cloud services are disrupted by virus attacks even miss-configuration issues as well as improper user policy settings can lead to errors.
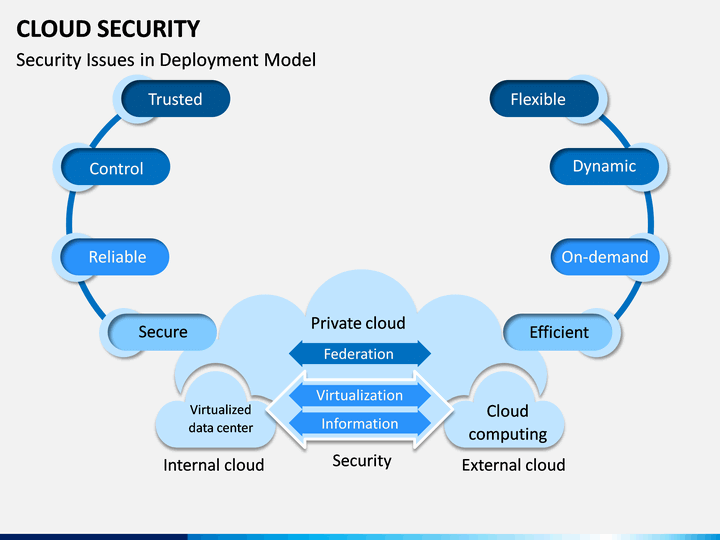 Source: sketchbubble.com
Source: sketchbubble.com
Enterprise Security Architecture. Unlike subscription-based pricing models the clouds payment structure enables the user to subscribe to vendor services and cloud infrastructures are paid on a pay-per-use basis. Explain Security Monitoring in Cloud Computing Security monitoring in cloud computing or cloud monitoring is a software and process package. Figure - Cloud Computing Architecture. User experience design UX is also important in order to create a navigable online experience.
 Source: in.pinterest.com
Source: in.pinterest.com
Figure - Cloud Computing Architecture. Secure cloud computing architecture encompasses three core capabilities. While there are variations of cloud architecture based on what youre trying to do most clouds require hardware middleware management and automation software. Various kind of Cloud computing architecture 4. SAFE Architecture Guide 9 Places in the Network.
 Source: pinterest.com
Source: pinterest.com
Britto Ramesh Kumar2 1Head Dept. Security architecture and design looks at how information security controls and safeguards are implemented in IT systems in order to protect the confidentiality integrity and availability of the data that are used processed and stored. Various kind of Cloud computing architecture 4. Confidentiality integrity and availability. Secure cloud computing architecture encompasses three core capabilities.
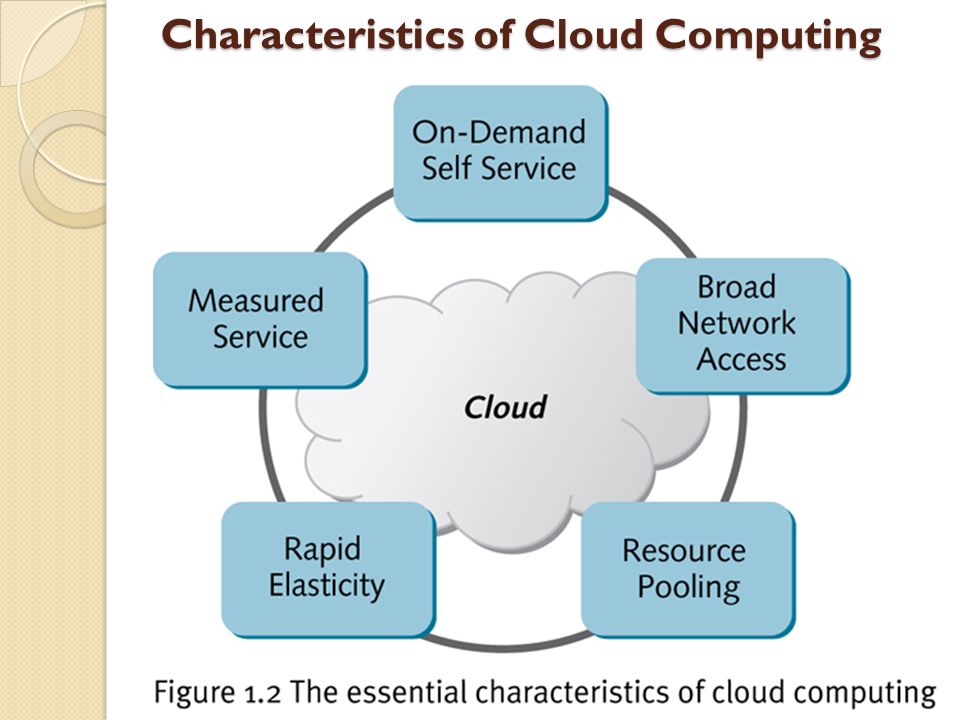 Source: slideplayer.com
Source: slideplayer.com
Secure Cloud Business Flows June 2019 Functional Controls Functional Controls are common security considerations that are derived from the technical aspects of theflows. Frontend is a userclient-facing architecture. Cloud computing security architecture relies on having visibility throughout the cloud network with performance management capabilities. A structured support practice aimed at detemining security requirements with all stakeholders and designing solutions to meet those requirements. Of Computer Science Soka Ikeda College of Arts and Science for Women Chennai 2Assistant Professor Dept.
 Source: slideshare.net
Source: slideshare.net
Businesses used cloud infrastructures to work with these applications. SaaS Cloud Computing Security Architecture SaaS services provide access to software applications and data through a browser. Cloud computing security architecture relies on having visibility throughout the cloud network with performance management capabilities. A structured technical vision to build standardised security designs and govern their implementation Architectural Support Services. Britto Ramesh Kumar2 1Head Dept.
 Source: pinterest.com
Source: pinterest.com
A structured support practice aimed at detemining security requirements with all stakeholders and designing solutions to meet those requirements. Businesses used cloud infrastructures to work with these applications. Frontend is a userclient-facing architecture. It also inherits their security issues which we discuss here identifying the main vulnerabilities in this kind of. Frameworks and Design Authority.
 Source: in.pinterest.com
Source: in.pinterest.com
Of Computer 1. Confidentiality integrity and availability. Frontend is a userclient-facing architecture. A structured technical vision to build standardised security designs and govern their implementation Architectural Support Services. Enterprise Security Architecture.
 Source: slideshare.net
Source: slideshare.net
Britto Ramesh Kumar2 1Head Dept. Understanding each capability will help guide your efforts in planning a. This paper focuses on. Businesses used cloud infrastructures to work with these applications. Secure cloud computing architecture encompasses three core capabilities.
 Source: slideshare.net
Source: slideshare.net
Adopting new technology can be a challenge but you can save time and rapidly move to the cloud using reference architectures that are based on our expert teams interaction with. A structured support practice aimed at detemining security requirements with all stakeholders and designing solutions to meet those requirements. The specific terms of security responsibility may vary between services and are sometimes up for negotiation with the service provider. 753 Cloud Architecture Design Challenges 76 Cloud Security and Trust Management 42 761 Cloud Security Defense Strategies 762 Distributed IntrusionAnomaly Detection 763 Reputation-Guided 77 References and. Businesses used cloud infrastructures to work with these applications.
 Source: hu.pinterest.com
Source: hu.pinterest.com
Security architecture and design looks at how information security controls and safeguards are implemented in IT systems in order to protect the confidentiality integrity and availability of the data that are used processed and stored. Of Computer Science Soka Ikeda College of Arts and Science for Women Chennai 2Assistant Professor Dept. SaaS Cloud Computing Security Architecture SaaS services provide access to software applications and data through a browser. The security issues at various levels of cloud computing environment is identified in this paper and categorized based on cloud computing architecture. Britto Ramesh Kumar2 1Head Dept.
 Source: in.pinterest.com
Source: in.pinterest.com
SAFE Architecture Guide 9 Places in the Network. Security requirements and Design. Secure Cloud Business Flows June 2019 Functional Controls Functional Controls are common security considerations that are derived from the technical aspects of theflows. Not only cloud services are disrupted by virus attacks even miss-configuration issues as well as improper user policy settings can lead to errors. Figure - Cloud Computing Architecture.
 Source: pinterest.com
Source: pinterest.com
Frameworks and Design Authority. Security Architecture of Cloud Computing J. Moreover the cloud security architecture should be aligned with the technology architecture as well as the organizational principles. User experience design UX is also important in order to create a navigable online experience. Understanding each capability will help guide your efforts in planning a.
This site is an open community for users to do sharing their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site serviceableness, please support us by sharing this posts to your preference social media accounts like Facebook, Instagram and so on or you can also bookmark this blog page with the title security architecture design in cloud computing slideshare by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.






