Your Security architecture design in cloud computing tutorialspoint images are available in this site. Security architecture design in cloud computing tutorialspoint are a topic that is being searched for and liked by netizens today. You can Get the Security architecture design in cloud computing tutorialspoint files here. Get all royalty-free photos.
If you’re looking for security architecture design in cloud computing tutorialspoint pictures information linked to the security architecture design in cloud computing tutorialspoint topic, you have come to the right blog. Our website frequently gives you suggestions for downloading the maximum quality video and picture content, please kindly hunt and locate more informative video content and graphics that match your interests.
Security Architecture Design In Cloud Computing Tutorialspoint. If you are looking to secure cloud storage for your company or organization youre likely to find a baffling number of options on the market. Cloud Computing provides us means by which we can access the applications as utilities over the internet. It may seem daunting at first to realize that your application. This paper focuses on.
 Kubernetes Architecture Tutorialspoint Port Forwarding Architecture Management From in.pinterest.com
Kubernetes Architecture Tutorialspoint Port Forwarding Architecture Management From in.pinterest.com
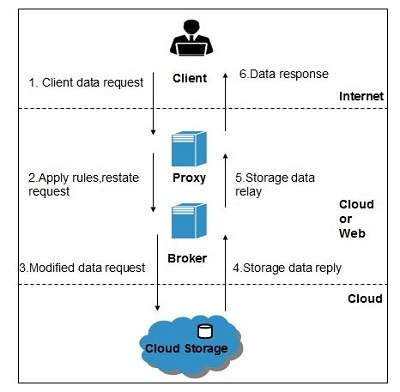
In cloud computing low bandwidth does not meet the desired computing performance. This tutorial will take you through a step-by. English Description Design customized software. An important aspect of your purchase decision is how the security. That acts as a Virtual Machine Manager. This paper presents a treatise about cloud computing security risk and attack we explained the definition of cloud computing and the P2P network in.
Kamal Kant Hiran Published on 20-Apr-2019 Language.
That acts as a Virtual Machine Manager. This tutorial will take you through a step-by. In cloud computing low bandwidth does not meet the desired computing performance. Of Computer Science Soka Ikeda College of Arts and Science for Women Chennai 2Assistant Professor Dept. English Description Unleash the power of cloud. That acts as a Virtual Machine Manager.
 Source: tutorialspoint.com
Source: tutorialspoint.com
It allows us to create configure and customize the business applications online. Britto Ramesh Kumar2 1Head Dept. Cloud Computing Using Salesforce Build and Customize Applications for your business using the Salesforce Platform Author. It may seem daunting at first to realize that your application. In cloud computing low bandwidth does not meet the desired computing performance.
 Source: tutorialspoint.com
Source: tutorialspoint.com
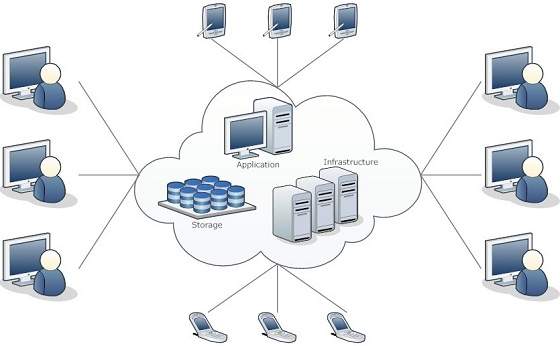
We can broadly divide the cloud architecture into two parts. Ashwini Kumar Raj Published on 02-Jan-2021 Language. Cloud Computing Master the Concepts Architecture and Applications with Real-world examples and Case studies Author. It may seem daunting at first to realize that your application. Cloud Computing provides us means by which we can access the applications as utilities over the internet.
 Source: tutorialspoint.com
Source: tutorialspoint.com
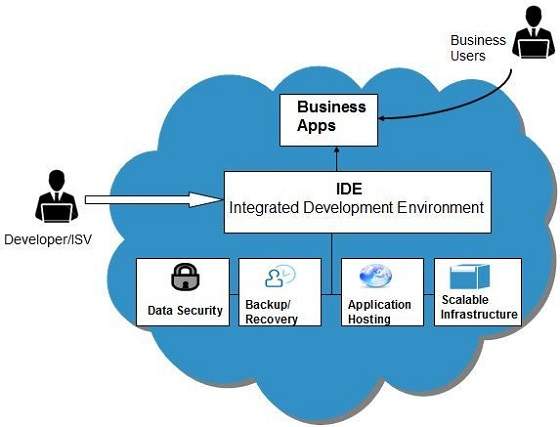
Of Computer 1. That acts as a Virtual Machine Manager. English Description Design customized software. Cloud Computing provides us means by which we can access the applications as utilities over the internet. Cloud computing security architecture relies on having visibility throughout the cloud network with performance management capabilities.
 Source: tutorialspoint.com
Source: tutorialspoint.com
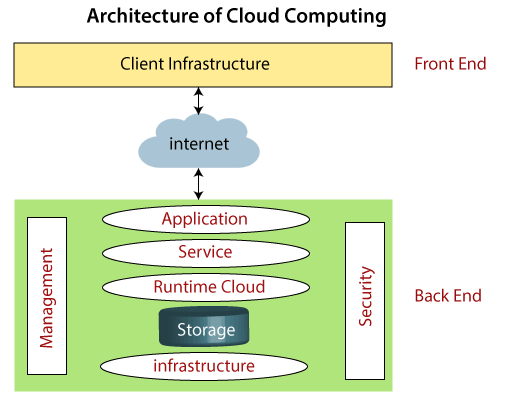
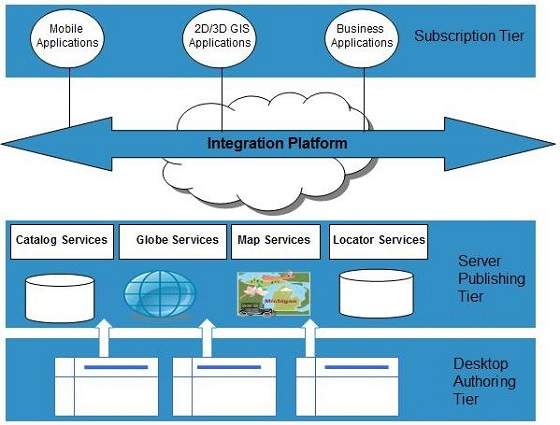
Front End Back End Each of the ends is connected through a network. It may seem daunting at first to realize that your application. Of Computer Science Soka Ikeda College of Arts and Science for Women Chennai 2Assistant Professor Dept. Security Architecture of Cloud Computing J. English Description Unleash the power of cloud.
 Source: tutorialspoint.com
Source: tutorialspoint.com
If you are looking to secure cloud storage for your company or organization youre likely to find a baffling number of options on the market. Cloud Computing architecture comprises of many cloud components which are loosely coupled. That acts as a Virtual Machine Manager. Cloud computing security architecture relies on having visibility throughout the cloud network with performance management capabilities. Security Architecture of Cloud Computing J.
 Source: tutorialspoint.com
Source: tutorialspoint.com
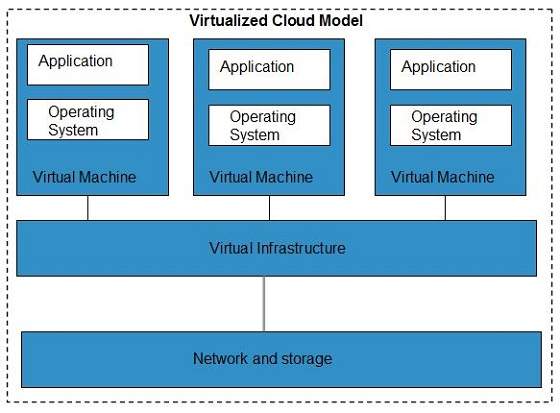
Britto Ramesh Kumar2 1Head Dept. Cloud infrastructure consists of servers storage devices network cloud management software deployment software and platform virtualization. Of Computer 1. Of Computer Science Soka Ikeda College of Arts and Science for Women Chennai 2Assistant Professor Dept. Ashwini Kumar Raj Published on 02-Jan-2021 Language.
 Source: tutorialspoint.com
Source: tutorialspoint.com
Cloud Computing security architecture is categorized into frontend and backend along with an amalgamation of the event-driven architecture and the service-oriented architecture in Cloud Computing. This paper focuses on. English Description Unleash the power of cloud. That acts as a Virtual Machine Manager. Front End Back End Each of the ends is connected through a network.
 Source: tutorialspoint.com
Source: tutorialspoint.com
Cloud Computing provides us means by which we can access the applications as utilities over the internet. Britto Ramesh Kumar2 1Head Dept. The security issues at various levels of cloud computing environment is identified in this paper and categorized based on cloud computing architecture. English Description Unleash the power of cloud. This tutorial will take you through a step-by.
 Source: javatpoint.com
Source: javatpoint.com
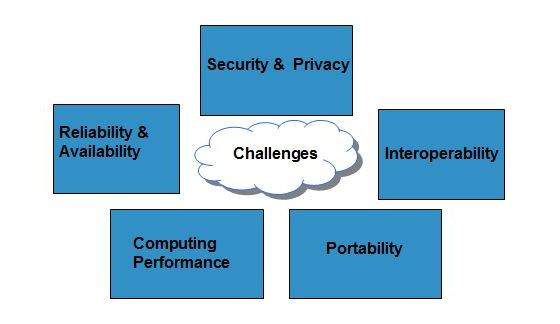
Portability This is another challenge to cloud computing that applications should easily be migrated from one cloud provider to another. Cloud Computing architecture comprises of many cloud components which are loosely coupled. Security and privacy issues can be overcome by employing encryption security hardware and security applications. Cloud Computing security architecture is categorized into frontend and backend along with an amalgamation of the event-driven architecture and the service-oriented architecture in Cloud Computing. This tutorial will take you through a step-by.
 Source: slideshare.net
Source: slideshare.net
Front End Back End Each of the ends is connected through a network. Of Computer 1. Hypervisor Hypervisor is a firmware or low-level program that acts as a Virtual Machine Manager. Security and privacy issues can be overcome by employing encryption security hardware and security applications. Cloud Computing architecture comprises of many cloud components which are loosely coupled.
 Source: tutorialspoint.com
Source: tutorialspoint.com
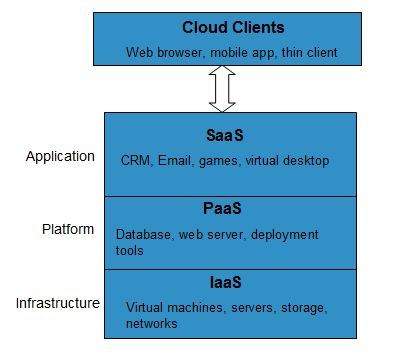
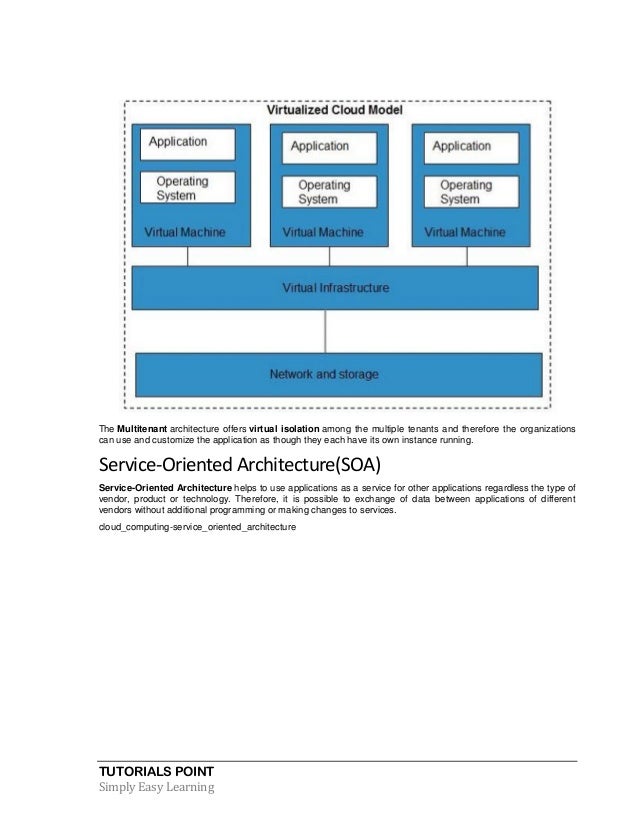
Cloud Computing Platform as a Service PaaS - Platform-as-a-Service offers the runtime environment for applications. Cloud Computing Architecture As we know cloud computing technology is used by both small and large organizations to store the information in cloud and access it from anywhere at anytime using the internet connection. It also offers development and deployment tools required to develop applications. Cloud computing is a form of outsourcing and you need a high level of trust in the entities youll be partnering with. If you are looking to secure cloud storage for your company or organization youre likely to find a baffling number of options on the market.
 Source: pinterest.com
Source: pinterest.com
Security Architecture of Cloud Computing J. Cloud computing security architecture implementing DES algorithm in cloud for data security Sep 2013 11-19 Varun Gandhi Sanchit Bansal Raveesh Kapoor Aakarsh Dhawan Varun Gandhi Sanchit Bansal. Security Architecture of Cloud Computing J. This paper presents a treatise about cloud computing security risk and attack we explained the definition of cloud computing and the P2P network in. Cloud computing security architecture relies on having visibility throughout the cloud network with performance management capabilities.
 Source: pinterest.com
Source: pinterest.com
Cloud Computing Using Salesforce Build and Customize Applications for your business using the Salesforce Platform Author. English Description Design customized software. It allows us to create configure and customize the business applications online. Ashwini Kumar Raj Published on 02-Jan-2021 Language. That acts as a Virtual Machine Manager.
 Source: tutorialspoint.com
Source: tutorialspoint.com
Cloud Computing Master the Concepts Architecture and Applications with Real-world examples and Case studies Author. Security Architecture of Cloud Computing J. Of Computer 1. Reliability and Availability Most of the businesses are dependent on services provided by third-party hence it is mandatory for the cloud systems to be reliable and robust. English Description Unleash the power of cloud.
 Source: ar.pinterest.com
Source: ar.pinterest.com
This tutorial will take you through a step-by. Cloud Computing Master the Concepts Architecture and Applications with Real-world examples and Case studies Author. Cloud computing security architecture relies on having visibility throughout the cloud network with performance management capabilities. This paper presents a treatise about cloud computing security risk and attack we explained the definition of cloud computing and the P2P network in. The security issues at various levels of cloud computing environment is identified in this paper and categorized based on cloud computing architecture.
 Source: tutorialspoint.com
Source: tutorialspoint.com
Portability This is another challenge to cloud computing that applications should easily be migrated from one cloud provider to another. Of Computer 1. Hypervisor Hypervisor is a firmware or low-level program that acts as a Virtual Machine Manager. Front End Back End Each of the ends is connected through a network. Cloud Computing security architecture is categorized into frontend and backend along with an amalgamation of the event-driven architecture and the service-oriented architecture in Cloud Computing.
 Source: in.pinterest.com
Source: in.pinterest.com
Cloud infrastructure consists of servers storage devices network cloud management software deployment software and platform virtualization. Cloud Computing Architecture As we know cloud computing technology is used by both small and large organizations to store the information in cloud and access it from anywhere at anytime using the internet connection. It also offers development and deployment tools required to develop applications. This paper presents a treatise about cloud computing security risk and attack we explained the definition of cloud computing and the P2P network in. English Description Unleash the power of cloud.
 Source: tutorialspoint.com
Source: tutorialspoint.com
Front End Back End Each of the ends is connected through a network. An important aspect of your purchase decision is how the security. Of Computer Science Soka Ikeda College of Arts and Science for Women Chennai 2Assistant Professor Dept. In cloud computing low bandwidth does not meet the desired computing performance. Front End Back End Each of the ends is connected through a network.
This site is an open community for users to do sharing their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site adventageous, please support us by sharing this posts to your favorite social media accounts like Facebook, Instagram and so on or you can also save this blog page with the title security architecture design in cloud computing tutorialspoint by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.






