Your Security architecture design security issues in hardware images are available. Security architecture design security issues in hardware are a topic that is being searched for and liked by netizens now. You can Find and Download the Security architecture design security issues in hardware files here. Find and Download all free photos and vectors.
If you’re searching for security architecture design security issues in hardware pictures information related to the security architecture design security issues in hardware keyword, you have visit the ideal site. Our site always gives you suggestions for seeking the highest quality video and image content, please kindly surf and find more informative video articles and images that fit your interests.
Security Architecture Design Security Issues In Hardware. This document can be considered as the secure design guideline for the architects or as a checklist for penetration tester to perform application architecture review as a part of the overall security. Security challenges in automotive hardwaresoftware architecture design Abstract. Secure Cloud Business Flows June 2019 Functional Controls Functional Controls are common security considerations that are derived from the technical. Design for security Sphere.
 Why The Security Stack Has 10 Layers Not 7 Life Application Security Architecture Security From pinterest.com
Why The Security Stack Has 10 Layers Not 7 Life Application Security Architecture Security From pinterest.com
Google Twitter and others identify the most common software design mistakes – compiled from their own organizations – that lead to security woes and how to avoid them.
Secure Cloud Business Flows June 2019 Functional Controls Functional Controls are common security considerations that are derived from the technical. It is preferable to perform the architecture review at the design stage as the cost and effort required for implementing security after development is high. Security Architecture and Design is a three-part domain. This paper is an introduction to security challenges for the design of automotive hardwaresoftware architectures. Marko Wolf2 Alexandre Bouard3 William R. Swarup Bhunia Mark Tehranipoor in Hardware Security 2019151 Attack Vectors Attack vectorsas they relate to hardware security are means or paths for bad actors attackers to get access to hardware components for malicious purposes for example to compromise it or extract secret assets stored in hardware.
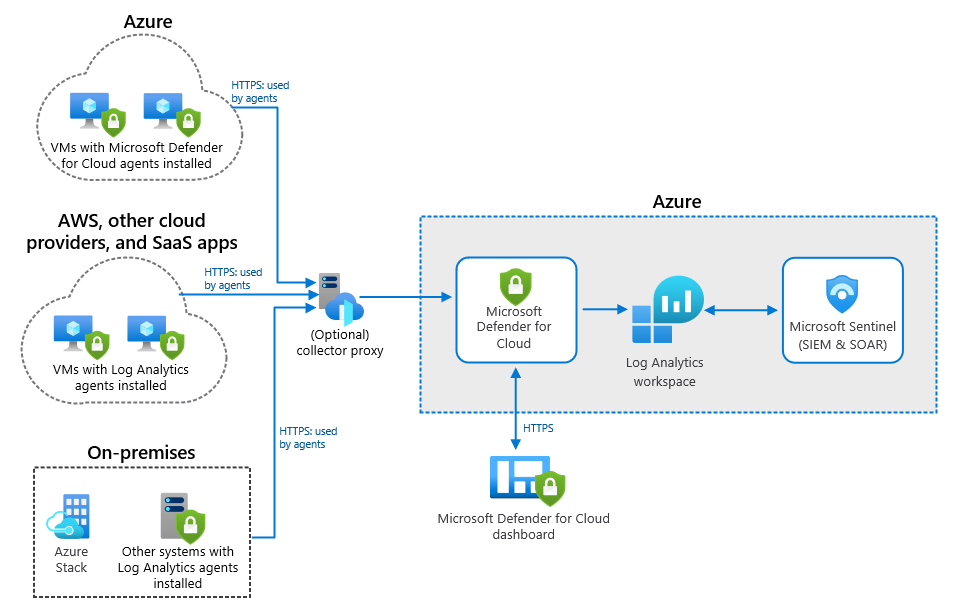 Source: docs.microsoft.com
Source: docs.microsoft.com
Security Design of the VMware Infrastructure 3 architecture by the department administrator within the boundaries assigned to the resource pool. VMware Infrastructure maintains a record of. This paper is an introduction to security challenges for the design of automotive hardwaresoftware architectures. Security Design of the VMware Infrastructure 3 architecture by the department administrator within the boundaries assigned to the resource pool. Network Architecture Security Issues and Hardware Implementation of a Home Area Network for Smart Grid Sergio Saponara 1 and Tony Bacchillone 1 1 Dipartimento Ingegneria.
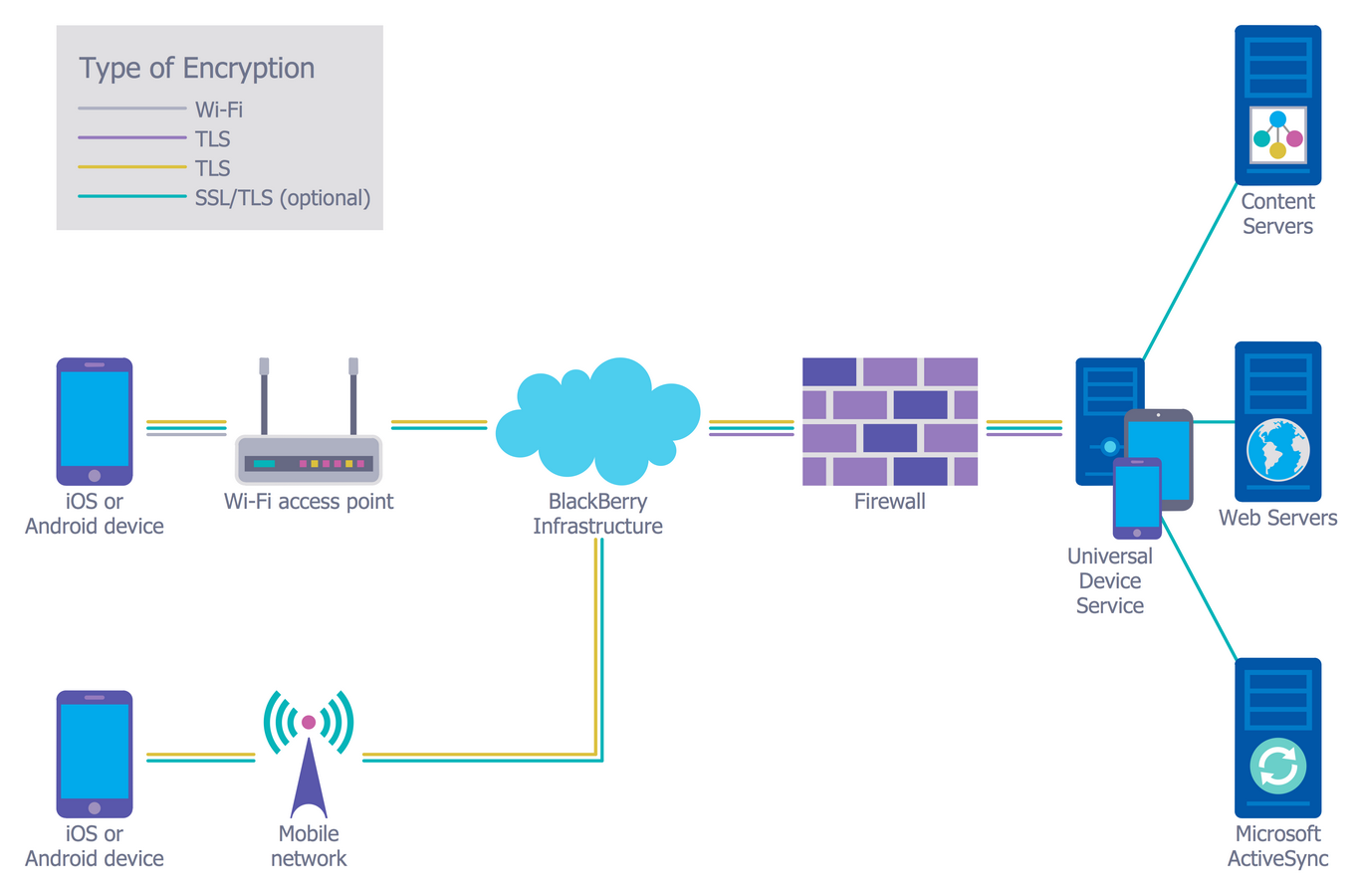 Source: conceptdraw.com
Source: conceptdraw.com
Swarup Bhunia Mark Tehranipoor in Hardware Security 2019151 Attack Vectors Attack vectorsas they relate to hardware security are means or paths for bad actors attackers to get access to hardware components for malicious purposes for example to compromise it or extract secret assets stored in hardware.
 Source: pinterest.com
Source: pinterest.com
The first part covers The first part covers the hardware and software required to have a secure computer system. The architecture is designed to ensure that the security policy and standards security architecture decisions and risk management are fully implemented and effective for a long period. Secure Cloud Business Flows June 2019 Functional Controls Functional Controls are common security considerations that are derived from the technical. Security Design of the VMware Infrastructure 3 architecture by the department administrator within the boundaries assigned to the resource pool.
 Source: pinterest.com
Source: pinterest.com
Counterfeiting design security obfuscation reverse engineering side-channel analysis Although a recognized if imperfectly executed issue in software design for security is an emerging topic in hardware. It is preferable to perform the architecture review at the design stage as the cost and effort required for implementing security after development is high. Network Architecture Security Issues and Hardware Implementation of a Home Area Network for Smart Grid Sergio Saponara 1 and Tony Bacchillone 1 1 Dipartimento Ingegneria. The cost plays crucial role ina any project.
 Source: pinterest.com
Source: pinterest.com
This paper is an introduction to security challenges for the design of automotive hardwaresoftware architectures. Enterprise information security architecture EISA is the practice of applying a comprehensive and rigorous method for describing a current andor future structure and behavior for an organizations security processes information security. Counterfeiting design security obfuscation reverse engineering side-channel analysis Although a recognized if imperfectly executed issue in software design for security is an emerging topic in hardware. As organizations build a robust security architecture their focus can gradually shift from remediation to a more proactive stance which is a theme also explored in the companion piece. Marko Wolf2 Alexandre Bouard3 William R.
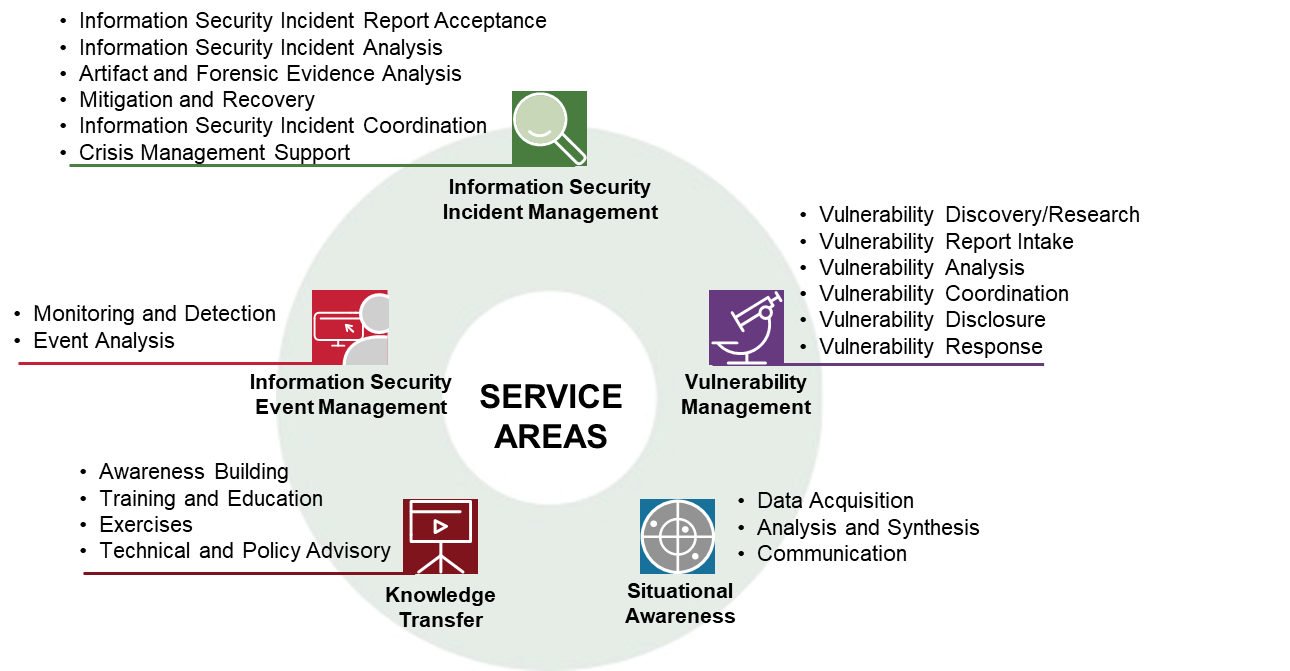 Source: first.org
Source: first.org
Counterfeiting design security obfuscation reverse engineering side-channel analysis Although a recognized if imperfectly executed issue in software design for security is an emerging topic in hardware. Enterprise information security architecture EISA is the practice of applying a comprehensive and rigorous method for describing a current andor future structure and behavior for an organizations security processes information security. Security Models and Architecture 187 All-In-One CISSP Certification All-in-One Exam Guide Harris 222966-7 Chapter 5 However before we dive into these concepts it is important to. This paper is an introduction to security challenges for the design of automotive hardwaresoftware architectures. Security Challenges in Automotive Hardware Software Architecture Design Florian Sagstetter 1 Martin Lukasiewycz Sebastian Steinhorst.
 Source: pinterest.com
Source: pinterest.com
Security challenges in automotive hardwaresoftware architecture design Abstract. In this spotlight article for the Security Architecture and Design domain I will discuss how security is architected and designed into software and hardware tools and technologies and then. The first part covers The first part covers the hardware and software required to have a secure computer system. In IoT hardware and unit prices are the main contributions to increase security and safety from one side and reduce. VMware Infrastructure maintains a record of.
 Source: ibm.com
Source: ibm.com
This paper is an introduction to security challenges for the design of automotive hardwaresoftware architectures. Counterfeiting design security obfuscation reverse engineering side-channel analysis Although a recognized if imperfectly executed issue in software design for security is an emerging topic in hardware. The first part covers The first part covers the hardware and software required to have a secure computer system. The architecture is designed to ensure that the security policy and standards security architecture decisions and risk management are fully implemented and effective for a long period.
 Source: in.pinterest.com
Source: in.pinterest.com
Network Architecture Security Issues and Hardware Implementation of a Home Area Network for Smart Grid Sergio Saponara 1 and Tony Bacchillone 1 1 Dipartimento Ingegneria. Swarup Bhunia Mark Tehranipoor in Hardware Security 2019151 Attack Vectors Attack vectorsas they relate to hardware security are means or paths for bad actors attackers to get access to hardware components for malicious purposes for example to compromise it or extract secret assets stored in hardware. The architecture is designed to ensure that the security policy and standards security architecture decisions and risk management are fully implemented and effective for a long period. Marko Wolf2 Alexandre Bouard3 William R. The first part covers The first part covers the hardware and software required to have a secure computer system.
 Source: br.pinterest.com
Source: br.pinterest.com
Google Twitter and others identify the most common software design mistakes – compiled from their own organizations – that lead to security woes and how to avoid them. Security Challenges in Automotive Hardware Software Architecture Design Florian Sagstetter 1 Martin Lukasiewycz Sebastian Steinhorst. Network Architecture Security Issues and Hardware Implementation of a Home Area Network for Smart Grid Sergio Saponara 1 and Tony Bacchillone 1 1 Dipartimento Ingegneria. Enterprise information security architecture EISA is the practice of applying a comprehensive and rigorous method for describing a current andor future structure and behavior for an organizations security processes information security. Marko Wolf2 Alexandre Bouard3 William R.
 Source: ibm.com
Source: ibm.com
Counterfeiting design security obfuscation reverse engineering side-channel analysis Although a recognized if imperfectly executed issue in software design for security is an emerging topic in hardware. Design for security Sphere. In IoT hardware and unit prices are the main contributions to increase security and safety from one side and reduce. VMware Infrastructure maintains a record of. Security Architecture and Design describes fundamental logical hardware operating system and software security components and how to use those components to design architect and evaluate.
 Source: sk.pinterest.com
Source: sk.pinterest.com
The first part covers The first part covers the hardware and software required to have a secure computer system. Security Architecture and Design describes fundamental logical hardware operating system and software security components and how to use those components to design architect and evaluate. The cost plays crucial role ina any project. Marko Wolf2 Alexandre Bouard3 William R. SAFE Architecture Guide 9 Places in the Network.
 Source: pinterest.com
Source: pinterest.com
Security Models and Architecture 187 All-In-One CISSP Certification All-in-One Exam Guide Harris 222966-7 Chapter 5 However before we dive into these concepts it is important to.
 Source: pinterest.com
Source: pinterest.com
Security Design of the VMware Infrastructure 3 architecture by the department administrator within the boundaries assigned to the resource pool. This paper is an introduction to security challenges for the design of automotive hardwaresoftware architectures. The cost plays crucial role ina any project. Enterprise information security architecture EISA is the practice of applying a comprehensive and rigorous method for describing a current andor future structure and behavior for an organizations security processes information security.
 Source: pinterest.com
Source: pinterest.com
Enterprise information security architecture EISA is the practice of applying a comprehensive and rigorous method for describing a current andor future structure and behavior for an organizations security processes information security.
 Source: pinterest.com
Source: pinterest.com
 Source: pinterest.com
Source: pinterest.com
The cost plays crucial role ina any project. Network Architecture Security Issues and Hardware Implementation of a Home Area Network for Smart Grid Sergio Saponara 1 and Tony Bacchillone 1 1 Dipartimento Ingegneria. The first part covers The first part covers the hardware and software required to have a secure computer system. Design for security Sphere. Security Challenges in Automotive Hardware Software Architecture Design Florian Sagstetter 1 Martin Lukasiewycz Sebastian Steinhorst.
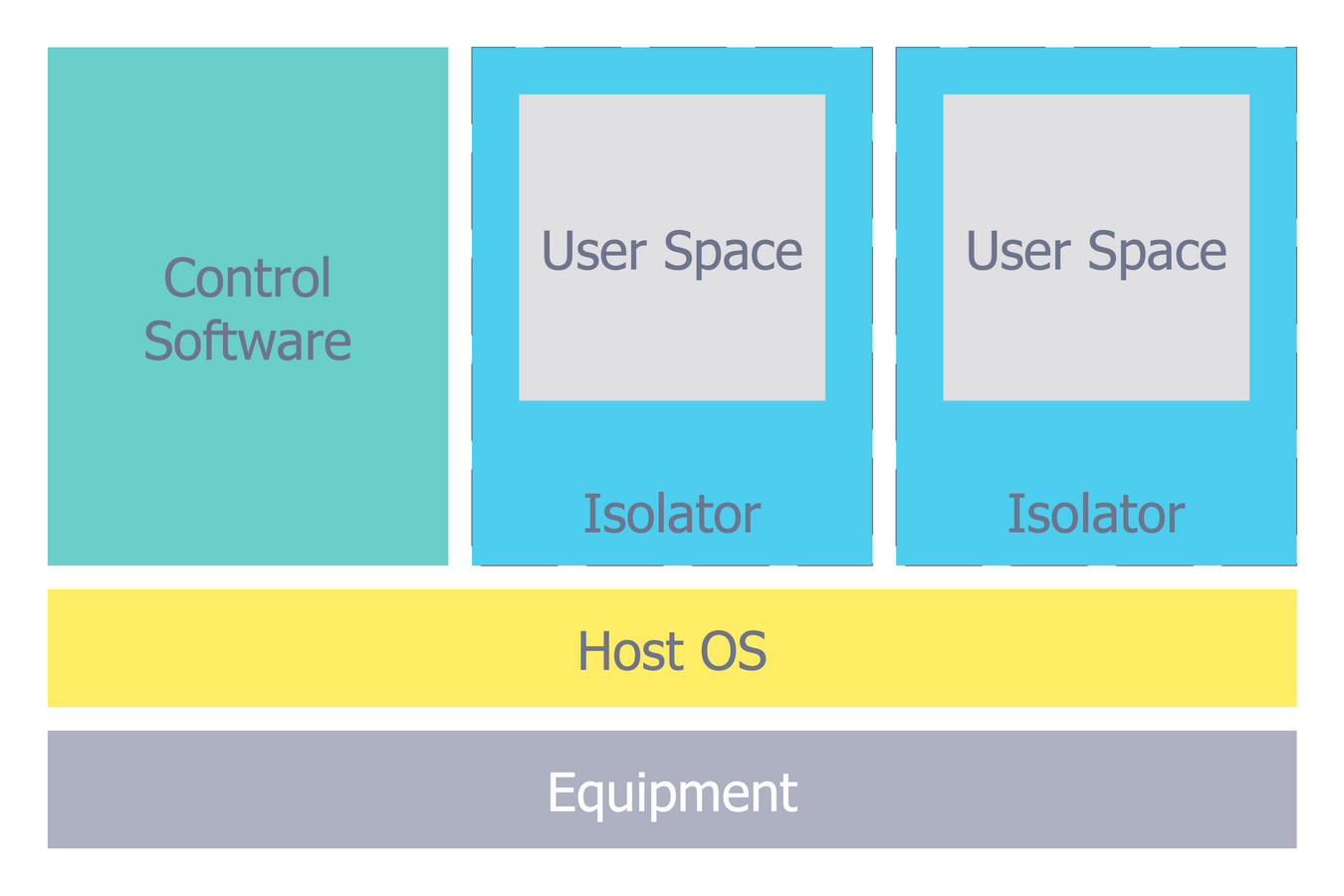 Source: conceptdraw.com
Source: conceptdraw.com
The cost plays crucial role ina any project. Security Challenges in Automotive Hardware Software Architecture Design Florian Sagstetter 1 Martin Lukasiewycz Sebastian Steinhorst. Counterfeiting design security obfuscation reverse engineering side-channel analysis Although a recognized if imperfectly executed issue in software design for security is an emerging topic in hardware. This paper is an introduction to security challenges for the design of automotive hardwaresoftware architectures. In this spotlight article for the Security Architecture and Design domain I will discuss how security is architected and designed into software and hardware tools and technologies and then.
This site is an open community for users to do sharing their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site serviceableness, please support us by sharing this posts to your preference social media accounts like Facebook, Instagram and so on or you can also save this blog page with the title security architecture design security issues in hardware by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.






