Your Security operation center architecture design images are ready in this website. Security operation center architecture design are a topic that is being searched for and liked by netizens now. You can Find and Download the Security operation center architecture design files here. Find and Download all free photos.
If you’re looking for security operation center architecture design images information connected with to the security operation center architecture design interest, you have come to the ideal site. Our website always gives you hints for downloading the highest quality video and picture content, please kindly search and find more enlightening video content and graphics that match your interests.
Security Operation Center Architecture Design. The overall architecture of a VSOC including assets threat detection threat feeds and products used within it The data feeds that power the SOC from the OT and IT networks. An Integrated Security Operations Center ISOC is designed to collect integrate and analyze alarms and logs from these traditionally siloed organizations providing much greater situational awareness to a utilitys security team. SOC Conceptual Architecture. By design a SOCs operational processes are intended to be formally structured regular and repeatable.
 Octa Transit Security And Operations Center This Is A Command Center To Be Built In Oc Cali I Used 3d Max Vray On T Design Command Center Project Management From pinterest.com
Octa Transit Security And Operations Center This Is A Command Center To Be Built In Oc Cali I Used 3d Max Vray On T Design Command Center Project Management From pinterest.com
A SOC is expected to contain several areas including an operational room a war room and the supervisors offices. An SOC within a building or facility is a central location from where staff supervises the site using data processing technology. Security operations centers must be architected for intelligence embracing an adaptive security architecture to become context-aware and intelligence-driven. These principles support these three key strategies and describe a securely architected system hosted on cloud or on-premises datacenters or a combination of both. The 2020s edition aims is to design a Emergency Operation Center to. Building a Security Operations Center Author Josh Pyorre Keywords Defcon DEF CON HackerSecurity Conference PresentationsTechnologyPhreakingLockpickinghackersinfosecHardware HackingExploit Defcon 18 71.
Defines design thumb rules and parameters for SOC Design.
We propose a reference conceptual architecture in Figure 2-13. Building an efficient security operations center SOC requires organizing internal resources in a way that improves communication and increases efficiencies. We propose a reference conceptual architecture in Figure 2-13. Security Operations sometimes referred to as a Security Operations Center SOC has a critical role to play in limiting the time and access an attacker can get to valuable systems and data. Event generators event collectors message database analysis engines and reaction management software. There are a lot of things to consider.
 Source: docs.microsoft.com
Source: docs.microsoft.com
A SOC is expected to contain several areas including an operational room a war room and the supervisors offices. The second part covers the logical models required to keep the system secure and the third part covers evaluation models that quantify how secure the system really is. SOC Conceptual Architecture. There are a lot of things to consider. The first part covers the hardware and software required to have a secure computer system.
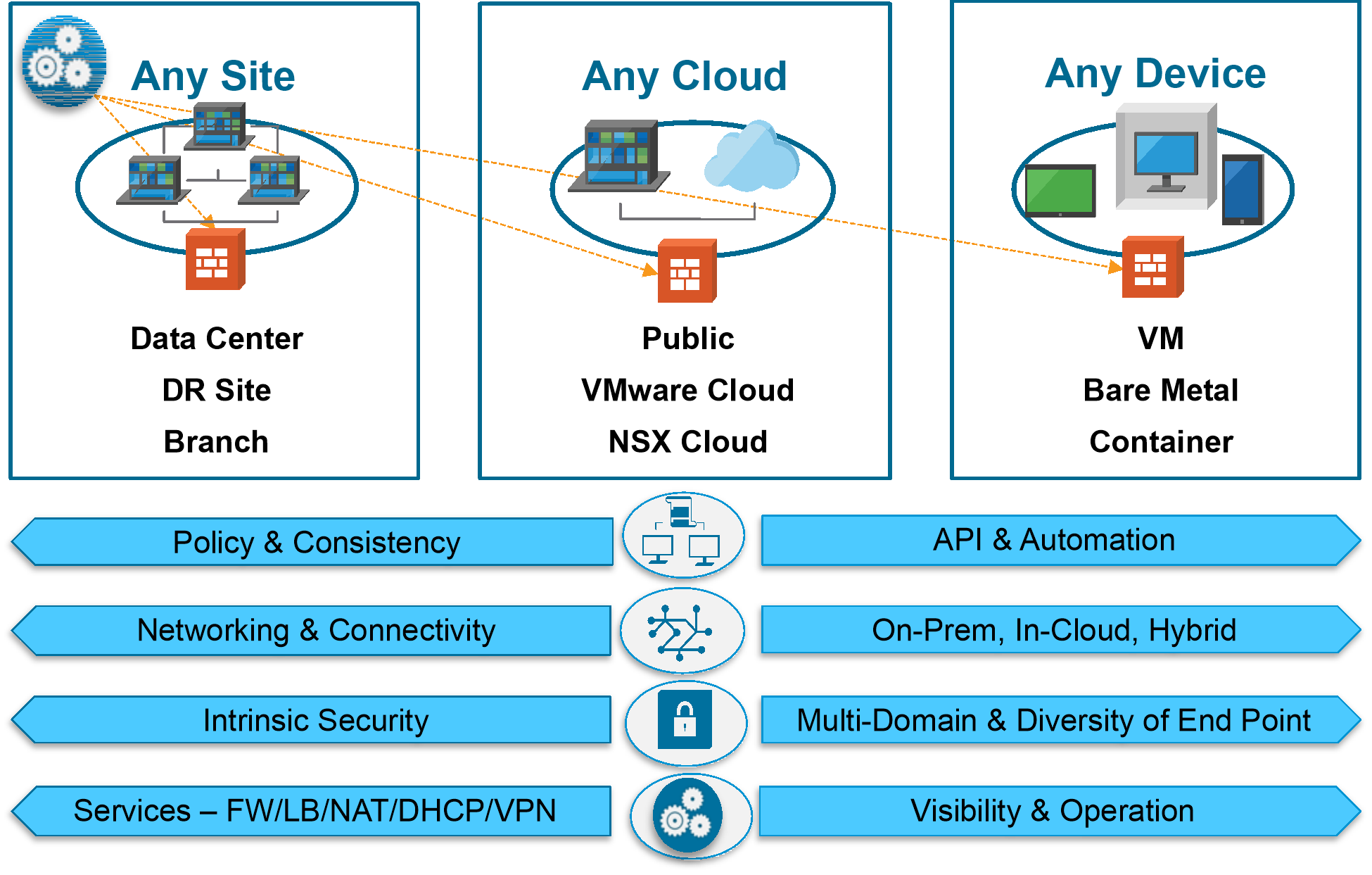 Source: nsx.techzone.vmware.com
Source: nsx.techzone.vmware.com
Kaira Looro is an international architecture competition open to students and young architect. The overall architecture of a VSOC including assets threat detection threat feeds and products used within it The data feeds that power the SOC from the OT and IT networks. Application of these principles will dramatically increase the likelihood your security architecture will maintain assurances of confidentiality integrity and availability. The first part covers the hardware and software required to have a secure computer system. Security Operations sometimes referred to as a Security Operations Center SOC has a critical role to play in limiting the time and access an attacker can get to valuable systems and data.
 Source: slidetodoc.com
Source: slidetodoc.com
SOCs have been typically built around a hub-and-spoke architecture where a security information and event management SIEM system aggregates and correlates data from security feeds. The architecture should formalize the operation model of SOC in terms of components and relationships. Security Operation Center - Design Build. Defines design thumb rules and parameters for SOC Design. Each minute that an attacker has in the environment allows them to continue to conduct attack operations and access sensitivevaluable systems.
 Source: pinterest.com
Source: pinterest.com
By design a SOCs operational processes are intended to be formally structured regular and repeatable. Event generators event collectors message database analysis engines and reaction management software. Security Architecture and Design is a three-part domain. Security Operations sometimes referred to as a Security Operations Center SOC has a critical role to play in limiting the time and access an attacker can get to valuable systems and data. SOC Conceptual Architecture.
 Source: pinterest.com
Source: pinterest.com
Event generators event collectors message database analysis engines and reaction management software. The first part covers the hardware and software required to have a secure computer system. Security Operation Center - Design Build. Defines design thumb rules and parameters for SOC Design. We propose a reference conceptual architecture in Figure 2-13.
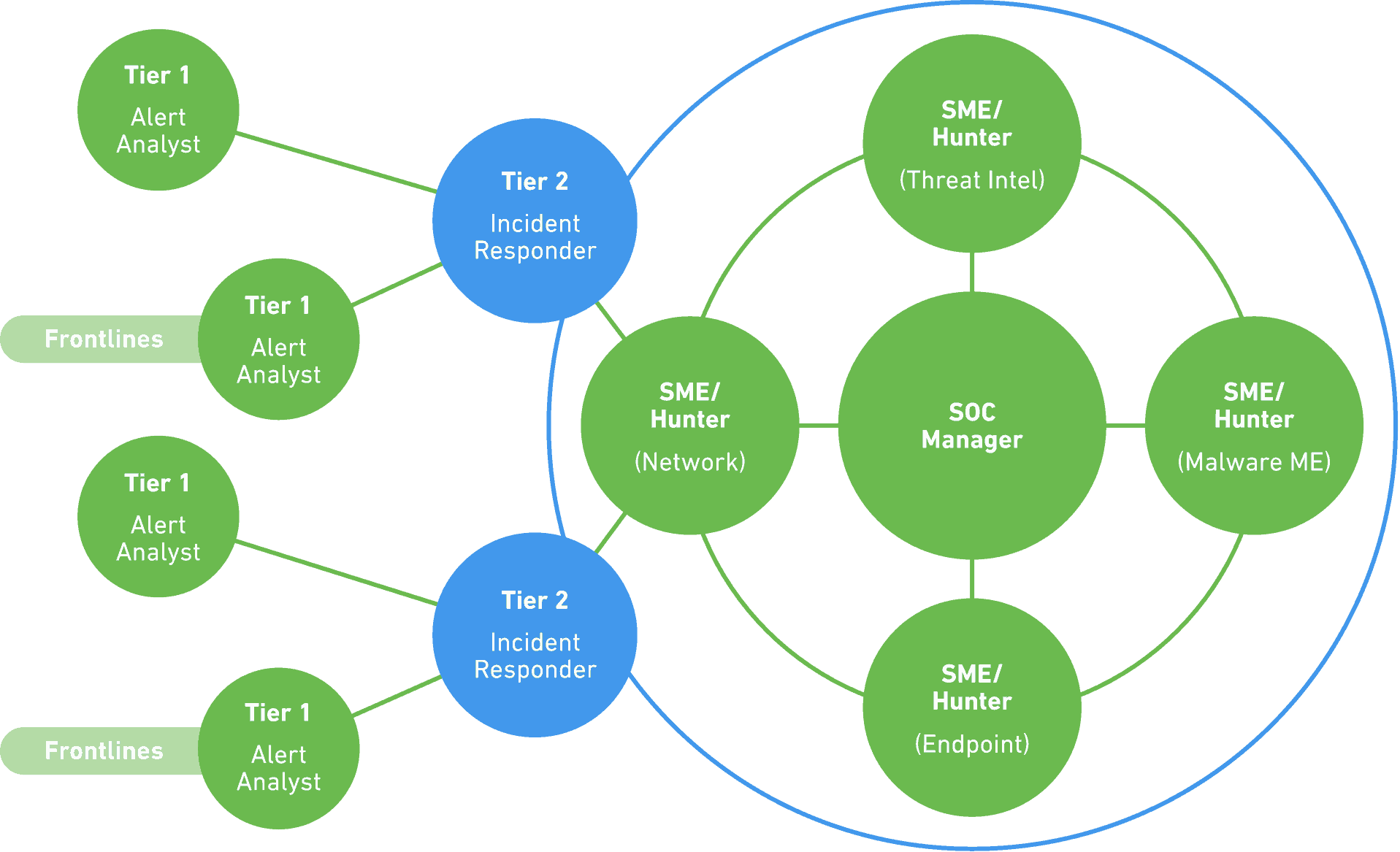 Source: exabeam.com
Source: exabeam.com
Building a Security Operations Center Author Josh Pyorre Keywords Defcon DEF CON HackerSecurity Conference PresentationsTechnologyPhreakingLockpickinghackersinfosecHardware HackingExploit Defcon 18 71. Thus the vast majority of todays SOCs are built according to patterns that are highly amenable to automation. A Security Operation Center SOC is made up of five distinct modules. SOCs have been typically built around a hub-and-spoke architecture where a security information and event management SIEM system aggregates and correlates data from security feeds. Operation center infrastructure This is where we are going to spend most of our time in this chapter.
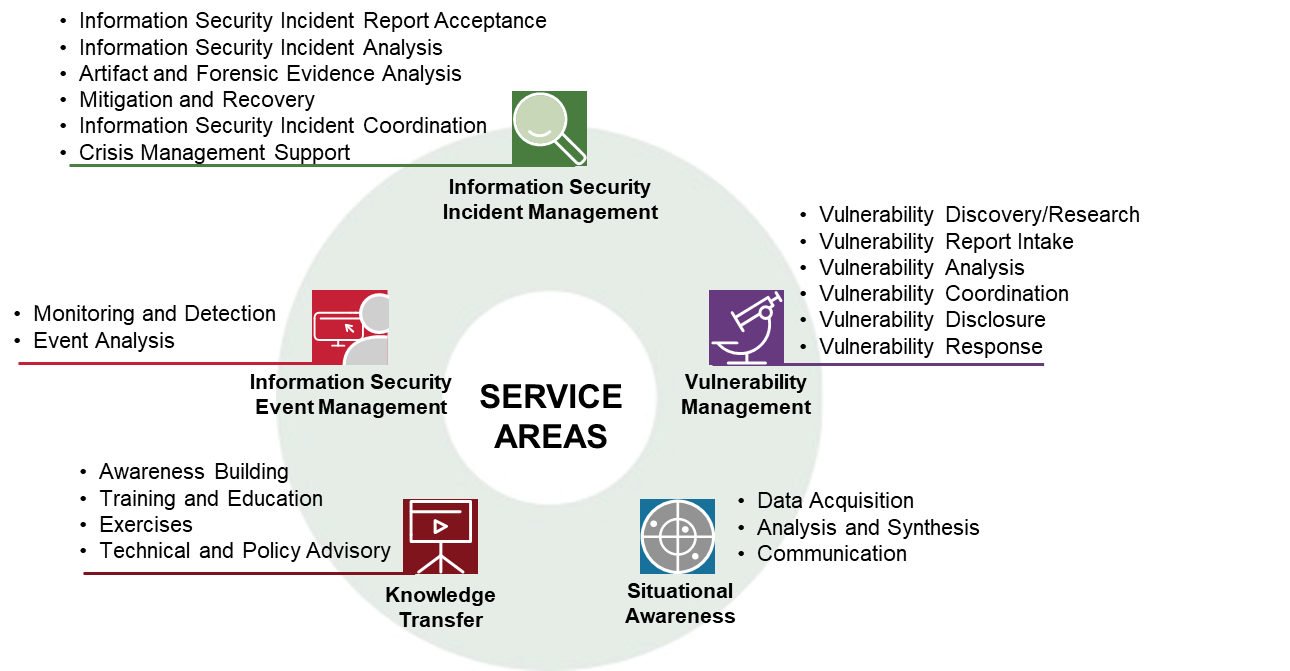 Source: first.org
Source: first.org
Security Operation Center - Design Build. A Security Operations Center is a highly skilled team following defined definitions and processes to manage threats and reduce security risk Security Operations Centers SOC are designed to. Security operations centers must be architected for intelligence embracing an adaptive security architecture to become context-aware and intelligence-driven. Event generators event collectors message database analysis engines and reaction management software. These principles support these three key strategies and describe a securely architected system hosted on cloud or on-premises datacenters or a combination of both.
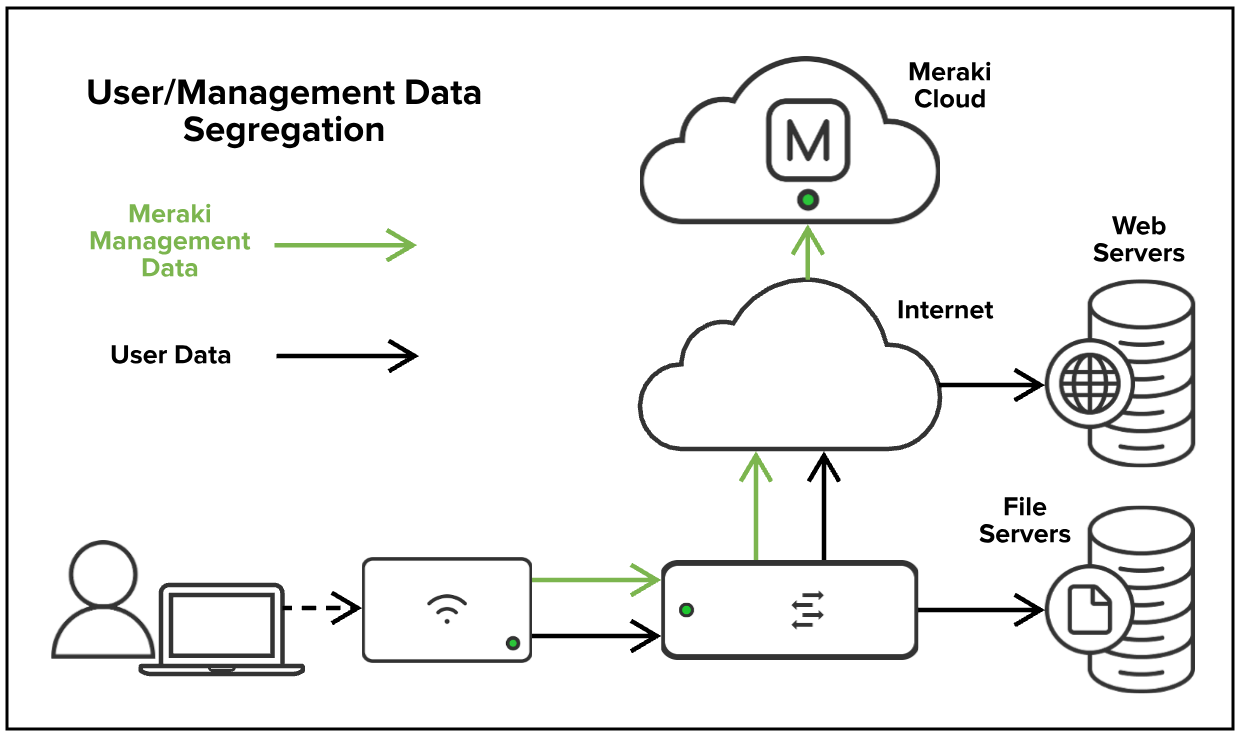 Source: documentation.meraki.com
Source: documentation.meraki.com
Application of these principles will dramatically increase the likelihood your security architecture will maintain assurances of confidentiality integrity and availability. Summarize the design and build approach for SOC Security Operation Center for both end user company and service providers. Security Architecture and Design is a three-part domain. Defines design thumb rules and parameters for SOC Design. Building an efficient security operations center SOC requires organizing internal resources in a way that improves communication and increases efficiencies.
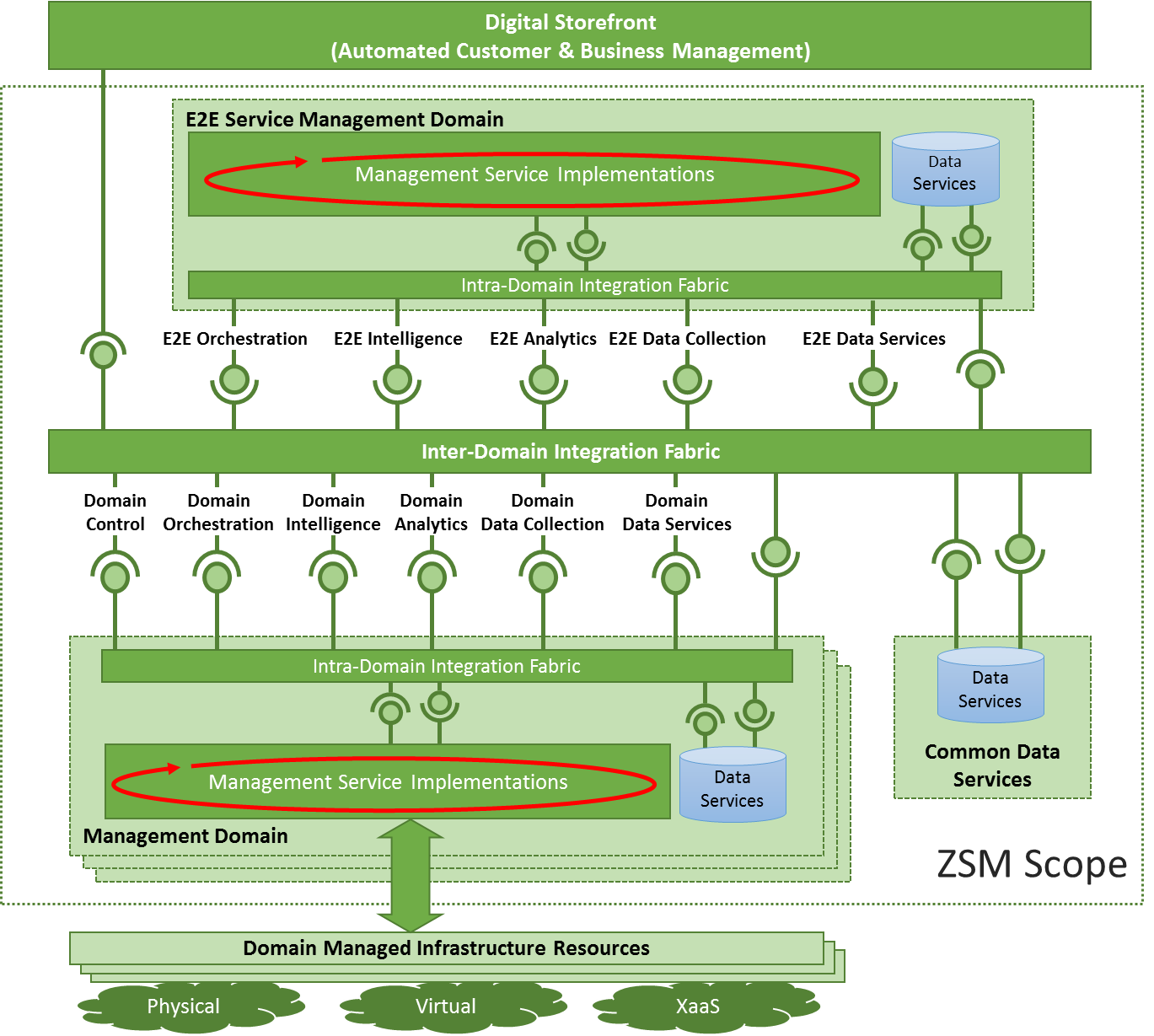 Source: etsi.org
Source: etsi.org
We propose a reference conceptual architecture in Figure 2-13. Building an efficient security operations center SOC requires organizing internal resources in a way that improves communication and increases efficiencies. A SOC is expected to contain several areas including an operational room a war room and the supervisors offices. Summarize the design and build approach for SOC Security Operation Center for both end user company and service providers. Thus the vast majority of todays SOCs are built according to patterns that are highly amenable to automation.
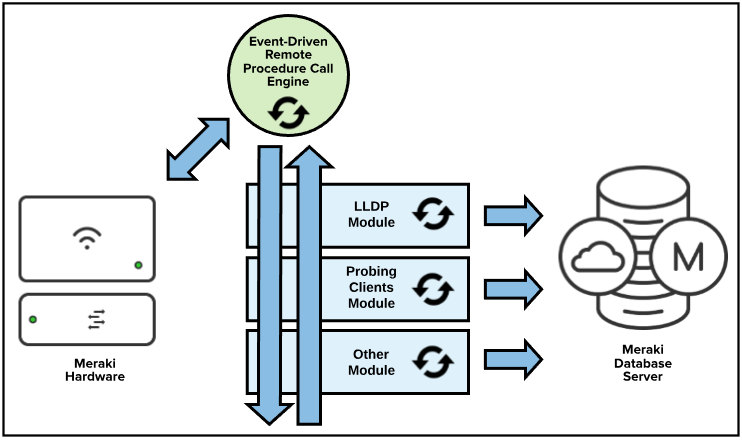 Source: documentation.meraki.com
Source: documentation.meraki.com
A Security Operation Center SOC is made up of five distinct modules. An Integrated Security Operations Center ISOC is designed to collect integrate and analyze alarms and logs from these traditionally siloed organizations providing much greater situational awareness to a utilitys security team. Security operations centers must be architected for intelligence embracing an adaptive security architecture to become context-aware and intelligence-driven. The 2020s edition aims is to design a Emergency Operation Center to. Security Operations sometimes referred to as a Security Operations Center SOC has a critical role to play in limiting the time and access an attacker can get to valuable systems and data.
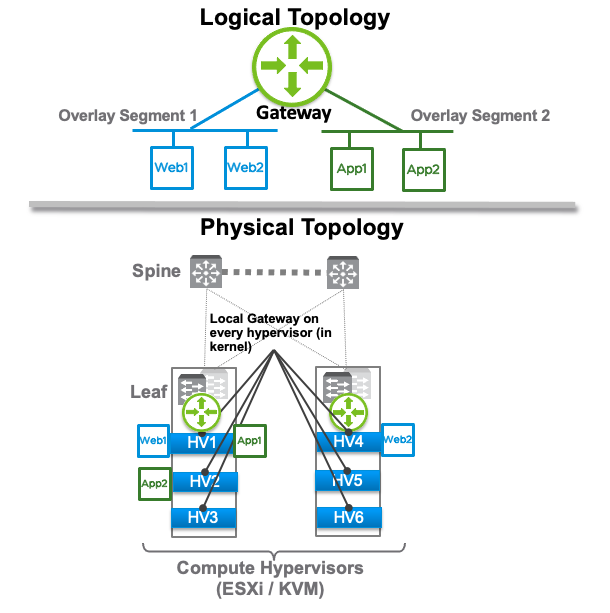 Source: nsx.techzone.vmware.com
Source: nsx.techzone.vmware.com
There are a lot of things to consider. The first part covers the hardware and software required to have a secure computer system. An SOC within a building or facility is a central location from where staff supervises the site using data processing technology. Thus the vast majority of todays SOCs are built according to patterns that are highly amenable to automation. SOC Conceptual Architecture.
 Source: pinterest.com
Source: pinterest.com
A Security Operations Center is a highly skilled team following defined definitions and processes to manage threats and reduce security risk Security Operations Centers SOC are designed to. Infrastructure needed to support your SOC is vital to your organizations security success. We propose a reference conceptual architecture in Figure 2-13. Security Operation Center - Design Build. To get the best out of your investment you should operate the various SOC technologies under a cohesive architecture.
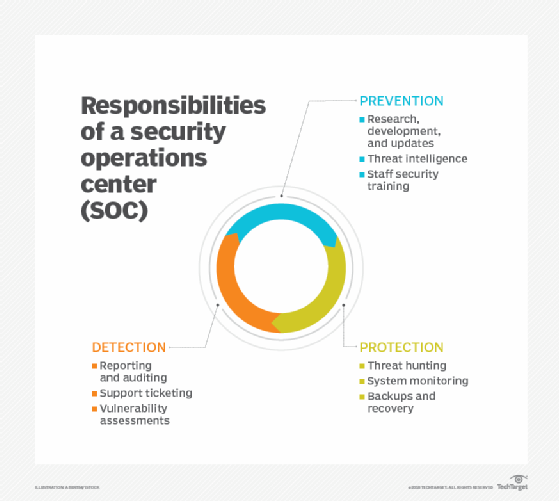 Source: searchsecurity.techtarget.com
Source: searchsecurity.techtarget.com
The architecture should formalize the operation model of SOC in terms of components and relationships. Building a Security Operations Center Author Josh Pyorre Keywords Defcon DEF CON HackerSecurity Conference PresentationsTechnologyPhreakingLockpickinghackersinfosecHardware HackingExploit Defcon 18 71. By design a SOCs operational processes are intended to be formally structured regular and repeatable. In this excerpt of Designing and Building Security Operations Center author David Nathans reviews the infrastructure needed to support a SOC and maintain SOC security. Security Architecture and Design is a three-part domain.

VMware Validated Design Architecture and Design is intended for cloud architects infrastructure administrators and cloud administrators who are familiar with and want to use VMware software to deploy in a short time and manage an SDDC that meets the requirements for capacity. We propose a reference conceptual architecture in Figure 2-13. These principles support these three key strategies and describe a securely architected system hosted on cloud or on-premises datacenters or a combination of both. Infrastructure needed to support your SOC is vital to your organizations security success. To get the best out of your investment you should operate the various SOC technologies under a cohesive architecture.
 Source: pinterest.com
Source: pinterest.com
Kaira Looro is an international architecture competition open to students and young architect. Security Operations sometimes referred to as a Security Operations Center SOC has a critical role to play in limiting the time and access an attacker can get to valuable systems and data. Infrastructure needed to support your SOC is vital to your organizations security success. The overall architecture of a VSOC including assets threat detection threat feeds and products used within it The data feeds that power the SOC from the OT and IT networks. Thus the vast majority of todays SOCs are built according to patterns that are highly amenable to automation.
 Source: pinterest.com
Source: pinterest.com
There are a lot of things to consider. Security operations centers must be architected for intelligence embracing an adaptive security architecture to become context-aware and intelligence-driven. SOC Conceptual Architecture. Event generators event collectors message database analysis engines and reaction management software. Security Operation Center - Design Build.
 Source: pinterest.com
Source: pinterest.com
Security Architecture and Design is a three-part domain. Security operations centers must be architected for intelligence embracing an adaptive security architecture to become context-aware and intelligence-driven. The second part covers the logical models required to keep the system secure and the third part covers evaluation models that quantify how secure the system really is. Kaira Looro is an international architecture competition open to students and young architect. A security operations center SOC is a centralized unit in an organization that deals with security issues on an organizational and technical level.
 Source: pinterest.com
Source: pinterest.com
Defines design thumb rules and parameters for SOC Design. Spokes of this model can incorporate a. Infrastructure needed to support your SOC is vital to your organizations security success. Kaira Looro is an international architecture competition open to students and young architect. Summarize the design and build approach for SOC Security Operation Center for both end user company and service providers.
This site is an open community for users to share their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site adventageous, please support us by sharing this posts to your favorite social media accounts like Facebook, Instagram and so on or you can also save this blog page with the title security operation center architecture design by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.






