Your Without security operation center architecture design images are ready. Without security operation center architecture design are a topic that is being searched for and liked by netizens today. You can Download the Without security operation center architecture design files here. Download all free images.
If you’re searching for without security operation center architecture design images information related to the without security operation center architecture design interest, you have visit the ideal site. Our site frequently gives you suggestions for seeing the highest quality video and picture content, please kindly surf and locate more enlightening video content and graphics that fit your interests.
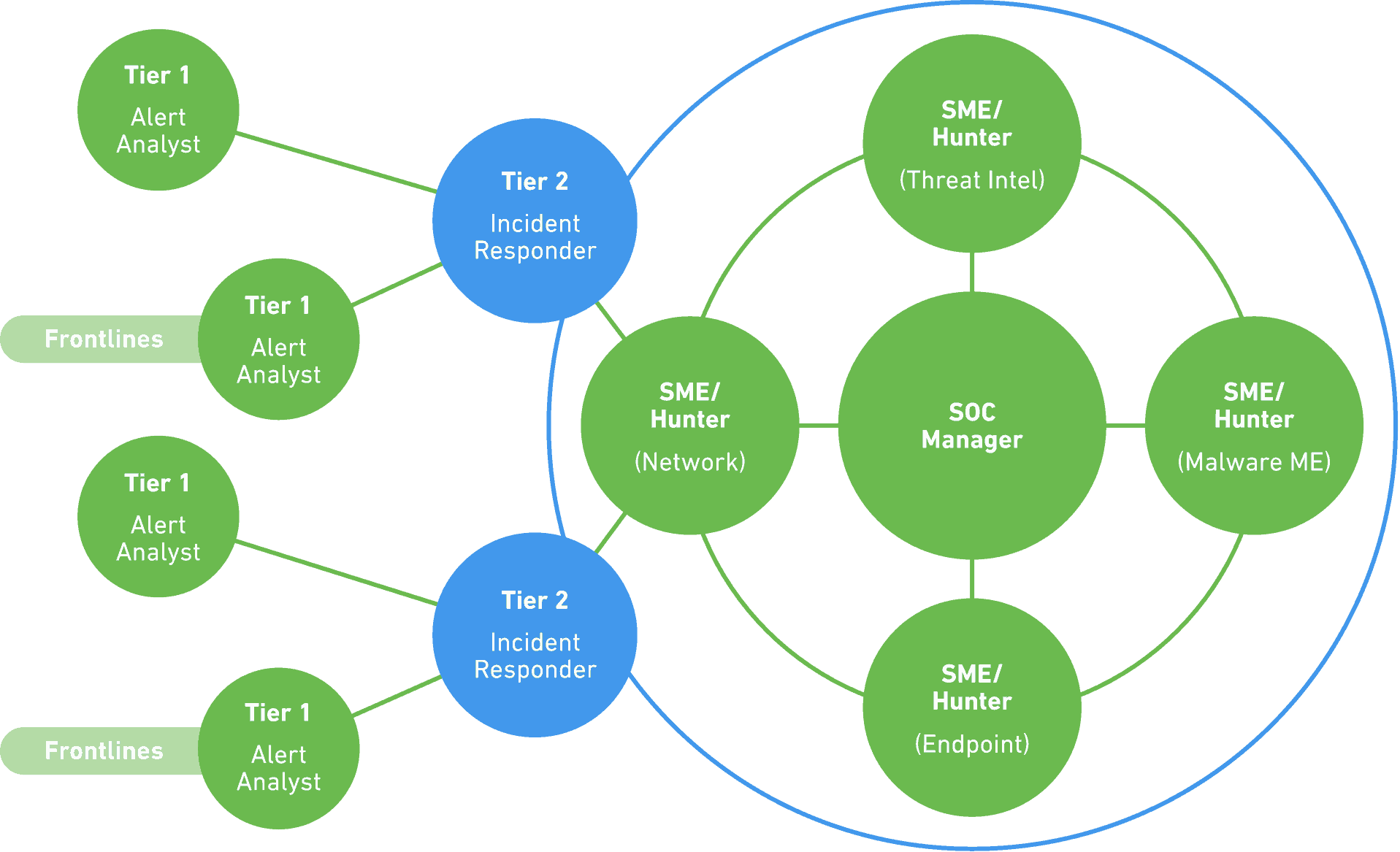
Without Security Operation Center Architecture Design. Adding to a former post When to Set Up a Security Operations Center were now offering a framework for organizing the three key functions of a SOC. SECURITY OPERATION CENTER - Models Strategies and development - By Ali Mohammadi Desember 1213 2017 1 Outline 2 Organizational Security Concept Security Operations Center SOC Concept SOC Models. A Security Operation Center SOC is made up of five distinct modules. A SOC is expected to contain several areas including an operational room a war room and the supervisors offices.
 Centralized Security Properly Planned Socs Help Mitigate Cyber Risks Security Room Office Interior Design Home Office Setup From pinterest.com
Centralized Security Properly Planned Socs Help Mitigate Cyber Risks Security Room Office Interior Design Home Office Setup From pinterest.com
Azure Role-based access control. The 2020s edition aims is to design a Emergency Operation Center to. SECURITY OPERATION CENTER - Models Strategies and development - By Ali Mohammadi Desember 1213 2017 1 Outline 2 Organizational Security Concept Security Operations Center SOC Concept SOC Models. Each minute that an attacker has in the. SEC545 offers an in-depth breakdown of security controls services and architecture models for public cloud environments. Without the words where my words occur anywhere in the article in the title of the article Return articles authored by eg PJ Hayes or McCarthy Return articles published in.
People process and technology.
SEC545 offers an in-depth breakdown of security controls services and architecture models for public cloud environments. The overarching rule in data center facilities is to design for flexibility and scalability. This rule embraces several key principles in the site location building selection floor layout electrical system design mechanical design and. Data center foundation data center services and user services. Event generators event collectors message database analysis engines. Design Overview The data center architecture consists of three primary modular layers with hierarchical interdependencies.
 Source: pinterest.com
Source: pinterest.com
A Security Operation Center SOC is made up of five distinct modules. The reference architecture building-block approach uses common components to minimize support costs and deployment risks. Event generators event collectors message database analysis engines. Security Operations sometimes referred to as a Security Operations Center SOC has a critical role to play in limiting the time and access an attacker can get to valuable systems and data. Design that can be easily adapted to specific environments and customer requirements.
 Source: in.pinterest.com
Source: in.pinterest.com
These design patterns are useful for building reliable scalable secure applications in the cloud. A SOC is expected to contain several areas including an operational room a war room and the supervisors offices. These design patterns are useful for building reliable scalable secure applications in the cloud. The 2020s edition aims is to design a Emergency Operation Center to. This rule embraces several key principles in the site location building selection floor layout electrical system design mechanical design and.
 Source: exabeam.com
Source: exabeam.com
Operation center infrastructure This is where we are going to spend most of our time in this chapter. One best practice is for organizations to create a plan to optimize operations so everybody is in line with the security strategy. Azure Role-based access control. The overarching rule in data center facilities is to design for flexibility and scalability. A Security Operation Center SOC is made up of five distinct modules.
 Source: pinterest.com
Source: pinterest.com
A Security Operation Center SOC is made up of five distinct modules. IDSes are systems placed on either the host or the network to detect potentially malicious or unwanted activity that warrants further attention by the SOC analyst. Security Operations sometimes referred to as a Security Operations Center SOC has a critical role to play in limiting the time and access an attacker can get to valuable systems and data. Adding to a former post When to Set Up a Security Operations Center were now offering a framework for organizing the three key functions of a SOC. Security operations center processes and procedures Without a SOC security tasks are often assigned ad-hoc with no streamlined procedures.
 Source: pinterest.com
Source: pinterest.com
Without the words where my words occur anywhere in the article in the title of the article Return articles authored by eg PJ Hayes or McCarthy Return articles published in. Among the many security-relevant data feeds a Security Operations Center is likely to ingest the most prominent are often IDSes. We cover brokering and security-as-a-service to help better secure SaaS access containers and PaaS architecture and security considerations and the entire spectrum of IaaS security offerings and capabilities. The overarching rule in data center facilities is to design for flexibility and scalability. Azure Role-based access control.
 Source: in.pinterest.com
Source: in.pinterest.com
Figure 1 illustrates the data center 2196. Operation center infrastructure This is where we are going to spend most of our time in this chapter. This 2019 edition of the SANS Security Operations Center SOC Survey was designed to provide objective data to security leaders and practitioners who are looking to establish a SOC or optimize their existing SOCs. Building an effective security operations center SOC requires organizing internal resources in a way that improves communication and increases efficiencies. Security Operations sometimes referred to as a Security Operations Center SOC has a critical role to play in limiting the time and access an attacker can get to valuable systems and data.
 Source: pinterest.com
Source: pinterest.com
A SOC is expected to contain several areas including an operational room a war room and the supervisors offices. Each minute that an attacker has in the. We cover brokering and security-as-a-service to help better secure SaaS access containers and PaaS architecture and security considerations and the entire spectrum of IaaS security offerings and capabilities. Building an effective security operations center SOC requires organizing internal resources in a way that improves communication and increases efficiencies. SECURITY OPERATION CENTER - Models Strategies and development - By Ali Mohammadi Desember 1213 2017 1 Outline 2 Organizational Security Concept Security Operations Center SOC Concept SOC Models.
 Source: pinterest.com
Source: pinterest.com
Building an efficient security operations center SOC requires organizing internal resources in a way that improves communication and increases efficiencies. Building an effective security operations center SOC requires organizing internal resources in a way that improves communication and increases efficiencies. One best practice is for organizations to create a plan to optimize operations so everybody is in line with the security strategy. Operation center infrastructure This is where we are going to spend most of our time in this chapter. Chapter Description This chapter from Security Operations Center.
 Source: pinterest.com
Source: pinterest.com
The 2020s edition aims is to design a Emergency Operation Center to. Among the many security-relevant data feeds a Security Operations Center is likely to ingest the most prominent are often IDSes. The 2020s edition aims is to design a Emergency Operation Center to. SECURITY OPERATION CENTER - Models Strategies and development - By Ali Mohammadi Desember 1213 2017 1 Outline 2 Organizational Security Concept Security Operations Center SOC Concept SOC Models. Adding to a former post When to Set Up a Security Operations Center were now offering a framework for organizing the three key functions of a SOC.
 Source: pinterest.com
Source: pinterest.com
Without the words where my words occur anywhere in the article in the title of the article Return articles authored by eg PJ Hayes or McCarthy Return articles published in. Among the many security-relevant data feeds a Security Operations Center is likely to ingest the most prominent are often IDSes. Event generators event collectors message database analysis engines. The reference architecture building-block approach uses common components to minimize support costs and deployment risks. These design patterns are useful for building reliable scalable secure applications in the cloud.
 Source: pinterest.com
Source: pinterest.com
We cover brokering and security-as-a-service to help better secure SaaS access containers and PaaS architecture and security considerations and the entire spectrum of IaaS security offerings and capabilities. The 2020s edition aims is to design a Emergency Operation Center to. People process and technology. Security Refinement and Improvement Cybercriminals are constantly refining their tools and tacticsand in order to stay ahead of them the SOC needs to implement improvements on a continuous basis. Building an efficient security operations center SOC requires organizing internal resources in a way that improves communication and increases efficiencies.
 Source: pinterest.com
Source: pinterest.com
Kaira Looro is an international architecture competition open to students and young architect. Security operations center processes and procedures Without a SOC security tasks are often assigned ad-hoc with no streamlined procedures. The reference architecture building-block approach uses common components to minimize support costs and deployment risks. Without the words where my words occur anywhere in the article in the title of the article Return articles authored by eg PJ Hayes or McCarthy Return articles published in. Design that can be easily adapted to specific environments and customer requirements.
 Source: in.pinterest.com
Source: in.pinterest.com
Kaira Looro is an international architecture competition open to students and young architect. Among the many security-relevant data feeds a Security Operations Center is likely to ingest the most prominent are often IDSes. One best practice is for organizations to create a plan to optimize operations so everybody is in line with the security strategy. Chapter Description This chapter from Security Operations Center. Each pattern describes the problem that the pattern addresses considerations for applying the pattern and an example based on Microsoft Azure.
 Source: pinterest.com
Source: pinterest.com
The 2020s edition aims is to design a Emergency Operation Center to. The reference architecture building-block approach uses common components to minimize support costs and deployment risks. IDSes are systems placed on either the host or the network to detect potentially malicious or unwanted activity that warrants further attention by the SOC analyst. The overarching rule in data center facilities is to design for flexibility and scalability. SECURITY OPERATION CENTER - Models Strategies and development - By Ali Mohammadi Desember 1213 2017 1 Outline 2 Organizational Security Concept Security Operations Center SOC Concept SOC Models.
 Source: pinterest.com
Source: pinterest.com
Design Overview The data center architecture consists of three primary modular layers with hierarchical interdependencies. SECURITY OPERATION CENTER - Models Strategies and development - By Ali Mohammadi Desember 1213 2017 1 Outline 2 Organizational Security Concept Security Operations Center SOC Concept SOC Models. Among the many security-relevant data feeds a Security Operations Center is likely to ingest the most prominent are often IDSes. The 2020s edition aims is to design a Emergency Operation Center to. Security Operations sometimes referred to as a Security Operations Center SOC has a critical role to play in limiting the time and access an attacker can get to valuable systems and data.
 Source: pinterest.com
Source: pinterest.com
Security Refinement and Improvement Cybercriminals are constantly refining their tools and tacticsand in order to stay ahead of them the SOC needs to implement improvements on a continuous basis. A Security Operation Center SOC is made up of five distinct modules. The 2020s edition aims is to design a Emergency Operation Center to. SEC545 offers an in-depth breakdown of security controls services and architecture models for public cloud environments. Adding to a former post When to Set Up a Security Operations Center were now offering a framework for organizing the three key functions of a SOC.
 Source: pinterest.com
Source: pinterest.com
One best practice is for organizations to create a plan to optimize operations so everybody is in line with the security strategy. Building an efficient security operations center SOC requires organizing internal resources in a way that improves communication and increases efficiencies. The 2020s edition aims is to design a Emergency Operation Center to. Each minute that an attacker has in the. Figure 1 illustrates the data center 2196.
 Source: slideteam.net
Source: slideteam.net
There are a lot of things to consider. There are a lot of things to consider. Security Operations sometimes referred to as a Security Operations Center SOC has a critical role to play in limiting the time and access an attacker can get to valuable systems and data. Security Refinement and Improvement Cybercriminals are constantly refining their tools and tacticsand in order to stay ahead of them the SOC needs to implement improvements on a continuous basis. Security operations center processes and procedures Without a SOC security tasks are often assigned ad-hoc with no streamlined procedures.
This site is an open community for users to share their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site serviceableness, please support us by sharing this posts to your preference social media accounts like Facebook, Instagram and so on or you can also save this blog page with the title without security operation center architecture design by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.






